Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Blocked drains wynnum
Blocked Drains Wynnum can be extremely inconvenient when they occur consistently, so our plumbing team are readily available to help. No matter what drainage system your blockage is occurring in, our team will find a lasting solution for you. We use the latest industry tools and equipment to locate
4 views • 5 slides
Hope for Pregnancy What You Need to Know About Blocked Fallopian Tubes
Over 30% of women suffering from Infertility have either blocked or damaged fallopian tubes. The condition of blocked fallopian tubes in the female reproductive tract is also known as tubal Infertility, tubal disease, or tubal occlusion. Unlike other Infertility disorders, blocked fallopian tubes do
9 views • 7 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Rate Optimization in Wideband RIS-assisted Wireless Systems
This research focuses on rate optimization in wideband RIS-assisted wireless systems, specifically investigating MIMO RIS-assisted systems in sub-6 GHz mmWave settings. Pathloss and blockage modeling, along with LOS vs. spectral efficiency and RIS-UE distance vs. spectral efficiency analyses, are ke
0 views • 4 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
NC22Plex STR Detection Kit: Advanced 5-Color Fluorescence Detection System
Explore the cutting-edge NC22Plex STR Detection Kit from Jiangsu Superbio Biomedical, offering a 5-color fluorescence detection system suitable for multiple applications. Enhance your research capabilities with this innovative product designed for precision and efficiency.
0 views • 20 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
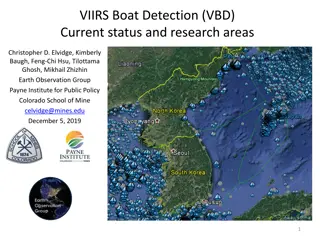
VIIRS Boat Detection (VBD) Research Overview
The Visible Infrared Imaging Radiometer Suite (VIIRS) program, a joint effort between NASA and NOAA, focuses on weather prediction and boat detection using low light imaging data collected at night. The VIIRS system provides global coverage with sensitive instruments and efficient data flow processe
1 views • 13 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Stop Hidden Water Damage: Your Ultimate Guide to Leak Detection in San Diego
Learn how San Diego leak detection services can help protect your home from water damage. Discover the signs of leaks, advanced detection technologies, and tips to prevent costly repairs. Stay ahead with proactive slab leak detection and expert solut
0 views • 6 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
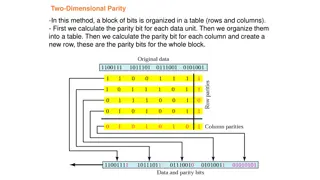
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
EPA Compliance Basics: Tank Leak Detection and Monitoring Methods
Learn about EPA requirements for tank leak detection, release detection methods, and compliance methods for monitoring tank systems. Understand the importance of implementing effective leak detection systems to prevent contamination and comply with federal regulations, including Automatic Tank Gaugi
0 views • 18 slides
Gas Detection of Hydrogen/Natural Gas Blends in the Gas Industry
Gas detection instruments play a crucial role in assessing the presence of hazardous atmospheres in the gas industry. This study focuses on the impact of adding hydrogen up to 20% in natural gas blends on gas detection instruments. The aim is to understand any potential inaccuracies in readings and
0 views • 30 slides
Timely San Diego Leak Detection | Protect Your Home from Water Damage
Discover the importance of timely leak detection in San Diego. Prevent costly water damage, reduce bills, and protect your home with professional leak detection services. Learn more about slab leak detection and prevention today!\n\nKnow more: \/\/m
0 views • 9 slides
Non-Isotopic Labeling for Molecular Detection
The use of non-radioactive probes in molecular detection involves synthetic DNA or RNA molecules with specific target sequences and reporter groups detectable via fluorescence spectroscopy. Direct and indirect labeling methods utilize fluorescent dyes or enzymes conjugated to modified nucleotides, a
0 views • 20 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
LD-Sketch: Distributed Sketching Design for Anomaly Detection in Network Data Streams
LD-Sketch is a novel distributed sketching design for accurate and scalable anomaly detection in network data streams, addressing challenges such as tracking heavy keys in real-time across a vast key space. By combining high accuracy, speed, and low space complexity, LD-Sketch enables efficient heav
0 views • 25 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Impact of Tx EVM on MIMO Detection Follow-Up
This document discusses the impact of Tx EVM on MIMO detection, highlighting that improving Tx EVM can achieve theoretical gains in nonlinear detection. It addresses questions raised during discussions and presents an optimal detector scenario in the presence of colored noise from Tx EVM. Simulation
0 views • 14 slides
Understanding Ear Wax (Cerumen) and Its Management
Ear wax, also known as cerumen, is a yellowish waxy substance secreted in the ear canal to protect, clean, and lubricate. Excess ear wax can lead to hearing issues, such as partial loss or malfunction of hearing aids. Learn about the types of ear wax, symptoms of blockage, and safe methods of remova
0 views • 9 slides
Enhancing Blockage Detection and Handover on 60 GHz Networks with P4 Programmable Data Planes
The study presents a system using programmable switches to monitor packet inter-arrival time for blockage detection on mmWave networks. Results show fast recovery speeds and minimal impact on flow completion time, with contributions focusing on leveraging programmable switches and real device scenar
0 views • 7 slides
Object-Oriented Python Code for WIMP Direct Detection Signals
Calculating signals for Weakly Interacting Massive Particle (WIMP) direct detection using an object-oriented Python code called WimPyDD. WimPyDD provides accurate predictions for expected rates in WIMP direct detection experiments within the framework of Galilean invariant non-relativistic effective
0 views • 24 slides
Prevent Water Damage_ Why Slab Leak Detection Matters in San Diego
Protect your home from costly water damage with professional slab leak detection services in San Diego. Learn how early detection can safeguard your foundation and avoid expensive repairs.\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 9 slides
Detection Methods for GMOs and LMOs in Molecular Biology
Techniques in Molecular Biology lecture discusses GMOs and LMOs, transgenic plants, examples like Bt cotton and Golden rice, detection methods, purpose of detection, and how transgenic plants are created. The content emphasizes the need to differentiate GM crops from non-GM crops and the importance
2 views • 40 slides
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
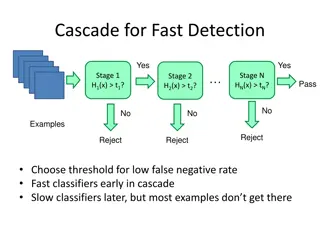
Understanding Face Detection via AdaBoost - CSE 455.1
Face detection using AdaBoost algorithm involves training a sequence of weak classifiers to form a strong final classifier. The process includes weighted data sampling, modifying AdaBoost for Viola-Jones face detector features, and more. Face detection and recognition technology is advancing rapidly
0 views • 49 slides
Rootkit Detection with RAI - Practical Challenges and Solutions
Practical Rootkit Detection with RAI by Christoph Csallner explores the challenges in malware detection, such as slow signature-based deployments and untrustworthy legacy platforms. The threat model presented illustrates how adversaries can manipulate binaries and gain root access. RAI offers a solu
0 views • 14 slides
Innovative Device-Free Passive Motion Detection System
This research presents RASID, a robust WLAN device-free passive motion detection system that can detect human presence without the need for carrying any devices or interacting actively with the system. By analyzing changes in received signal strength behavior, the system can identify human motions.
0 views • 43 slides
Understanding Blood Clots, Vessel Blockage, and Strokes
Polymers, blood clots, vessel blockages, and strokes are explained in this informative content. Blood clot formation, vessel blockages due to embolism and thrombosis, and the different types of strokes are detailed. The effects of stroke on the brain and its various regions are highlighted.
0 views • 11 slides
Water Quality Monitoring Project Meeting Highlights
The INTERREG Meeting ATCZ-86 held on 02.09.2021 showcased project progress reports, discussions on sensor development, webserver deployment, and monitoring station concepts. Activities included multi-sensor systems for water parameter measurement, sensor module evaluations, and development of data h
0 views • 13 slides
Beamforming in mmWave Transmission for 5G Networks
Adaptive beamforming plays a vital role in supporting mmWave transmission in 5G networks, addressing challenges like high propagation loss and signal blockage. The use of an innovative user-assisted approach, involving angle computation and configuration messages, enhances the beamforming process fo
0 views • 18 slides