Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
CS 404/504 Special Topics
Adversarial machine learning techniques in text and audio data involve generating manipulated samples to mislead models. Text attacks often involve word replacements or additions to alter the meaning while maintaining human readability. Various strategies are used to create adversarial text examples
1 views • 57 slides
Understanding Deep Generative Models in Probabilistic Machine Learning
This content explores various deep generative models such as Variational Autoencoders and Generative Adversarial Networks used in Probabilistic Machine Learning. It discusses the construction of generative models using neural networks and Gaussian processes, with a focus on techniques like VAEs and
9 views • 18 slides
Unleash the Power of the DP3150 Facing Lathe from Mudar M Metalworking Machine T
Elevate Your Metalworking Operations with the DP3150 Facing Lathe from Mudar M Metalworking Machine Tools Trading!\nEnhance your used metalworking machine tools capabilities with the DP3150 Facing Lathe available at Mudar M Metalworking Machine Tools Trading!\nExplore our inventory and discover to
1 views • 7 slides
Advanced Machine Learning: Data Preparation and Exploration Part 1
This lecture on advanced machine learning covers topics such as the ML process in detail, data understanding, sources, types, exploration, preparation, scaling, feature selection, data balancing, and more. The ML process involves steps like defining the problem, preparing data, selecting and evaluat
0 views • 80 slides
Exploring Adversarial Machine Learning in Cybersecurity
Adversarial Machine Learning (AML) is a critical aspect of cybersecurity, addressing the complexity of evolving cyber threats. Security analysts and adversaries engage in a perpetual battle, with adversaries constantly innovating to evade defenses. Machine Learning models offer promise in combating
0 views • 43 slides
Understanding Domain Adaptation in Machine Learning
Domain adaptation in machine learning involves transferring knowledge from one domain to another. It addresses the challenge of different data distributions in training and testing sets, leading to improved model performance. Techniques like domain adversarial training and transfer learning play a k
0 views • 16 slides
CSEP 546 Machine Learning Course Overview
This course, led by Geoff Hulten and TAs Alon Milchgrub and Andrew Wei, delves into important machine learning algorithms and model production techniques. Topics covered include logistic regression, feature engineering, decision trees, intelligent user experiences, computer vision basics, neural net
1 views • 10 slides
Exploration of Learning and Privacy Concepts in Machine Learning
A comprehensive discussion on various topics such as Local Differential Privacy (LDP), Statistical Query Model, PAC learning, Margin Complexity, and Known Results in the context of machine learning. It covers concepts like separation, non-interactive learning, error bounds, and the efficiency of lea
0 views • 14 slides
Seminar on Machine Learning with IoT Explained
Explore the intersection of Machine Learning and Internet of Things (IoT) in this informative seminar. Discover the principles, advantages, and applications of Machine Learning algorithms in the context of IoT technology. Learn about the evolution of Machine Learning, the concept of Internet of Thin
0 views • 21 slides
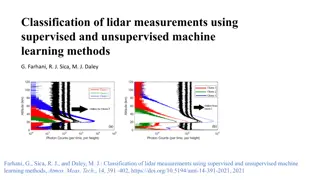
Classification of Lidar Measurements Using Machine Learning Methods
This study focuses on classifying lidar measurements using supervised and unsupervised machine learning methods. By utilizing machine learning, specifically supervised learning, the researchers trained a prediction function to automatically label unlabeled lidar scans. They conducted steps to implem
0 views • 16 slides
Understanding Adversarial Attacks in Machine Learning
Adversarial attacks in machine learning aim to investigate the robustness and fault tolerance of models, introduced by Aleksander Madry in ICML 2018. This defensive topic contrasts with offensive adversarial examples, which seek to misclassify ML models. Techniques like Deep-Fool are recognized for
0 views • 29 slides
Understanding Adversarial Machine Learning Attacks
Adversarial Machine Learning (AML) involves attacks on machine learning models by manipulating input data to deceive the model into making incorrect predictions. This includes creating adversarial examples, understanding attack algorithms, distance metrics, and optimization problems like L-BFGS. Var
0 views • 88 slides
Understanding Adversarial Threats in Machine Learning
This document explores the world of adversarial threats in machine learning, covering topics such as attack nomenclature, dimensions in adversarial learning, influence dimension, causative and exploratory approaches in attacks, and more. It delves into how adversaries manipulate data or models to co
0 views • 10 slides
Limitations of Deep Learning in Adversarial Settings
Deep learning, particularly deep neural networks (DNNs), has revolutionized machine learning with its high accuracy rates. However, in adversarial settings, adversaries can manipulate DNNs by crafting adversarial samples to force misclassification. Such attacks pose risks in various applications, in
0 views • 38 slides
Adversarial Risk Analysis for Urban Security
Adversarial Risk Analysis for Urban Security is a framework aimed at managing risks from the actions of intelligent adversaries in urban security scenarios. The framework employs a Defend-Attack-Defend model where two intelligent players, a Defender and an Attacker, engage in sequential moves, with
1 views • 26 slides
Scientific Machine Learning Benchmarks: Evaluating ML Ecosystems
The Scientific Machine Learning Benchmarks aim to assess machine learning solutions for scientific challenges across various domains like particle physics, material sciences, and life sciences. The process involves comparing products based on large experimental datasets, including baselines and mach
1 views • 35 slides
Mastering Slot Machine Programming_ A Complete Guide
Mastering Slot Machine Programming: A complete guide to developing slot machine games. Learn key concepts, coding techniques, and best practices for creating engaging and successful slot machine games.\n\nSource>>\/\/ \/slot-machine-programming\n
0 views • 5 slides
Adversarial Learning in ML: Combatting Internet Abuse & Spam
Explore the realm of adversarial learning in ML through combating internet abuse and spam. Delve into the motivations of abusers, closed-loop approaches, risks of training on test data, and tactics used by spammers. Understand the challenges and strategies involved in filtering out malicious content
0 views • 13 slides
Distillation as a Defense Against Adversarial Perturbations in Deep Neural Networks
Deep Learning has shown great performance in various machine learning tasks, especially classification. However, adversarial samples can manipulate neural networks into misclassifying inputs, posing serious risks such as autonomous vehicle accidents. Distillation, a training technique, is proposed a
3 views • 31 slides
Understanding Robustness to Adversarial Examples in Machine Learning
Explore the vulnerability of machine learning models to adversarial examples, including speculative explanations and the importance of linear behavior. Learn about fast gradient sign methods, adversarial training of deep networks, and overcoming vulnerabilities. Discover how linear perturbations imp
0 views • 37 slides
Adversarial Attacks on Post-hoc Explanation Methods in Machine Learning
The study explores adversarial attacks on post-hoc explanation methods like LIME and SHAP in machine learning, highlighting the challenges in interpreting and trusting complex ML models. It introduces a framework to mask discriminatory biases in black box classifiers, demonstrating the limitations o
2 views • 18 slides
Understanding Game Playing and Adversarial Search at University of Berkeley
Delve into the realm of game playing and adversarial search at the University of Berkeley to understand the complexities of multi-agent environments. Explore the concepts of competitive MA environments, different kinds of games, and the strategic decision-making processes involved in two-player game
0 views • 81 slides
Understanding Machine Learning: A Comprehensive Overview
Machine learning has evolved significantly over the decades, driven by concepts like Neural Networks, Reinforcement Learning, and Deep Learning. This technology enables machines to learn from past data to make predictions. Activities in machine learning involve data exploration, preparation, model t
0 views • 16 slides
Introduction to Machine Learning in BMTRY790 Course
The BMTRY790 course on Machine Learning covers a wide range of topics including supervised, unsupervised, and reinforcement learning. The course includes homework assignments, exams, and a real-world project to apply learned methods in developing prediction models. Machine learning involves making c
0 views • 62 slides
Understanding Zero-Shot Adversarial Robustness for Large-Scale Models
Pretrained large-scale vision-language models like CLIP show strong generalization on unseen tasks but are vulnerable to imperceptible adversarial perturbations. This work delves into adapting these models for zero-shot transferability in adversarial robustness, even without specific training on unk
0 views • 18 slides
Understanding Learning in Games Seminar
Explore the intersection of Game Theory and Machine Learning in the context of Learning in Games. Discover how decision-makers adapt strategies to maximize their utility, with emphasis on Multi-Agent Learning. Topics include AI for Board Games, Equilibrium Computation in Auctions, and various soluti
0 views • 11 slides
Understanding Processor Cycles and Machine Cycles in 8085 Microprocessor
Processor cycles in microprocessors like 8085 involve executing instructions through machine cycles that are essential operations performed by the processor. In the 8085 microprocessor, there are seven basic machine cycles, each serving a specific purpose such as fetching opcodes, reading from memor
0 views • 17 slides
Evaluating Adaptive Attacks on Adversarial Example Defenses
This content discusses the challenges in properly evaluating defenses against adversarial examples, highlighting the importance of adaptive evaluation methods. While consensus on strong evaluation standards is noted, many defenses are still found to be vulnerable. The work presents 13 case studies o
0 views • 9 slides
Understanding Adversarial Search in Artificial Intelligence
Adversarial search in AI involves making optimal decisions in games through concepts like minimax and pruning. It explores the strategic challenges of game-playing, from deterministic turn-taking to the complexities of multi-agent environments. The history of computer chess and the emergence of huma
0 views • 56 slides
Foundations of Artificial Intelligence: Adversarial Search and Game-Playing
Adversarial reasoning in games, particularly in the context of artificial intelligence, involves making optimal decisions in competitive environments. This module covers concepts such as minimax pruning, game theory, and the history of computer chess. It also explores the challenges in developing AI
0 views • 56 slides
Supervised Machine Learning for Data Management in Archives
In this study by Jennifer Stevenson, a supervised machine learning approach is proposed for arrangement and description in archives, specifically focusing on the DTRIAC collection which contains a vast amount of historical documents related to nuclear technology. The aim is to expedite the catalogin
1 views • 15 slides
Social Implications of Machine Learning in Anthropological Research
Exploring the intersection of machine learning and anthropology, this presentation delves into the evolving role of data scientists as modern-day anthropologists studying big data through machine learning. It emphasizes the need for on-the-ground ethnographic analysis to understand the impact of the
0 views • 27 slides
Learning from Demonstration in the Wild: A Novel Approach to Behavior Learning
Learning from Demonstration (LfD) is a machine learning technique that can model complex behaviors from expert trajectories. This paper introduces a new method, Video to Behavior (ViBe), that leverages unlabelled video data to learn road user behavior from real-world settings. The study presents a v
0 views • 19 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Understanding Machine Learning: Types and Examples
Machine learning, as defined by Tom M. Mitchell, involves computers learning and improving from experience with respect to specific tasks and performance measures. There are various types of machine learning, including supervised learning, unsupervised learning, and reinforcement learning. Supervise
0 views • 40 slides
Exploring Adversarial Search and Minimax Algorithm in Games
Competitive games create conflict between agents, leading to adversarial search problems. The Minimax algorithm, used to optimize player decisions, plays a key role in analyzing strategies. Studying games offers insights into multiagent environments, economic models, and intellectual engagement. The
0 views • 17 slides
Efficient Image Compression Model to Defend Adversarial Examples
ComDefend presents an innovative approach in the field of computer vision with its efficient image compression model aimed at defending against adversarial examples. By employing an end-to-end image compression model, ComDefend extracts and downscales features to enhance the robustness of neural net
0 views • 16 slides
Lifelong and Continual Learning in Machine Learning
Classic machine learning has limitations such as isolated single-task learning and closed-world assumptions. Lifelong machine learning aims to overcome these limitations by enabling models to continuously learn and adapt to new data. This is crucial for dynamic environments like chatbots and self-dr
0 views • 32 slides