Suicide Awareness and Prevention
Suicide, suicide attempts, risk factors, protective factors, and how to effectively intervene in order to prevent loss of life to suicide.
1 views • 15 slides
Youth Risk Behavior in Louisiana Schools
Louisiana student behaviors from YRBSS data include carrying guns, fights, bullying, and suicide attempts. Student perspectives on mental health importance in creating safe school environments. Efforts to promote resources for better mental health access and support. Popular
2 views • 29 slides
MRCGP Applied Knowledge Test
The MRCGP Applied Knowledge Test (AKT) assesses the knowledge base needed for UK general practice, focusing on critical interpretation and application of information. The test comprises 200 multiple-choice questions with no negative marking, lasting 190 minutes and offered four times a year. Rules d
0 views • 73 slides
Reform Efforts in the Ottoman Empire: 18th and 19th Century Transformations
The Ottoman Empire underwent a series of reforms from the late 18th to the 19th century, aiming to centralize power, boost revenues, strengthen the military, educate bureaucrats, refine legal systems, and improve healthcare. Factors driving these reforms included military weaknesses, separatist nati
0 views • 19 slides
Mirai Botnet
The Mirai Botnet, created by Maneth Balasooriya and Jacob Gottschalk, is a notorious IoT botnet known for Distributed Denial-of-Service attacks on devices like IP cameras and DVRs. It originated from a Minecraft server protection racket and has been involved in major incidents. The botnet operates v
1 views • 8 slides
Oregon Phishing Awareness Program: Implementation and Strategy
The State of Oregon's Phishing Awareness Program involves a structured approach to combat phishing attacks. It includes various phases such as pilot programs, monthly phishing simulations, and employee engagement strategies. The program aims to educate staff at all levels on identifying and reportin
1 views • 10 slides
Challenges and Solutions in Municipal Debt Relief
Municipalities facing financial struggles, particularly with debt to entities like Eskom, are hindered by inefficiencies, low revenue collection, and high indigency levels. Various attempts, including Eskom debt relief initiatives, have been made to address these challenges, but significant improvem
1 views • 29 slides
Monel K500 Flanges Manufacturers
Compared to steel, Monel is truly challenging to machine as it works rapidly. It should be turned and worked at slow velocities and low feed rates. Monel 400 lines and chambers are seen as being utilized in different application attempts like petrochemical plants, oil treatment working conditions, s
1 views • 2 slides
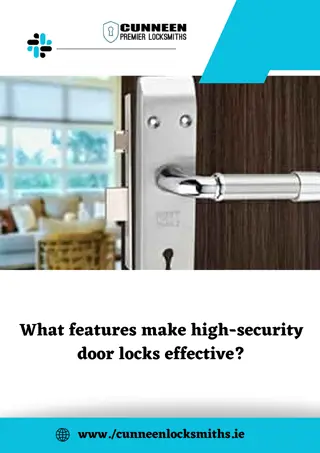
What features make high-security door locks effective
These locks are designed to resist picking attempts by incorporating features like mushroom or spool pins, which hinder traditional picking methods. Additionally, some locks have special mechanisms that engage when picked, making manipulation even more challenging.
1 views • 5 slides
Survival and Struggle: William Strachey's Account of The Tempest
William Strachey, a member of the Virginia Company, recounts the harrowing shipwreck of the Sea Venture on the Bermuda island in a storm. Despite mutiny attempts, survivors endured almost a year before reaching safety. Explore the challenges they faced and the possible influence on Shakespeare's pla
0 views • 10 slides
Comprehensive Guide to Suicide Awareness and Prevention in the Navy
Explore key topics such as suicide and suicide attempts, risk factors, protective factors, first responder roles, and the importance of suicide prevention in the Department of the Navy. Learn how to recognize warning signs, provide care, and intervene effectively to prevent loss of life due to suici
0 views • 15 slides
Understanding Contact Tracing in Public Health
Contact tracing is a crucial process in public health aimed at identifying and monitoring individuals who have been in close contact with those infected with infectious diseases. It involves tracking and managing potential outbreaks, monitoring symptoms, and preventing further transmission. The hist
1 views • 15 slides
Polynomial-time Pseudodeterministic Construction of Primes and Motivational Challenges
Exploring the challenges and advancements in generating prime numbers, particularly focusing on a pseudodeterministic construction method within polynomial time. The discussion includes reviewing previous approaches, fundamental computational problems related to primes, motivational problem statemen
0 views • 40 slides
The Cuban Revolution: Batista to Castro
Fulgencio Batista's rise to power in Cuba in 1933 through coups led to army influence in the government. Fidel Castro, born into an upper-class family, organized rebels to overthrow Batista in the Cuban Revolution. After failed attempts and imprisonment, Castro regrouped, defeated Batista's forces i
1 views • 8 slides
The Monroe Doctrine: A Declaration of American Independence
The Monroe Doctrine asserts that the American continents are not to be colonized by European powers and considers attempts to extend European systems into the hemisphere as dangerous. The United States declares its non-interference with existing European colonies or dependencies.
0 views • 8 slides
Comprehensive Overview of Bariatrics and Pre/Post-Transplant Obesity
Delve into the world of bariatrics and pre/post-transplant obesity with insights on medical weight loss, reasons for bariatric surgery, types of bariatric surgery at VUMC, eligibility criteria for transplant, and the impact of nutrition factors and COVID-19. Learn about specialized medical weight in
0 views • 29 slides
A Problem: Analysis of Family Honor and Moral Dilemmas in Anton Chekhov's Work
Explores the moral dilemma faced by the Uskov family when dealing with Sasha's forgery and non-repayment, highlighting the differing views of paternal uncles and the eventual realization of Sasha's criminal tendencies despite the family's attempts to spare him from punishment.
0 views • 19 slides
The Fate of Opposition in Multiparty Malawi: 1994-2020
This paper explores why Malawi's governance post-Banda has been dominated by elected autocracies rather than democracies. It delves into the effectiveness of opposition groups in terms of organization, funding, public support, and resilience against government attempts to suppress them. The influenc
0 views • 6 slides
Insight into the Autobiographical Play "Sailmaker" by Alan Spence
Alan Spence's play "Sailmaker" delves into the poignant narrative of loss, familial struggles, and societal perceptions. Set in a staunchly Protestant culture of Glasgow, the play weaves a tale of Davie, a sail-maker, and his son Alec as they grapple with grief, adaptation, and personal transformati
1 views • 8 slides
Understanding Word Embeddings in NLP: An Exploration
Explore the concept of word embeddings in natural language processing (NLP), which involves learning vectors that encode words. Discover the properties and relationships between words captured by these embeddings, along with questions around embedding space size and finding the right function. Delve
0 views • 28 slides
Understanding Artificial Intelligence and Intelligence in Computers
Artificial Intelligence (AI) aims to create intelligent computer systems that mimic human behaviors. It involves algorithms derived from human intelligence to make computers smarter and more useful. This includes the ability to acquire knowledge, think, reason, and exhibit goal-oriented behavior. Th
0 views • 13 slides
Understanding Central Place Theory: Key Concepts and Determinants
Central Place Theory (CPT) attempts to explain the spatial arrangement, size, and number of settlements based on central places, zones of influence, and hinterlands. This theory, introduced by Walter Christaller in 1933, outlines the importance of central functions, threshold populations, and factor
0 views • 12 slides
Developing Critical Thinking Skills to Solve Riddles
Enhance your critical thinking abilities by transitioning from being a responsible reader to a critical thinker when solving riddles. This process involves thorough reading, questioning, using your knowledge base to develop answers, testing against the riddle, and overcoming deliberate attempts to m
0 views • 11 slides
Understanding English Language GCSE Paper 2
In preparation for the English Language GCSE Paper 2, it is crucial to grasp the requirements of Question 2 which focuses on identifying explicit and implicit ideas, synthesizing evidence from different texts, and summarizing differences between them. The marks are broken down into levels depending
1 views • 18 slides
Phishing Survival Guide: How to Recognize and Respond to Suspicious Emails
Learn how to spot a phishing email and what steps to take if you receive one or fall victim to a phishing scam. Find out how to identify suspicious links, recognize phishing attempts, and protect yourself from giving out personal information or losing money. Stay informed and secure in the digital a
2 views • 5 slides
Analytic Versus Continental Philosophy in the 20th Century: A Comparative Overview
In 20th-century philosophy, the divide between Analytic and Continental schools deepened but has seen recent attempts at reconciliation. Analytic philosophy emphasizes logic, language, and epistemology, requiring technical expertise, while Continental philosophy rejects metaphysical speculation and
0 views • 15 slides
Status Report: Mr. G. Raseala's Mortal Remains - Department of Health Forensic Pathology Services
The report details the discovery and identification process of an unknown body linked to the Raseala family, highlighting discussions with the family regarding DNA testing and police affidavits. Despite familial attempts to assist with identification, challenges arose, leading to the matter being ha
0 views • 11 slides
Human Predicament: A Moving Tale of Loss and Rejection
A poignant narrative unfolds as a young survivor of World War II attempts to reclaim her belongings from an acquaintance's house. The encounter exposes deep-seated emotions of loss, rejection, and the complexities of post-war existence. Through subtle interactions and realizations, the story delves
1 views • 11 slides
Mastering Front Line Blocking Techniques in Football
Learn the strategies and techniques involved in front line blocking for field goal and PAT attempts in football. Understand the importance of FG/PAT blocking, inside and outside block schemes, and specific drills for developing these skills. Explore detailed instructions on single, look off, and rev
0 views • 18 slides
Enhancing HARQ Framing for IEEE 802.11 Standards
Hybrid-ARQ (HARQ) is a candidate topic for TGbe presentations in IEEE 802.11 standards. Despite previous unsuccessful attempts, there is renewed interest in enabling HARQ through framing support. This document discusses the importance of presenting HARQ framing, outlining the necessary information a
1 views • 7 slides
The Enchanting Tale of "The Twelve Dancing Princesses
In the kingdom, a mysterious secret perplexes the king as his twelve princesses' shoes wear out mysteriously each night. A series of failed attempts by suitors leads a poor soldier to undertake the challenge with the help of an old woman's magical cloak. Will he uncover the princesses' nocturnal esc
2 views • 26 slides
YHI Account Locking: Reasons and Resolutions
Your YHI account could get locked due to multiple failed login attempts, inactivity, or accumulation of browsing data. Learn the common causes of locked accounts and their resolutions, including steps to reset your password or username, reactivate a dormant account, and clear browsing data. Contact
0 views • 7 slides
Impact of Number of Contact Attempts on Response Rates in Multimode Surveys
This meta-analysis investigates the effects of the number of contact attempts on response rates and web completion rates in multimode surveys. Benefits of multimode surveys include improving coverage, increasing response rates, reducing costs, and enhancing measurement accuracy by utilizing multiple
0 views • 27 slides
Comparing Autocratic Attempts in Poland and Hungary
Poland and Hungary exhibit common ideological frames in their autocratic attempts, focusing on regime change rather than government shifts. These attempts utilize ethnonationalism, Euro-skepticism, and xenophobia to justify their actions. The two countries also showcase different types of post-commu
0 views • 15 slides
Understanding and Addressing Suicidal Attempts in Children
Suicidal attempts in children under 12 are rare but pose significant risks that increase with age. Factors such as bullying, neglect, abuse, and family dynamics play crucial roles. A 10-year analysis reveals insights into admissions for suicidal gestures in pre-pubertal children, highlighting the ne
0 views • 22 slides
National COVID-19 Contact Tracing Fundamentals and Operations Overview
The document provides detailed information on the structure and operations of the national COVID-19 contact tracing in England, involving Tier 1, Tier 2, and Tier 3 contact tracing levels. It covers topics such as the role of different tiers, escalation criteria, infectious and incubation periods of
0 views • 15 slides
Understanding the Role of Contact in Contemporary Adoption
The slides prepared by Professor Beth Neil delve into the significance of post-adoption contact, exploring questions, experiences, and studies related to contact between adopted children, birth relatives, and adoptive families. The content highlights the importance of flexibility in contact guidelin
0 views • 37 slides
Learn How to Identify Genuine Emails and Avoid Phishing Attempts
Understanding how to spot phishing emails is crucial for maintaining email security. This activity presents various email examples for evaluation – distinguishing between genuine communications and potential phishing attempts. By honing this skill, individuals can protect themselves from online sc
0 views • 9 slides
Madison County Revenue Compliance Procedures
The procedures followed by Amy Beard, a Revenue Compliance Officer II in Madison County, towards delinquent taxpayers include contacting, sending certified letters, filing warrants, and conducting hearings and trials. Repeat attempts are made to contact taxpayers and ensure compliance. Failure to co
0 views • 11 slides
Analyzing Break-In Attempts Across Multiple Servers using Apache Spark
Exploring cyber attacks on West Chester University's servers by analyzing security logs from five online servers using Apache Spark for large-scale data analysis. Uncovering attack types, frequency patterns, and sources to enhance security measures. Discover insights on break-in attempts and potenti
0 views • 19 slides