Hope Student Retention & Persistence Analysis Overview
Analysis conducted by the Frost Center at Hope College on student retention and persistence, focusing on demographic variables and involvement in various activities. The retention rates by cohort and class year are outlined, along with explanations on retention calculations and measurements. The dat
0 views • 29 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
Exploring Att&ck Matrix: Engage Ludicrous Speed
Dive into the world of the Mitre Att&ck Matrix, where crazy ampersands and Trebuchet Font cues you in on how to engage Ludicrous Speed and understand the basics of attacker/adversary tactics, techniques, and common use cases. Explore matrices, prevent attacks, and work programmatically with Att&ck u
0 views • 26 slides
Understanding Network Security: Hijacking, Denial of Service, and IDS
This content delves into the concepts of spying and hijacking in network security, covering topics such as eavesdropping on packets, injecting packets into streams, denial of service attacks, and defense mechanisms like firewalls and IDS. It explores low-level attacks and defenses, including ARP cac
1 views • 81 slides
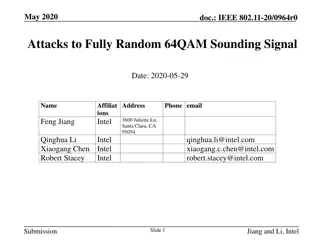
Attacks on Fully Random 64QAM Sounding Signal in IEEE 802.11-20/0964r0
Presentation by Intel demonstrates vulnerabilities in fully random QPSK and 64QAM sounding signals in IEEE 802.11-20/0964r0. Proposed attack methods, including Viterbi equalizer attacks, and solutions such as Secure LTF mechanism and windowed FFT are discussed to enhance security in ranging. The pre
0 views • 31 slides
Adversarial Risk Analysis for Urban Security
Adversarial Risk Analysis for Urban Security is a framework aimed at managing risks from the actions of intelligent adversaries in urban security scenarios. The framework employs a Defend-Attack-Defend model where two intelligent players, a Defender and an Attacker, engage in sequential moves, with
1 views • 26 slides
Factors Influencing STEM Major Persistence Among Underrepresented Minority Students in College
This study examines the retention of aspiring scientists and engineers in STEM majors, focusing on underrepresented minority (URM) students. It investigates differences in intentions and persistence across racial groups, considering the impact of college experiences. Factors influencing STEM major p
0 views • 13 slides
Exploring Latinas/os in STEM: Factors Influencing Persistence
The study investigates the experiences of Latinas/os in STEM fields to understand the factors that contribute to their persistence. It highlights disparities in academic preparation, self-confidence, and aspirations compared to White students. Latinas/os face higher financial concerns, lower academi
4 views • 22 slides
Examining Medication Persistence Methods and Outcomes in Patients Post MI
Understanding medication persistence post myocardial infarction (MI) is crucial for optimizing patient outcomes. The ARTEMIS trial explored variation in P2Y12 inhibitor persistence rates using multiple measurement methods. This study design involved over 11,000 MI patients across 301 US hospitals, w
5 views • 12 slides
Introduction to Network Security Course
This network security course by Professor Christo Wilson covers fundamental security principles applicable to all systems, designing secure networked systems, understanding attacker mindsets, and respecting ethical boundaries in security research. The course aims to equip students with the ability t
0 views • 26 slides
Understanding Blending Attacks on Mixes by Meng Tang
Explore the effectiveness of blending attacks on mixes, including steps of a blending attack, attack models, factors affecting the attack, defense strategies, and insights from the attacker's viewpoint.
0 views • 25 slides
Understanding BIOS Flash and System Management Mode Internals
Dive into the intricacies of BIOS flash and system management mode internals, exploring SPI flash technology, attacker persistence strategies, Copernicus vulnerability scanning results, BIOS flash locations, and boot BIOS flash configurations. Uncover the significance of hardware pins in determining
0 views • 28 slides
Cybersecurity News and Insights
Explore the latest cybersecurity news and insights on hacking incidents, data breaches, vulnerabilities, and attacker strategies discussed in the context of MIS. Stay informed about ongoing cyber threats and how attackers operate once inside a system.
0 views • 31 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
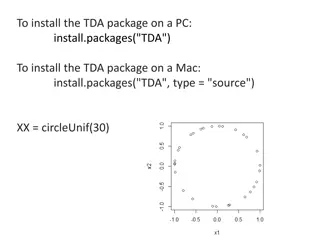
Understanding Topological Data Analysis (TDA) with Persistence Diagrams
Dive into the world of Topological Data Analysis (TDA) by learning how to install the TDA package on different operating systems and interpreting the plots of data points, barcodes, and persistence diagrams. Explore the visualization of cycles in different dimensions and understand the concepts of H
0 views • 17 slides
High Impact Practices for Fostering Persistence in Adult Education Programs
Explore effective strategies and insights on fostering persistence among adult learners in educational programs. Learn about recruitment techniques, intake processes, and program design to support learners in achieving their educational goals. Dive into activities and surveys to enhance understandin
0 views • 18 slides
Persistence of Langmuir Modes in Complex Shear Flows
Exploring the persistence of Langmuir modes in kinematically complex plasma flows with a focus on shear flows in nature and historical backgrounds. The research delves into the methodology of classical theory and introduces the nonmodal approach to address limitations. Details on shear flow definiti
0 views • 16 slides
Insights from Northwick Park Emergency Department & Young Harrow Foundation Workshop
Explore statistics and insights from the Northwick Park Emergency Department and Young Harrow Foundation workshop, focusing on emergency medicine, mental health, youth violence, trauma patients, and demographic distribution in the NW London sector. Discover trends in ED attendances related to youth
0 views • 15 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Understanding Threat Modeling and Offensive Security
Threat modeling in offensive security involves determining potential threat scenarios that could compromise a system, understanding the system from an attacker's perspective, and devising defensive strategies. It helps confirm security implementations, identify gaps, monitor shortcomings, vulnerabil
0 views • 31 slides
Exploring Persistence as a Habit of Mind: Student Perspective at Chabot College
Delve into the exploration of persistence as a Habit of Mind through the lens of students at Chabot College. Discover the strategies and actions that enable students to persist in their courses, examined through surveys and qualitative research methods. Gain insights into the formation of Faculty In
0 views • 28 slides
Understanding Web Security: Risks, Threats, and Safeguards
In the realm of web security, it is crucial to shift our mindset to anticipate malicious intent and potential vulnerabilities. Attackers can aim to access private data, manipulate information, disrupt services, or tarnish reputations. Familiarize yourself with common attacker goals, tools used, and
0 views • 18 slides
Hands-Off Persistence System (HOPS) Overview
Hands-Off Persistence System (HOPS) is a novel approach to memory hierarchy design, focusing on volatile memory with minimal changes. It enables multiple copies of the same cacheline, handles cross-dependencies conservatively, and optimizes transaction processing epochs efficiently. The system archi
0 views • 72 slides
Innovations in Nonvolatile Memory Systems and Architecture
Cutting-edge research presented at NVMW 2023 explores the frontier of nonvolatile memory technologies, such as Intel PMEM operation modes and Whole-System Persistence (WSP). Topics include unlocking the full potential of NVM, failure-atomic region-level WSP, and accelerated store persistence methods
0 views • 21 slides
Leveraging Persistence for Offensive Security
Explore the tactics and techniques of persistence for offensive security, covering topics such as penetration testing, red team engagements, credential stealing, and utilizing registry keys and scheduled tasks. Discover ways to maintain access to systems through unauthorized means and understand the
0 views • 20 slides
Tools for Automated Data Persistence and Quality Control in Financial Environment
The Schonfeld Environment, a registered investment firm, utilizes kdb+ for data management. Challenges involve persisting, automating, and ensuring quality control of proprietary data. The Persistence API facilitates secure and efficient management of derived datasets.
0 views • 13 slides
Understanding Persistence Ignorance in Domain Models
Persistence Ignorance is a concept in software development where domain models do not contain any persistence-related code, focusing solely on business logic. This approach promotes separation of concerns, single responsibility, loose coupling, testability, and reusability. NHibernate and Plain Old
0 views • 8 slides
Understanding Java Persistence API (JPA) for Data Management in Java Applications
Java Persistence API (JPA) is a specification that provides a framework for managing relational data in Java applications. It simplifies ORM solutions, offers vendor independence, and supports test-driven development with annotation-driven mapping.
0 views • 31 slides
Enhancing Student Persistence Through Academic Advising Strategies
Northeastern University's initiatives focus on persistence advising, offering continuous support to students facing challenges. With faculty and staff collaboration, a campus culture of caring is nurtured, leveraging holistic approaches and creating customized support networks. The persistence advis
0 views • 19 slides
Comparison of Persistence on Guideline-Recommended HIV Treatment Among US Medicaid Beneficiaries
This study compares the persistence rates of newer DHHS guideline-recommended single- and multiple-tablet regimens for treatment-naive patients living with HIV. The analysis utilized the All-Payer Claims Database to assess treatment patterns among Medicaid beneficiaries, highlighting the importance
1 views • 19 slides
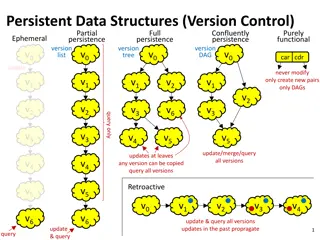
Understanding Persistent Data Structures and Version Control
Exploring persistent data structures and version control concepts, including partial persistence, full confluence, purely functional approaches, and ephemeral versions. Delve into tree lists, full and partial persistence, query methods, retroactive updates, planar point location, path copying in tre
0 views • 9 slides
Enhancing Storage Consistency in Persistent Memory Systems
Persistent memory systems face challenges with strict write ordering requirements affecting performance. This study introduces Loose-Ordering Consistency to minimize overhead while ensuring storage consistency by leveraging hardware support and innovative commit protocols. Results show a significant
0 views • 26 slides
Understanding Cohort Analysis in Educational Research
Cohort analysis in educational research involves studying a group of students meeting specific criteria to analyze trends over time. Baseline data is crucial for comparison, and it helps institutions track student persistence, retention, and attrition rates. By establishing baselines, institutions c
0 views • 12 slides
Randomness in Topology: Persistence Diagrams, Euler Characteristics, and Möbius Inversion
Exploring the concept of randomness in topology, this work delves into the fascinating realms of persistence diagrams, Euler characteristics, and Möbius inversion. Jointly presented with Amit Patel, the study uncovers the vast generalization of Möbius inversion as a principle of inclusion-exclusio
0 views • 57 slides
The Impact of Unmet Financial Needs on First-Year Student Persistence
This study explores how unmet financial needs affect the persistence of first-year students in higher education institutions, particularly in South Africa. It discusses the challenges faced by students who lack adequate financial support and examines factors contributing to student retention. The re
0 views • 19 slides
Analysis of Teacher Credential Impact on Student Persistence and Level Completions
Exploring the correlation between teachers holding a Texas Teacher Credential and student performance in terms of persistence and level completions. The study evaluates data from identified credential teachers and non-credential groups, emphasizing teacher experience levels. Additionally, profession
0 views • 21 slides
Overview of ATLAS I/O Framework and Data Persistence
This overview provides a high-level understanding of the ATLAS Input/Output framework and data persistence, focusing on Athena as the event processing framework. It discusses the basics of ATLAS I/O, including writing and reading event data, as well as key components like OutputStream, EventSelector
0 views • 29 slides
Cryptology System Design Fundamentals: ARSA Cryptosystem Examination Solutions
The given content discusses the solution to an ARSA cryptosystem final examination design problem, involving the computation of public and secret keys for users A and B, encryption and signing of messages, and considerations for attacker interceptions and computations. The solution guides through th
0 views • 18 slides
Uncovering the Topology of Time-Varying fMRI Data using Cubical Persistence
Authors present a novel framework to transform time-varying fMRI data into topological representations, utilizing cubical persistence to analyze brain state trajectories and cluster participants based on topological features in blood flow in the brain, providing insights into cognitive processes. fM
0 views • 11 slides
Advanced Topics in Topological Data Analysis: Research Highlights
Explore cutting-edge research in Topological Data Analysis (TDA) through topics such as Mapper Stability Measures, Deep Learning advancements, Vectorization techniques, Generalized Persistence modeling, Stochastic Aspects analysis, Formal Properties of Persistence, and Complement Problems in TDA app
0 views • 8 slides