Demystifying Cybersecurity: Protecting Your Agency and Getting Started
Learn how to protect your agency from cyber threats by conducting Cyber Threat Assessments, identifying vulnerabilities, and creating an effective Cyber Incident Action Plan. Understand the steps involved in assessing threats, analyzing risks, and responding to cyber-attacks to safeguard your organization's data and operations.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
CYBERSECURITY - DEMYSTIFIED PROTECTING YOUR AGENCY AND HOW TO GET STARTED
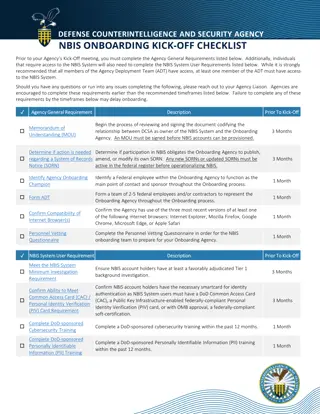
GETTING STARTED CYBER TREAT ASSESSMENTS What is a Cyber Threat Assessment? A Cyber Threat Assessment is a specialized version of a Risk Assessment. Agencies and Organizations should be taking a close look at their computer systems, remote access services and cloud based accounts. From exposing weaknesses in systems to issues with compliance, a cybersecurity threat assessment enables organizations to uncover hidden vulnerabilities in people, processes and technology before a malicious actor can exploit them. 1 1https://www.optiv.com/security-threat-assessment
CYBER THREAT ASSESSMENTS WHAT DO YOU NEED TO DO? #1 Characterize EACH of your data systems (what kind of data, who uses it, vendor, retention policy, where does the data come from and where does it go, where is it stored, where and how is it backed-up), pre-determine the data recovery process #2 Identify threats and exploits (i.e. unauthorized access, data exposure, and disruption of service) #3 Determine risk impact (impacts if the threat was exercised: High, Medium, or Low) #4 Analyze the environment (identify threat prevention, detection, mitigation) #5 Determine a likelihood rating (how likely is a given exploit) #6 Calculate your risk rating Impact (if exploited) * Likelihood (of exploit) = Risk Rating
CYBER INCIDENT ACTION PLAN Your agency has done all the right things, Cybersecurity Threat Assessments, end user training but the bad actors have succeeded and you find yourself a victim of a cyber-attack. Now what do you do? You follow your Cybersecurity Incidence Response Plan! An effective response plan needs to guide company personnel at all levels in managing a potential data breach in a way that supports rapid and thoughtful response activities.
CYBER INCIDENT ACTION PLAN WHERE TO START? Phase 1: Prepare This phase will take the most work, it s not easy! Whether an agency prepares their own Incident Action Plan, or if a professional contract is put in place, there are steps to consider in plan development. Before beginning formal planning, ECC, PSAP/9-1-1, LMR managers should discuss cyber threats with their agency s or department s senior managers, their servicing IT departments, IT vendors, and with budget officials to ensure planning is understood at various management levels, especially as regards the issue of ransom demands. These policy discussions can help define and qualify responsibilities (especially vendors contractual responsibilities for cyber security) before having to deal with an attack.
PHASE 2: IDENTIFY Identification or detection of a data breach looks for deviations from normal operations and activities.
PHASE 3: CONTAIN When a breach has been detected, the normal reaction is to fix it NOW. This is when an agencies training kicks in FOLLOW YOUR INCIDENT RESPONSE PLAN and training! Evidence can be inadvertently destroyed if you don t follow the proper steps. Follow the advice and direction of your computer forensic team. Remember: DON T panic DON T make hasty decisions DON T wipe and re-install your systems (yet)
PHASE 4: ERADICATE The vulnerability that led to the breach needs to be eliminated. This can be agency policies, procedures, or a technology solution. All traces of malware should be securely removed, and systems should be patched and updated. If this activity is outside the scope of an agencies IT department, additional subject matter experts may be needed and should be noted in the Incident Response Plan.
PHASE 5: RECOVER Once ALL traces of the breach have been eliminated, systems are patched, updated and tested, THEN the compromised system can be reintroduced. (This can take weeks or even months) This step s complexity greatly depends on a successful off-site, off-network back up plan
PHASE 6: REVIEW It is critical that an after-action meeting is held and a report is developed. Learn what worked or didn t work from the Incident Response Plan and make any necessary adjustments.
HELP I CANT DO ALL OF THIS! Pick one or two things that you can do: Increase (or start) personnel cybersecurity awareness training Strong passwords with an expiration cycle Personal device and USB policies Learning to monitor for and reporting the signs of a system breach Unexpected user lockouts Repeated system crashes Abnormal behavior during browsing: popups, redirects, etc. Everyone needs to know the plan BEFORE something happens Display Ransomware Posters for personnel awareness
NEW CISA RANSOMWARE GUIDANCE It s not just Ransomware This document provides best practices for preventing network infection General best practices and network hardening guidance Template Response Plan checklist https://www.cisa.gov/sites/default/files/p ublications/CISA_MS- ISAC_Ransomware%20Guide_S508C.pdf
RESOURCES ARE AVAILABLE Cybersecurity Essentials Framework and toolkits provide great resources for each step of the process https://www.cisa.gov/publication/cisa-cyber-essentials https://www.cisa.gov/publication/cyber-essentials-toolkits (each includes great resources) Ransomware Posters designed for PSAPs, but are relevant to every radio dispatch facility and agency office https://www.dps.texas.gov/IOD/interop/swicDocuments.htm Texas SWIC Office Guidance Documents: https://www.dps.texas.gov/IOD/interop/swicDocuments.htm (posted in SWIC Document Library soon) Getting Started Cyber Threat Assessment Getting Started Cyber Incidence Response Plan