Red, Blue, Purple Team Development Discussion Panel
Explore best practices for team development in RBP security operations, focusing on operationalizing security focuses, assessing operator capabilities, implementing development pillars, and utilizing cyber ranges for hands-on skills training. Learn how to optimize security insight, architecture desi
0 views • 13 slides
Understanding Information Flow in Software Security
Explore the concept of information flow in software security, focusing on implicit data flows from confidential sources to sinks. Learn about threat models, side channels, and defending against potential attacks in practical contexts. Delve into the complexities of maintaining security while conside
5 views • 26 slides
The Fight - A Story of Friendship and Understanding
Ranji finds himself in a fight over the rights to a pool but ends up befriending his adversary through a series of challenges and understanding. Despite initial conflict, they learn from each other, eventually becoming friends and forming a bond over shared experiences.
0 views • 9 slides
Bankruptcy Motion Practice Essentials
Dive into the key aspects of bankruptcy motion practice, from contested matters to adversary proceedings. Learn about the rules and guidelines, required documents for motions, and best practices for drafting motions in bankruptcy cases.
0 views • 12 slides
Strong Average-Case Circuit Lower Bounds: A Brief Overview
Exploring the history and motivation behind the Circuit Lower Bounds Program focused on proving complexity class separations through non-trivial derandomization, with a primary emphasis on Strong Average-Case Lower Bounds. Ren and Chen delve into the pursuit to establish ?? ≠ ? since the 1980s.
0 views • 61 slides
Understanding Tail Bounds and Inequalities in Probability Theory
Explore concepts like Markov's Inequality, Chebyshev's Inequality, and their proofs in the context of random variables and probability distributions. Learn how to apply these bounds to analyze the tails of distributions using variance as a key parameter. Delve into examples with geometric random var
0 views • 27 slides
Understanding Real Analysis: Intervals, Bounds, and Problem-solving
Explore the concepts of intervals and bounds in real analysis, including open and closed intervals, semi-closed intervals, least upper bound, and greatest lower bound. Learn how to solve problems based on intervals and bounded sets through detailed explanations and examples.
0 views • 11 slides
Understanding Real Analysis: Intervals, Bounds, and Problem Solving
Explore the world of real analysis through intervals, bounds, and problem-solving techniques. Learn about open intervals, closed intervals, semi-closed intervals, infinite intervals, least upper bound, greatest lower bound, and solve problems based on intervals and bounded sets. Enhance your underst
1 views • 11 slides
Exploring Att&ck Matrix: Engage Ludicrous Speed
Dive into the world of the Mitre Att&ck Matrix, where crazy ampersands and Trebuchet Font cues you in on how to engage Ludicrous Speed and understand the basics of attacker/adversary tactics, techniques, and common use cases. Explore matrices, prevent attacks, and work programmatically with Att&ck u
0 views • 26 slides
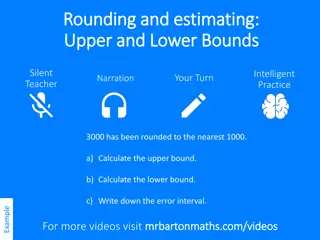
Understanding Rounding and Estimating: Upper and Lower Bounds Example
Explore how to determine upper and lower bounds after rounding numbers to the nearest 1000 or 100. Learn how to calculate the error intervals and practice your skills with provided examples. Gain a clear understanding of rounding to the nearest whole number and how to identify boundaries in estimati
2 views • 4 slides
Understanding Stability and Generalization in Machine Learning
Exploring high probability generalization bounds for uniformly stable algorithms, the relationship between dataset, loss function, and estimation error, and the implications of low sensitivity on generalization. Known bounds and new theoretical perspectives are discussed, along with approaches like
0 views • 8 slides
Generalization Bounds and Algorithms in Machine Learning
Generalization bounds play a crucial role in assessing the performance of machine learning algorithms. Uniform stability, convex optimization, and error analysis are key concepts in understanding the generalization capabilities of algorithms. Stability in optimization, gradient descent techniques, a
0 views • 16 slides
Investigating Power and Area Reduction Bounds in 3D Integration
This study focuses on establishing upper bounds for power and area reduction in 3D Integrated Circuits (3DICs), specifically exploring the benefits of multi-tier 3DICs compared to lower-tier configurations. Previous works and evaluations on power and wirelength benefits are discussed, highlighting t
0 views • 24 slides
Understanding Upper and Lower Bounds in Rounding and Estimating
Learn how to calculate upper and lower bounds and error intervals when rounding numbers to significant figures. Practice rounding to different significant figures and apply the concept to various numerical values. Develop a solid grasp of estimation techniques with informative examples and visual ai
1 views • 5 slides
Abundant Life: Key to Success Through God's Help
Embrace the abundant life prepared for success through knowing that God sees, hears, and strengthens us. His help subdues our adversary, and Jesus advocates for us. Revelation of His thoughts empowers us to overcome challenges and achieve success, reflecting God's desire for our prosperity and victo
0 views • 10 slides
Insights into Advanced Algorithmic Problems
Delve into discussions surrounding complex algorithmic challenges, such as the limitations in solving the 3-SAT problem within specific time bounds, the Exponential Time Hypothesis, proving lower bounds for algorithms in various scenarios, and exploring approximation ratios in algorithm design. Thes
1 views • 65 slides
Understanding Tail Bounds in Probability for Computing
Tail bounds in probability theory play a crucial role in analyzing random variables and understanding the behavior of certain events. This content explores the concept of tail bounds, their importance through examples, and the derivation of upper bounds on tails. Markov's inequality is also discusse
0 views • 31 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Dual System Encryption: Concept, History, and Recent Works
Explore the concept and history of dual system encryption, including the strategy of security proof, partitioning technique, and the adaptive security model. Understand how security is ensured through mathematical problem complexities and adversary challenges.
0 views • 29 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
IEEE 802.11-17/1373r1 PHY Security Overview
This document outlines the security requirements for the IEEE 802.11-17/1373r1 protocol, focusing on authentication, encryption algorithms, key management, and message integrity in both associated and unassociated states. It also addresses securing against adversaries with specified response times,
0 views • 10 slides
Analysis of Onion Routing Security and Adversary-based Metrics
In this comprehensive analysis, the security aspects of Onion Routing are scrutinized along with adversary-based metrics. Various security vulnerabilities such as compromised relays and potential attacks on the first and last routers are examined. Existing metrics like entropy coefficients and proba
0 views • 21 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
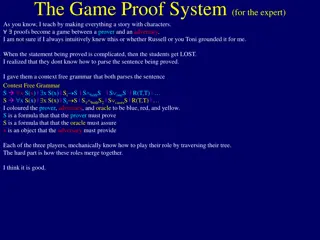
Game Proof System for Experts: Interactive Storytelling Approach
Teaching proofs as a game between a prover, an adversary, and an oracle using context-free grammar and character roles. This system helps students understand complex statements by breaking them down and providing interactive gameplay for better comprehension and engagement.
0 views • 14 slides
Numerical Abstract Domain with Max Operator in Timing Analysis
Explore a numerical abstract domain based on expression abstraction and the Max operator with applications in timing analysis. The challenges in timing analysis, such as disjunctive and non-linear bounds, are discussed along with simple examples illustrating these concepts. The difficulty of proving
0 views • 21 slides
Analysis on Oil's Impact on Civil War and State Weakness
The analysis delves into the potential causal effects of oil on civil war and state weakness. By examining the observed data and establishing bounds, it suggests that oil could either significantly reduce wars or have a small positive effect. Furthermore, it explores how oil may lead to war through
1 views • 6 slides
Additive Combinatorics Approach to Log-Rank Conjecture in Communication Complexity
This research explores an additive combinatorics approach to the log-rank conjecture in communication complexity, addressing the maximum total bits sent on worst-case inputs and known bounds. It discusses the Polynomial Freiman-Ruzsa Conjecture and Approximate Duality, highlighting technical contrib
0 views • 9 slides
Understanding Upper and Lower Bounds in Measurements
Explore the concept of upper and lower bounds in measurements through examples involving rounding numbers and calculating boundaries for different units like centimeters, millimeters, and meters. Learn how to determine the range within which a rounded number falls for both discrete and continuous da
0 views • 9 slides
Understanding Upper and Lower Bounds in Mathematics
Exploring the concept of upper and lower bounds in mathematics, this content discusses how numbers are rounded to the nearest whole number and identifies the possible maximum and minimum values. It also provides examples and rules for finding upper and lower bounds, as well as practical applications
0 views • 6 slides
Exploring Circuit Size Bounds in Complexity Theory
The article delves into Shannon's Theorem in Complexity Theory, discussing the upper bounds of circuit sizes for Boolean functions of n variables. It explores the 1-1 correspondence with 0-1 strings of length 2n and how Boolean functions can be expressed as CNF or DNF formulas. The computation of th
2 views • 19 slides
Advanced Techniques for Heavy Hitters Detection in Insertion Streams
Beating CountSketch algorithms, like those presented by David P. Woodruff and team, offer innovative solutions for identifying heavy hitters in insertion streams with minimal space complexity. Guarantees such as L1 and L2 outputs and the CountSketch approach are explored to achieve efficient heavy h
0 views • 18 slides
Understanding Lower Bounds in the Cell Probe Model
Exploring the concept of lower bounds for static data structures, this content delves into the tradeoffs between query time and space efficiency. It discusses the need for proving lower bounds, the model of data structures, and how CPUs access memory in computational devices. Kasper Green Larsen fro
0 views • 45 slides
Understanding Rule 4: Ball In Play, Dead Ball, Out of Bounds
Exploring Rule 4 of the game rules, this article delves into Ball In Play, Dead Ball, and Out of Bounds situations, discussing key scenarios like legal snaps, live ball becoming dead, and the impact of inadvertent whistles. It covers rules regarding ball positioning, player actions, and referee sign
0 views • 14 slides
Communication Lower Bounds of Key-Agreement Protocols
Key-agreement protocols play a vital role in secure communication between parties. This document explores lower bounds of key-agreement protocols through density increment arguments, idealization of symmetric primitives, Merkle puzzles, and the impact of communication bits between Alice and Bob. Var
0 views • 10 slides
Lower Bounds for Small Depth Arithmetic Circuits
This work explores lower bounds for small-depth arithmetic circuits, jointly conducted by researchers from MSRI, IITB, and experts in the field. They investigate the complexity of multivariate polynomials in arithmetic circuits, discussing circuit depth, size, and the quest for an explicit family of
0 views • 114 slides
Lower Bounds on Sampling Good Codes in Bounded-Depth Circuits
Bounded-depth circuits are proven unable to sample or approximate good codes effectively. This work delves into lower bounds, showcasing that bounded families of circuits face limitations in computing specific functions or sampling distributions. The example of Parity in AC0 circuits illustrates the
0 views • 21 slides
Advanced Techniques for Orthogonal Skyline Counting Queries
Advanced techniques for orthogonal skyline counting queries discuss optimal planar solutions, dividing and conquering for topmost point identification, efficient vertical slab counting, succinct data structures for prefix sums and range maxima, upper bounds on degree and multi-slab queries, as well
0 views • 11 slides
Understanding Measurement Bounds and Accuracy
Exploring the concepts of significant figures, bounds, accuracy, and ranges in measurement. From determining the smallest and largest possible lengths to finding lower and upper bounds based on accuracy, this content focuses on practical exercises and explanations to enhance understanding. Learn how
0 views • 6 slides
Understanding Propositional Proof Complexity and Lower Bounds
Studies focus on the intractability of propositional proof complexity, exploring the power of proof systems to verify tautologies. Discussion on known lower bounds and challenges in proving hardness of certain tautologies.
0 views • 23 slides