Universal Two-Qubit Computational Register for Trapped Ion Quantum Processors
Universal two-qubit computational register for trapped ion quantum processors, including state preparation, gates, and benchmarking. The experimental setup and results are discussed.
0 views • 14 slides
HPE 651089-001 1u Cable Management Arm for ProLiant DL360p Gen8/Gen9
New | 651089-001 | HPE 1u Cable Management Arm for ProLiant DL360p Gen8\/Gen9 | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\nProduct Link : \/\/ \/hpe-651089-001-1u-cable-management-arm-for-proliant-dl360p-gen8-gen9\/
2 views • 1 slides
Towards Single-Event Upset Detection in Hardware Secure RISC-V Processors
This research focuses on detecting single-event upsets (SEUs) in hardware-secure RISC-V processors in radiation environments, such as high-energy physics and space applications. Motivated by the potential data errors, unpredictable behavior, or crashes caused by SEUs, the study explores fault inject
4 views • 17 slides
Understanding Superscalar Processors in Processor Design
Explore the concept of superscalar processors in processor design, including the ability to execute instructions independently and concurrently. Learn about the difference between superscalar and superpipelined approaches, instruction-level parallelism, and the limitations and design issues involved
0 views • 55 slides
Understanding Computer Architecture: A Comprehensive Overview by Prof. Dr. Nizamettin AYDIN
Explore the realm of computer architecture through the expertise of Prof. Dr. Nizamettin AYDIN, covering topics like RISC characteristics, major advances in computers, comparison of processors, and the driving force for CISC. Delve into the evolution of processors, register optimization, and the tra
0 views • 42 slides
Understanding Multicore Processors: Hardware and Software Perspectives
This chapter delves into the realm of multicore processors, shedding light on both hardware and software performance issues associated with these advanced computing systems. Readers will gain insights into the evolving landscape of multicore organization, spanning embedded systems to mainframes. The
1 views • 36 slides
Introduction to Intel Assembly Language for x86 Processors
Intel Assembly Language is a low-level programming language designed for Intel 8086 processors and their successors. It features a CISC instruction set, special purpose registers, memory-register operations, and various addressing modes. The language employs mnemonics to represent instructions, with
2 views • 12 slides
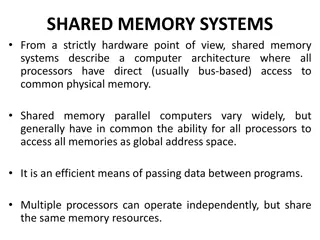
Understanding Shared Memory Systems in Computer Architecture
Shared memory systems in computer architecture allow all processors to have direct access to common physical memory, enabling efficient data sharing and communication among processors. These systems consist of a global address space accessible by all processors, facilitating parallel processing but
1 views • 19 slides
Understanding Computer System Architectures
Computer systems can be categorized into single-processor and multiprocessor systems. Single-processor systems have one main CPU but may also contain special-purpose processors. Multiprocessor systems have multiple processors that share resources, offering advantages like increased throughput, econo
2 views • 25 slides
Understanding System Management Mode (SMM) in x86 Processors
System Management Mode (SMM) is a highly privileged mode in x86 processors that provides an isolated environment for critical system operations like power management and hardware control. When the processor enters SMM, it suspends all other tasks and runs proprietary OEM code. Protecting SMM is cruc
1 views • 26 slides
PowerPC Architecture Overview and Evolution
PowerPC is a RISC instruction set architecture developed by IBM in collaboration with Apple and Motorola in the early 1990s. It is based on IBM's POWER architecture, offering both 32-bit and 64-bit processors popular in embedded systems. The architecture emphasizes a reduced set of pipelined instruc
2 views • 13 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Contrasting RISC and CISC Architectures
Contrasting RISC (Reduced Instruction Set Computing) and CISC (Complex Instruction Set Computing) architectures, the images and descriptions elaborate on their advantages and disadvantages, with a focus on multiplying two numbers in memory using a CISC approach. CISC processors aim to complete tasks
0 views • 35 slides
Understanding ARM RISC Design Philosophy and Its Impact
Delve into the world of ARM processors, exploring the RISC design philosophy that underpins their efficiency and widespread application. Learn about key principles, compare RISC with CISC, and discover how ARM's simplicity, orthogonality, and efficient architecture contribute to its dominance in mob
0 views • 12 slides
Design and Implementation of Shifters in ALU for Single-Cycle Processors
The detailed discussion covers the construction of a multifunction Arithmetic Logic Unit (ALU) for computer processors, specifically focusing on the design and implementation of shifters. Shift operations such as SLL, SRL, SRA, and ROR are explained, with insights into shifting processes and data ex
0 views • 5 slides
Understanding the Hemiplegic Arm and Hand After Stroke
A stroke can cause weakness in the arm and hand, affecting movement and daily tasks. Careful handling reduces pain and complications. Common issues include pain, swelling, altered sensation, and muscle tone changes. Limbs may have low tone (limp) or high tone (stiff), leading to challenges in moveme
0 views • 11 slides
k-Ary Search on Modern Processors
The presentation discusses the importance of searching operations in computer science, focusing on different types of searches such as point queries, nearest-neighbor key queries, and range queries. It explores search algorithms including linear search, hash-based search, tree-based search, and sort
0 views • 18 slides
Enhancing I/O Performance on SMT Processors in Cloud Environments
Improving I/O performance and efficiency on Simultaneous Multi-Threading (SMT) processors in virtualized clouds is crucial for maximizing system throughput and resource utilization. The vSMT-IO approach focuses on efficiently scheduling I/O workloads on SMT CPUs by making them "dormant" on hardware
0 views • 31 slides
Dynamic Load Balancing on Graphics Processors: A Detailed Study
In this comprehensive study by Daniel Cederman and Philippas Tsigas from Chalmers University of Technology, the focus is on dynamic load balancing on graphics processors. The research delves into the motivation, methods, experimental evaluations, and conclusions related to this critical area. It cov
0 views • 57 slides
Scaling Multi-Core Network Processors Without the Reordering Bottleneck
This study discusses the challenges in packet ordering within parallel network processors and proposes solutions to reduce reordering delay. Various approaches such as static mapping, single SN approach, and per-flow sequencing are explored to optimize processing efficiency in multi-core NP architec
0 views • 22 slides
ARM Microcontroller Power Supply, Reset, and Clock Control Overview
This overview covers the power supply, reset control, and clock sources for ARM microcontrollers, focusing on aspects such as power supplies, battery backup, voltage regulator operation modes, and power supply supervisor functions. It discusses essential details like operating voltages, backup domai
0 views • 27 slides
- Understanding Exceptions in Modern High-Performance Processors
- Overview of exceptions in pipeline processors, including conditions halting normal operation, handling techniques, and example scenarios triggering exception detection during fetch and memory stages. Emphasis on maintaining exception ordering and performance analysis in out-of-order execution proc
0 views • 28 slides
Cache-Based Attack and Defense on ARM Platform - Doctoral Dissertation Thesis Defense
Recent research efforts have focused on securing ARM platforms due to their prevalence in the market. The study delves into cache-based security threats and defenses on ARM architecture, emphasizing the risks posed by side-channel attacks on the Last-Level Cache. It discusses the effectiveness of si
0 views • 44 slides
Cost-Effectiveness of TrustZone Defense on ARM Platform
Recent research focuses on enhancing security on ARM platforms due to increasing security risks. This study delves into the challenges posed by cache-based security threats and discusses the development of a defense framework for ARM. The exploration involves experimental evaluations aiming to optim
0 views • 25 slides
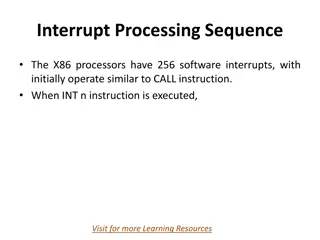
Understanding Interrupt Processing Sequence in X86 Processors
X86 processors have 256 software interrupts, functioning similarly to a CALL instruction. When an INT n instruction is executed, the processor follows a sequence involving pushing the flag register, clearing flags, finding the correct ISR address, and transferring CPU control. Special interrupts lik
0 views • 10 slides
ARM Cortex-M Interrupt and Exception Programming Overview
Explore the fundamentals of interrupts and exceptions programming in ARM Cortex-M microcontrollers. Topics include interrupt handling mechanisms, interrupt vector table, interrupt priorities, control registers, and transitioning from reset to boot programs. Gain insights into the privileged executio
0 views • 31 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Cutting-Edge Robotics: Black-I Robotics Innovations
Black-I Robotics, led by CEO Brian Hart, is a technology-focused company specializing in unmanned ground vehicles and mobile manipulators. Their flagship product, the Landshark Robotic Arm, is a powerful electric arm designed for manipulating artillery shells and disrupting improvised explosive devi
0 views • 28 slides
Should Ghana Provide Discounts on Cocoa Beans for Local Processors? A Case Study
Ghana's cocoa sector plays a significant role in the country's economy, yet less than 25% of cocoa beans are processed locally, limiting its market share. This case study explores the impact of local processing on Ghana's cocoa industry and discusses the dilemma of value addition. The question of wh
0 views • 14 slides
Understanding Shared Memory Coherence, Synchronization, and Consistency in Embedded Computer Architecture
This content delves into the complexities of shared memory architecture in embedded computer systems, addressing key issues such as coherence, synchronization, and memory consistency. It explains how cache coherence ensures the most recent data is accessed by all processors, and discusses methods li
0 views • 47 slides
Constructive Computer Architecture: Multistage Pipelined Processors
Explore the concepts of multistage pipelined processors and modular refinement in computer architecture as discussed by Arvind and his team at the Computer Science & Artificial Intelligence Lab, Massachusetts Institute of Technology. The content delves into the design and implementation of a 3-stage
0 views • 28 slides
Data Hazards in Pipelined Processors: Understanding and Mitigation
Explore the concept of data hazards in pipelined processors, focusing on read-after-write (RAW) hazards and their impact on pipeline performance. Learn strategies to mitigate data hazards, such as using a scoreboard to track instructions and stall the Fetch stage when necessary. Discover how adjusti
0 views • 23 slides
Understanding Instruction Flow Techniques in High-IPC Processors
Explore the intricate processes involved in optimizing instruction flow within high-IPC processors, tackling challenges such as control dependences, branch speculation, and branch direction prediction. Learn about the goals, impediments, branch types, and implementations that shape the efficient exe
0 views • 80 slides
Memory Benchmarking of ARM-Based Systems-on-Chip
This study evaluates memory performance in ARM-based Systems-on-Chip (SoCs) for Data Stream Computing (DSC). It discusses key challenges such as energy efficiency, storage capacity, costs, and memory latencies. The relevance of memory performance in military-led research is highlighted, along with t
0 views • 40 slides
Leveraging Graphics Processors for Accelerating Sonar Imaging via Backpropagation
Utilizing graphics processors to enhance synthetic aperture sonar imaging through backpropagation is a key focus in high-performance embedded computing workshops. The backpropagation process involves transmitting sonar pulses, capturing returns, and reconstructing images based on recorded samples. T
0 views • 18 slides
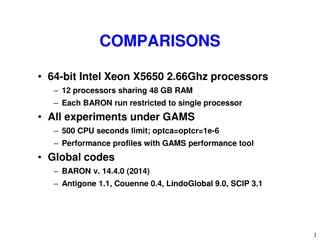
Performance Comparison of Optimization Solvers on Intel Xeon X5650 Processors
Experiment results comparing the performance of optimization solvers (BARON, Antigone, LindoGlobal, SCIP, Couenne) on Intel Xeon X5650 2.66Ghz processors with 48GB RAM. The study includes 369 NLPs from various libraries and an aggregate analysis of 1740 NLPs and MINLPs. Performance profiles generate
0 views • 6 slides
Optimizing Packet Processing on Arm Architecture in OVS: A Story of Performance Enhancement and Stability
Exploring the optimization of packet processing on Arm architecture in OVS, focusing on improving performance and stability through various techniques such as offloading datapath operations, implementing efficient lookup tables, accelerating hash calculations, and addressing bottlenecks. The agenda
0 views • 22 slides
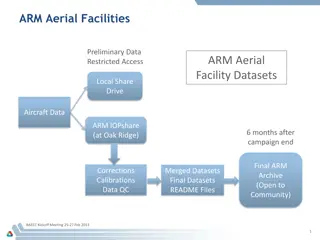
ARM Aerial Facilities Data Management Instructions
ARM provides comprehensive guidelines for managing and sharing aerial facility data, including data collection, processing, and accessibility for the scientific community. The process involves automatic collection, processing, and ingest of data to meet ARM-approved standards, with options for data
0 views • 6 slides
Hardware Performance Monitoring with Kernel Modules
This document explores the use of hardware performance counters and cycle counting on x86 and ARM architectures for monitoring and analyzing system performance. It covers topics such as the utilization of hardware counters, cycle counting on x86 processors, and the ARM Performance Monitor Unit (PMU)
0 views • 12 slides
Flynn's Taxonomy: Classification of Computer Architectures
Michael Flynn's 1966 classification divides computer architectures into SISD, SIMD, MISD, and MIMD based on the number of instruction streams and data streams. SISD corresponds to traditional single-processor systems, SIMD involves multiple processors handling different data streams, MISD has multip
0 views • 10 slides