Understanding Checksums in Packet Headers
Checksums play a crucial role in validating the integrity of packet headers in various protocols. This tutorial explores the concept of checksums, the use of algorithms like CRC, and the process of recalculating checksums to ensure data integrity in network communications.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Lab 8: Checksum Recalculation and Packet Deparsing Jorge Crichigno College of Engineering and Computing, University of South Carolina A Hands-on Tutorial on P4 Programmable Data Planes Tuesday March 7, 2023 1
Checksum Recalculation and Packet Deparsing Lab activities are described in Lab 8, P4 Programmable Data Plane Switches (BMv2) lab series 2
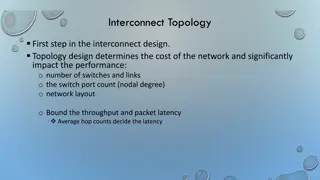
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Packet headers 3
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Packet headers Hash algorithm (e.g., CRC) H Checksum
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Receiver Packet headers Packet headers Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Checksum Checksum 5
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Receiver Packet headers Packet headers Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Checksum Checksum Equal? Checksum verified, accept packet 6
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Receiver Packet headers Packet headers Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Checksum Checksum Equal? Checksum incorrect, reject packet 7
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Programmable Switch Receiver Original headers Modified headers Packet headers Packet headers action Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Hash algorithm (e.g., CRC) H Checksum Checksum 8
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Programmable Switch Receiver Original headers Modified headers Packet headers Packet headers action Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Hash algorithm (e.g., CRC) H Checksum Checksum 9
Checksums Several protocols use checksums to validate the integrity of the packet headers A checksum is a small value derived using a checksum algorithm such as the Cyclic Redundancy Check (CRC) Sender Programmable Switch Receiver Original headers Modified headers Packet headers Packet headers action Hash algorithm (e.g., CRC) Hash algorithm (e.g., CRC) H H Hash algorithm (e.g., CRC) H Checksum Checksum Equal? Checksum Checksum verified, accept packet 10
Lab Topology and Objectives The topology consists of three hosts: h1, h2, and h3; one P4 switch: s1 The P4 program modifies the headers of the packet The P4 program recomputes the checksum of the updated headers 11