Active Directory Delegation, cionsystems.com
The Active Directory Manager Pro features active directory delegation which can help organizations to reduce the number of high privilege accounts thereby reducing risk and enhancing security. https:\/\/shorturl.at\/uLNP7
2 views • 7 slides
Active Directory Password Reset, cionsystems.com
It is a great solution for identity administration and controlling access. http:\/\/tinyurl.com\/krry4n3
3 views • 2 slides
Active Directory Auditing, cionsystems.com
A very simple and cost effective solution that makes active directory auditing easy proactively tracking and giving change alerts. https:\/\/rb.gy\/ttey9o
2 views • 7 slides
Active Directory Backup and Recovery, cionsystems
Sometimes human error, technology failures and malicious actions can easily corrupt the directory. \/\/rb.gy\/klwubf
1 views • 7 slides
Arkansas Community Mental Health Center Directory
The Arkansas Community Mental Health Center Directory provides contact information for various mental health providers in different areas of Arkansas, including services offered and emergency contact numbers. The directory includes details for Ouachita Behavioral Health and Wellness, Counseling Asso
0 views • 7 slides
Active Directory Password Reset, cionsystems.com
It is a great solution for identity administration and controlling access. \/\/rb.gy\/upx1mj
3 views • 7 slides
Understanding Active Directory: Key Components and Security Considerations
Active Directory is a crucial component in Windows networks, providing centralized resource management, authentication, and authorization services. Key components include objects, domains, domain controllers, OUs, forests, and group policies. Understanding the data store, NTDS.dit file, partitions,
6 views • 68 slides
Active Directory Backup and Recovery, cionsystems
Sometimes human error, technology failures and malicious actions can easily corrupt the directory. \/\/tinyurl.com\/5xpuutyd
3 views • 7 slides
Active Directory Self Service Password Reset Tool, cionsystems
It provides the feature of delegated web access administration, self-registration, self-service and password management. \/\/rb.gy\/1tjfv5
2 views • 2 slides
Efficient Reflect & Reset Strategies for Successful OKR Cycles
Prepare for your upcoming Reflect & Reset workshop to ensure a more efficient and effective OKR session. Learn strategies to accurately track progress, identify key learnings, and involve your team members for a successful OKR cycle. Understand the critical steps of defining objectives and key resul
0 views • 16 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Understanding Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
1 views • 11 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Northampton General Hospital NHS Trust Post Covid-19 Reset Overview
Northampton General Hospital NHS Trust is prioritizing patient safety and excellence in healthcare post Covid-19. Their reset and recovery phase aims to resume urgent non-Covid services safely, focusing on cancer care, diagnostics, and outpatient treatments. The hospital has maintained 80% of pre-Co
1 views • 12 slides
Reset Internet Banking Transaction Password Online Guide
Complete your internet banking transaction password reset online using your ATM card details and registered mobile number for OTP verification. Follow the step-by-step instructions provided with images for a successful reset process and confirmation.
0 views • 8 slides
Understanding Directory Structures in Operating Systems
Directory structures play a crucial role in operating systems, organizing files, and supporting essential operations like file search, creation, deletion, listing, and traversal. This content explores single-level and two-level directory structures, addressing their benefits and limitations in manag
2 views • 23 slides
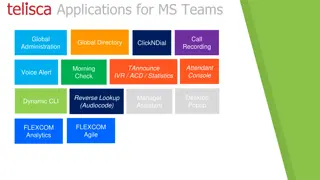
Telisca Suite: Enhancing MS Teams Integration with Advanced Tools
Explore the Telisca suite of applications and tools designed to enhance MS Teams functionality. From call recording to global directory management, Azure authentication, and gateway configurations, Telisca offers a comprehensive solution for optimizing communication and collaboration within the Team
0 views • 92 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
How to Login to BridgeIT & Create MAPFRE Password
Learn how to login to BridgeIT on August 6th at bridgeit.mapfre.com:4430 and create or reset your MAPFRE password. Follow the step-by-step instructions provided using your MAPFRE username. A dedicated support helpline is available for any login difficulties.
0 views • 5 slides
Guide to Logging in to SIRA UW with MAPFRE Credentials
Learn how to access SIRA UW platform using your MAPFRE credentials starting August 6th. Follow the steps for creating and resetting your password, ensuring a smooth login process. Utilize your MAPFRE username and be prepared to wait 10 minutes post password reset. Reach out to the dedicated support
0 views • 5 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
Mastering Active Directory Management with PowerShell
Learn essential tips and techniques for managing Active Directory using PowerShell, including starting tips, staying up-to-date with PowerShell versions, methods of management, exploring Active Directory commands, getting information from AD, and selecting, sorting, and exporting data efficiently.
0 views • 15 slides
Understanding BQ76952 Overcurrent Detection and Analog Data Reset
The BQ76952 device features a protective mechanism where reaching the OCD1 threshold triggers a reset of OTPB and analog data. This was observed during an OCD test, where cell voltages exceeded specified thresholds. While it's not explicitly stated in the specs, exceeding the voltage threshold may b
0 views • 16 slides
Understanding User Accounts and Directory Services in Network Computing
Explore the role of user accounts and directory services in network-centric computing infrastructure. Learn about Directory Servers, User Administration in Unix, and the concept of Group Accounts in Unix. Discover how Directory Services provide centralized repositories for managing information, enab
0 views • 9 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Understanding Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
SecDir: A Secure Directory to Defeat Directory Side-Channel Attacks
SecDir introduces a secure directory design to mitigate directory side-channel attacks, a critical security threat. By reassigning part of the conventional directory storage to per-core private directories, SecDir aims to block directory interference between processes and enhance security in cache h
0 views • 49 slides
Platinum Partner Package Benefits for RESET Event
Elevate your brand visibility and engagement as a Platinum Partner at RESET event. Enjoy prime logo placement, exclusive marketing opportunities, and a fully-branded 3D interactive virtual stand to showcase your company. Gain access to detailed attendee data for a lasting impact and ROI. Watch a dem
0 views • 4 slides
Essential Windows Enterprise Services Overview
Exploring Windows Enterprise Services, the Introductions to UNM Directory Services, the LAMB Authoritative Source of Information for AD processes, and the benefits of RSAT (Remote Server Administration Tools). Discover the delegation of responsibilities in OU structures and the nuances of Group Type
0 views • 16 slides
Understanding Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Understanding Active/Active SQL Clusters for High Availability
Discover the importance of Active/Active SQL clusters for ensuring 24/7 availability of your database servers. Learn about the benefits, setup process, and the high availability solution it offers for the entire server instance. Follow a detailed step-by-step guide for setting up SQL Active/Active c
0 views • 18 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Understanding Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
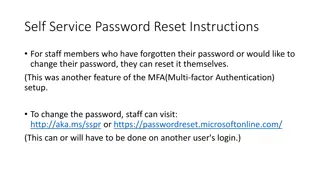
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides