CS 404/504 Special Topics
Adversarial machine learning techniques in text and audio data involve generating manipulated samples to mislead models. Text attacks often involve word replacements or additions to alter the meaning while maintaining human readability. Various strategies are used to create adversarial text examples
1 views • 57 slides
Understanding Translation: Key Concepts and Definitions
Translation involves transferring written text from one language to another, while interpreting deals with oral communication. Etymologically, the term "translation" comes from Latin meaning "to carry over." It is a process of replacing an original text with another in a different language. Translat
11 views • 76 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Understanding Text Features in Nonfiction Texts
Text features are essential components of nonfiction texts that authors use to enhance reader comprehension. They include elements such as tables of contents, indexes, glossaries, and titles, each serving a unique purpose in aiding readers to navigate and understand the content. By utilizing these t
1 views • 15 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
Unique Sample Text Images Collection for Creative Projects
Create captivating visuals with this diverse collection of sample text images. From customizable text layouts to percentage displays, this set offers a range of design elements to elevate your creative projects. Explore different styles, colors, and compositions to enhance your presentations, websit
7 views • 10 slides
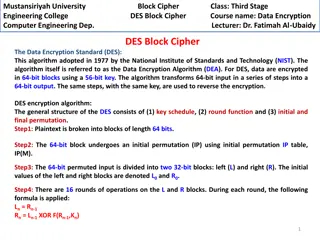
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Introduction to Structured Text in PLC Programming
Structured text is a high-level text language used in PLC programming to implement complex procedures not easily expressed with graphical languages. It involves logical operations, ladder diagrams, and efficient control logic for industrial automation. Concepts such as sensor input, logic operation
5 views • 23 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Enhancing Accessibility Through Alternate Text in Microsoft Documents
Explore the importance of alternate text in Microsoft documents for accessibility. Learn what alternate text is, why and when you should use it, and how to add it effectively. Discover the benefits of incorporating alternate text and the legal aspects related to accessibility under Section 508. Enha
0 views • 23 slides
Optimizing MIH SA Establishment for Single Radio Handover
This presentation discusses the optimization of MIH (Media Independent Handover) Security Association (SA) establishment for single radio handover. It covers the key points and methods proposed for enhancing the communication between Mobile Node (MN) and Top Point of Service (TPoS) using cipher suit
3 views • 6 slides
Text Classification and Nave Bayes: The Power of Categorizing Documents
Text classification, also known as text categorization, involves assigning predefined categories to free-text documents. It plays a crucial role in organizing and extracting insights from vast amounts of unstructured data present in enterprise environments. With the exponential growth of unstructure
0 views • 28 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Audience and Purpose in Text Analysis
When analyzing written texts, identifying the purpose and audience is crucial. The purpose reflects the reason behind the text, while the audience indicates who the text is intended for. By recognizing these aspects, one can better understand the content, language, and overall impact of the text. Va
1 views • 50 slides
Essential Information on Text-to-911 System
Explore key details about the text-to-911 system, including capturing text conversations, handling abandoned calls, transferring text calls to queues, and managing text conversations effectively. Learn about system configurations, call release timings, and dispatcher capabilities in handling text me
0 views • 12 slides
Text-to-911 System Operations Quiz
Test your knowledge on Text-to-911 system operations with this quiz. Learn about capturing text conversations, handling abandoned calls, transferring calls to queues, text conversation timelines, and more. Enhance your understanding of the protocols and procedures involved in managing text-based eme
1 views • 12 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
Key Principles in Cryptography: Kerckhoff's and Key Space
Understanding fundamental principles in cryptography, including Kerckhoff's principle, key space requirements, and the importance of secure private-key encryption. Exploring the Shift Cipher's security, key space size considerations, and the need for heuristic constructions for proving scheme securi
0 views • 51 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Understanding Text Representation and Mining in Business Intelligence and Analytics
Text representation and mining play a crucial role in Business Intelligence and Analytics. Dealing with text data, understanding why text is difficult, and the importance of text preprocessing are key aspects covered in this session. Learn about the goals of text representation, the concept of Bag o
0 views • 27 slides
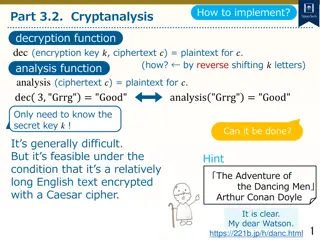
Understanding Cryptanalysis: Key Concepts and Techniques
Cryptanalysis is a fundamental aspect of cryptography that involves decoding encrypted communications and messages. This topic delves into the basic cryptographic tools, such as the Caesar cipher, and explores how encryption and decryption functions work. By understanding cryptanalysis, you can anal
0 views • 12 slides
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Introduction to JMP Text Explorer Platform: Unveiling Text Exploration Tools
Discover the power of JMP tools for text exploration with examples of data curation steps, quantifying text comments, and modeling ratings data. Learn about data requirements, overall processing steps, key definitions, and the bag of words approach in text analysis using Amazon gourmet food review d
0 views • 23 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Understanding Bigrams and Generating Random Text with NLTK
Today's lecture in the Computational Techniques for Linguists course covered the concept of bigrams using NLTK. Bigrams are pairs of words found in text, which are essential for tasks like random text generation. The lecture demonstrated how to work with bigrams, including examples from the NLTK boo
0 views • 19 slides
Exploration of Cryptography and Secure Communication Methods
Delve into the concepts of cryptography, data hiding, and secure communication methods such as Diffie-Hellman key exchange. Discover how Bob safely sends a ring to Alice, the use of Caesar cipher method, and the importance of mathematical principles in ensuring secure communication protocols. Learn
0 views • 22 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
0 views • 16 slides
Enhancing Reading Comprehension Through Text-Dependent Questions
This resource delves into the significance of text-dependent questions in improving students' reading comprehension skills by emphasizing the importance of evidence from the text, building knowledge through nonfiction, and developing critical thinking abilities. It highlights key advances in educati
0 views • 16 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Understanding Encryption and its Importance in Everyday Life
Encryption is a crucial process that transforms messages into secret codes, ensuring only intended recipients can decipher them. This review delves into the significance of encryption for online activities, cracking different cipher methods, and recognizing security flaws. Discover how computational
0 views • 9 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
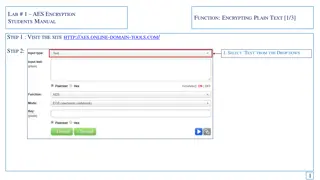
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides
Understanding Loops and ASCII Values in Python
Learn about while loops, fencepost loops, and sentinel loops in Python programming. Explore how ASCII values are assigned to characters and how to manipulate them. Practice a Caesar cipher program to encrypt messages and discover common pitfalls in loop structures. Gain insights into the importance
1 views • 22 slides