Buy Verified Payoneer Accounts
Buy Verified Payeer Accounts\nLooking to expand your online payment options? Look no further - with our Buy Verified Payeer Accounts, you can easily and seamlessly https:\/\/buy5stareviewer.com\/product\/buy-verified-payoneer-account\/. Our accounts are verified, ensuring safe and reliable transacti
3 views • 7 slides
The Secure Path_ Implementing Digital Product Keys for Online Businesses (1)
Implementing digital product keys for online businesses offers a secure path towards protecting valuable software assets and ensuring compliance. By leveraging robust software key management systems, companies can enhance security measures, safeguard against unauthorized distribution, and mitigate p
1 views • 3 slides
The Secure Path_ Implementing Digital Product Keys for Online Businesses (1)
In today's digital landscape, where online businesses reign supreme, safeguarding products and services against piracy and unauthorized access is paramount. Enter the era of digital product keys \u2013 a secure path towards ensuring the integrity of online transactions and protecting intellectual pr
1 views • 3 slides
Global Game Jam NEXT 2024: Unleashing Creativity and Innovation in Game Development
Dive into the world of game development at Global Game Jam NEXT 2024 in Hong Kong, China. This event brings together passionate individuals to collaborate, design, and prototype video games and non-digital games. Explore workshops, team presentations, and the chance to turn your ideas into reality.
1 views • 14 slides
windows 10 pro OEM kEYS
Windows 10 Pro OEM keys are digital licenses that activate Windows 10 Pro on a device. They're sold at lower prices than retail keys, often to system builders. These keys tie to the original hardware and offer full OS functionality, updates, and support. They're cost-effective for PC builders and in
3 views • 2 slides
Cracking the Code Understanding Windows 10 Pro OEM Keys
Understanding Windows 10 Pro OEM keys is crucial for activating licenses efficiently. OEM keys are linked to specific hardware, like pre-built systems, ensuring affordability but limited to that hardware. They're not transferable between devices. Retail keys, on the other hand, offer flexibility but
1 views • 8 slides
WindowKeys Unlocking the Power of Windows with Genuine License Keys
Windows with Genuine License Keys provide a secure and reliable operating system experience. These keys ensure that your version of Windows is legitimate and allows you to access all features and updates. With a genuine license key, you can activate your copy of Windows, receive support from Microso
4 views • 3 slides
Best Automotive Locksmith In Los Angeles
Need a skilled automotive locksmith in Los Angeles. A skilled locksmith with the ability to create car keys and fix ignition issues is known as an automotive locksmith. This locksmith can also fix your automobile's lock mechanisms and unlock your car. Car locksmith are capable of cutting car keys. W
10 views • 7 slides
How can MR game developers ensure accessibility and inclusivity in their game designs
As the world of Mixed Reality (MR) Game Development continues to evolve, developers increasingly recognize the importance of accessibility and inclusivity in their game designs. Creating experiences that are accessible to players of all abilities not only expands the reach of your game but also fost
1 views • 5 slides
What are the essential steps in game design and development for beginners
Embarking on the journey of game design and development can be both exciting and daunting for beginners. Whether you aspire to create captivating games for traditional platforms or explore the immersive realm of Mixed Reality (MR) Game Development, understanding the fundamental steps is crucial. In
0 views • 12 slides
Is Croquet the Ultimate Garden Game? | MegaChess
In the 1860s, croquet as a game kicked up in the United Kingdom, further the years passed when its popularity peaked and this game was adopted by the United States and then it went to other countries. The game of Croquet played in the garden is a fun-to game starting from the afternoon and going thr
2 views • 8 slides
How to Start Your Career in Game Design?
In the digital age, where interactive entertainment holds sway over global audiences, game design stands as a pinnacle of creativity and technical prowess. For those captivated by the idea of crafting virtual worlds, shaping immersive experiences, and pushing the boundaries of technology, a career i
0 views • 6 slides
Understanding VSAM Logical Record Access Methods
VSAM utilizes three primary methods to find logical records - Relative Byte Address, Relative Record Number, and Key field. Relative Byte Address assigns a unique address to each record based on sequential ordering. Relative Record Number is used in RRDS datasets to access records by a numbered sequ
3 views • 35 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Keys in Relational Databases
Keys play a crucial role in relational databases by uniquely identifying records and establishing relationships between tables. Primary keys are essential for data integrity, ensuring each entity is identified uniquely. Learn about primary keys, types of keys, and examples of creating tables with pr
0 views • 57 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
At Vbrae.com, find the greatest game keys available online
At Vbrae.com, find the greatest game keys available online! We provide exceptional customer service and unmatched prices, making it simple for you to purchase the games you enjoy. Get the gaming experience you deserve by shopping now!
3 views • 1 slides
Understanding the Key Concepts of Relational Databases
Introduction to the fundamental concepts of relational databases including the relational model proposed by Edgar F. Codd, relation schemes, relation instances, keys for a relation, and more. Discover the significance of keys, candidate keys, superkeys, and primary keys in database design.
0 views • 27 slides
Buy aged Github accounts
Buy aged Github accounts\nAre you looking to boost your online business? Buy Github accounts might be just what you need. When you buy Github accounts, you open up new doors for your company. These accounts can help you in many ways.When you buy Gith
0 views • 17 slides
Want to buy gourmet coffee online? Threespoons.ie is the best place to buy
Want to buy gourmet coffee online? Threespoons.ie is the best place to buy gourmet coffee online. We have a wide selection of coffee beans, blends, and roasts. Explore our range online or visit us in-store.
0 views • 1 slides
Understanding Database Management Systems and Keys in SQL
This content discusses the importance of organizing data into multiple tables within a database management system, the concept of keys and foreign keys, and the potential issues of data redundancy. It also covers examples of structured data related to products, orders, and manufacturers.
0 views • 55 slides
Exploring Dichotomous Keys in Biology
Delve into the world of dichotomous keys with lessons on their types and practical application. Learn how to use these keys to identify various organisms and classify them based on specific characteristics. From distinguishing between different cat species to identifying aquatic organisms, this expl
0 views • 17 slides
Exploring Computer Keyboards And Typewriters
Dive into the world of computer keyboards and typewriters to understand their similarities and differences. Learn about the layout of alphabetic keys like QWERTY, utilizing the shift key for capitalization and special characters, the function of the enter key, differences between computer keyboards
0 views • 18 slides
Game Programming Patterns Game Loop Summary
This content discusses the game loop structure in game programming patterns, comparing simple main loops and modern event-driven programs. It covers the continuous movement of a game even without user input, the importance of running at a fixed frame rate, and the implementation of frame rate contro
0 views • 14 slides
Game Clock Operator Guidelines and Responsibilities
Guidelines and responsibilities for game clock operators, including dress code, rules study, pre-game preparations, and in-game conduct. Operators must be qualified, familiar with game timing procedures, and maintain focus on accurate timekeeping. Follows procedures for pre-game, game-time operation
0 views • 19 slides
- Rust: A Hardcore Survival Game Experience
- Rust, developed by Facepunch Studios and presented by Ben Walker, immerses players in a challenging survival game where they awaken on an island with nothing but a rock. The goal is to gather resources, craft tools, build shelter, and defend against other players. With multiplayer interactions and
0 views • 19 slides
Understanding Matching Keys in Database Systems
Matching keys play a crucial role in identifying the same real-world entities in database systems. They specify which attributes to compare and how to compare them, helping minimize redundancy and improve data accuracy. This summary discusses relative candidate keys, minimal matching keys, and relia
0 views • 13 slides
Key and Splines Design at Minia University
Key and splines design play a crucial role in connecting mechanical elements like shafts and hubs to transmit power efficiently. This article covers the types of keys, principles of work, and various classifications of keys such as sunk keys, saddle keys, tangent keys, round keys, and splines. It de
0 views • 20 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Casino Game Development Mastery_ Your Ultimate Guide to Success in Online Gambling
Learn all about casino game development, key trends, and how casino game developers create engaging experiences through casino game development services.\n\nSource>>\/\/ \/casino-game-development-company\n\n
0 views • 5 slides
The Case of the Missing Keys
In this amusing tale, Kylee Goodwin narrates the comical ordeal of her mum losing her keys yet again. The family embarks on a frantic search through various rooms, only for the keys to be found hanging safely on their hook by Dad in the end. A lighthearted story of everyday mishaps and the relief of
0 views • 13 slides
Advanced SQL Concepts and Queries Overview
Today's lecture highlights advanced SQL topics such as multi-table queries, set operators, joins, primary keys, foreign keys, and more. The session covers practical activities and fundamental concepts in database management. Explore the nuances of SQL semantics and understand the importance of keys
0 views • 55 slides
Understanding Database Constraints, Keys, and Triggers
Explore the concepts of constraints, foreign keys, local and global constraints, and triggers in the context of database management systems. Delve into topics such as types of constraints, keys, and expressing foreign keys with examples. Enhance your understanding of database integrity and data rela
0 views • 40 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
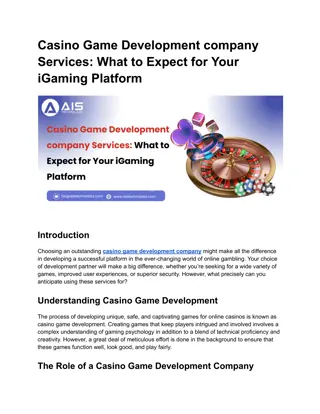
Casino Game Development company Services_ What to Expect for Your iGaming Platform
Discover what to expect from a casino game development company, including casino game developers, casino game development, and casino game development services.\n\nSource>>\/\/medium.com\/@aistechnolabspvtltd\/casino-game-development-company-services
0 views • 4 slides
The Importance of Hiring Experienced Casino Game Developers for Your Online Casino
Discover why hiring experienced casino game developers for your online platform ensures superior casino game development services and card game development.\n\nSource>>\/\/ \/casino-game-development-company\n\n
0 views • 4 slides
Buy Verified Binance Accounts in Exciting Price
\n\nTags: Best Place to Buy Verified Binance Accounts, Buy Verified Binance Account, Buy Verified Binance Accounts, Buy Verified Binance Accounts USA, Can I Buy Verified Binance Accounts\n\nBuy Verified Binance Accounts\nThe world economy is entering
0 views • 12 slides
2024s Best Site to Buy Airbnb accounts
2024s Best Site to Buy Airbnb accounts \nTags: Buy Airbnb account, Buy Airbnb accounts, Buy Airbnb Superhost account, Buy verified Airbnb Accounts, I want to buy an Airbnb account\n\nEmail: usaboostsocial@gmail.com\nTelegram: @usaboostsocial\nSkype: usaboostsocial\nWhatsApp: 1 (929) 630-4484\n2024s
0 views • 14 slides
IDEAL-GAME Project Meeting and Creator Tool Development in Spain
Join the IDEAL-GAME project meeting in Madrid, Spain, focusing on learning scenarios, book design, and usability testing for the Online Serious Game Creator. Explore the Technology Acceptance Model (TAM) and gain insights into questionnaire design. Participate in enhancing higher education through i
0 views • 11 slides
Understanding Computer Input Devices and Keystrokes
The system box of a computer contains essential components like the CPU, motherboard, and memory chips. Character keys, action keys, and application-dependent keys on a keyboard serve different functions, from typing letters to performing actions. Key combinations and shortcuts provide efficient way
0 views • 10 slides