Comprehensive Overview of Distributed Intrusion Detection System (DIDS)
Explore the Distributed Intrusion Detection System (DIDS) introduced by Mohammad Hossein Salehi and Kiumars Talaee. Learn about the significance, working, and different types of IDS within DIDS like HIDS, NIDS, and agent-based IDS. Understand the division, information sources, and roles of client-based (HIDS) and network-based (NIDS) systems in enhancing cybersecurity. Delve into the key features, detection capabilities, and performance considerations of DIDS components for effective threat mitigation.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
DISTRIBUTED INTRUSION DETECTION SYSTEM Mohammad Hossein Salehi and Kiumars Talaee Computer Engineering Department, Mazandaran University of Science and Technology, Distributes Systems Class Seminar Supervisor: Hadi Salimi mhss.pro@gmail.com , kiumars.talaee@gmail.com
DIDS Introduction to DIDS
Why DIDS ? DIDS Grow of Web Based Technology and Network Distributed Attacks Critical Information on Web Identification Availability
The Working of IDS DIDS Sniff Network Traffic Event Sensor Intrusion Detection Signature base Anomaly base Alert Generator Hardware IDS High Secure Expensive Software IDS Work Easily Cheaper
The Division of IDS DIDS Information Source Based Strategist Analysis Based Time Event Based Structure Based The kinds of Response to Intrusion
The Information Source Based IDS DIDS Audit trails Network Packets Application logs Wireless Sensor Traffic Sensor Alerts Therefore We Have three Kind of Division HIDS NIDS DIDS (Agent based IDS)
The Information Source Based IDS DIDS Therefore We Have three Kind of Division : HIDS NIDS DIDS (Agent based IDS)
Client Based or HIDS DIDS Just secure The Host Increase the IDS Performance with Decrease The roles Have lower traffic than NIDS and DIDS Working on Application Layer And can t detection many of attacks on lower layer
Network Based or NIDS DIDS Collecting and Analyzed in Network Traffic Source Information Have a Two Segment Monitor Agent Maybe Have a Management Console Have a Problem in upper than 100 Mbps The Scope Dependency on local Segments This have good Performance on DoS Attacks If Network Traffic have a Encryption can not work
Agent Based or DIDS DIDS Collecting and Analyzed in NIDS and HIDS Have a Several NIDS or HIDS or Hybrid of these with one Central Management Station Each IDS Sending Report to Central Management Station Central Management Station Analyzed the Reports and Generate the Alert for Security Officer Central Management Station Update the Role Database In this system both collection and Analyzed the data have a Distributed Structure
The Picture of DIDS DIDS
Strategist Analysis Based DIDS Anomaly Based Detection or Statistical based Signature based Detection
Time Event Based DIDS Real time Detection Response to the Attacks in Real time Offline Detection First Monitor and store the data and then Analyzed and generate the Alerts
Stracture Based Division DIDS Centralized architecture Single Monitored System Distributed Architecture Multiple Monitored Systems
Response Based Division DIDS Active Response Passive Response
Distributed Intrusion Detection System DIDS Intrusion Detection System with Distributed Planning Easily can work on fast Network Traffic In Distributed Systems we have little single point of failure DIDS with Distributed Sensors : ASAX (Mouinji et al., 1995) NSTAT (Kemmerer, 1997) DIDS (Snapp etal., 1999) NetSTAT (Vigna and Kemmerer, 1999) DIDS with Distributed Sensors and Level Architecture: EMERALD (Porras and Neumann, 1997) GRIDS (Stanford _ Chen et al ., 1996) AAFID (spafford and Zamboi, 2000) CIDF (Stanford _ Chen et al ., 1998) MADAM ID (Ning et al., 2002)
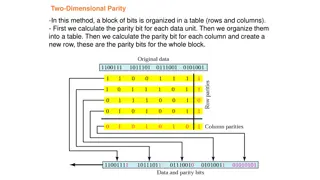
Distributed Intrusion Detection System DIDS A Hierarchical Architecture of Distributed Intrusion Detection System with free communication between layers
Distributed Intrusion Detection System DIDS DIDS Projects with Autonomous Agents AAFID (Autonomous Agent for Intrusion Detection) in Purdu University IDA (Intrusion Detection Agent System) Japan IT Agency JAM (Java Agent for Meta learning) in Columbia University
Mobile Agent in IDS DIDS Overcoming Network Latency Reducing Network Load Autonomous and Asynchronous Execution Dynamic Adaption Platform Independence Protocol Encapsulation
Two Usual Attack in Network DIDS DDoS or Distributed Denial of Service Probing
DIDS Problems DIDS Increase the Analyze Speed Security in Sending Management Packets Expensive Traffic Monitoring Rate
References DIDS [1] Ilija Basicevic, Miroslav Popovic, Vladimir Kovacevic ,"The Use of Distributed Network-Based IDS Systems in Detection of Evasion Attacks",IEEE Advanced Industrial Conference on elecommunications, AICT 2005, Lisbon, Portugal, July 17- 20, 2005 [2] Ashok Kumar Tummala, Parimal Patel, "Distributed IDS using Reconfigurable Hardware," ipdps, pp.426, 2007 IEEE International Parallel and Distributed Processing Symposium, 2007 [3] Kabiri, Peyman; Ghorbani, Ali, A Rule-Based Temporal Alert Correlation System , International Journal of Network Security, Vol. 5, No.1, pp. 66-72, July 2007 [4] Ajith Abraham, Ravi Jain, Johnson Thomas and Sang Yong Han, D-SCIDS: Distributed SoftComputing intrusion detection system , Journal of Network and Computer Applications 30, PP 81 98, 2007 [5] Michael P. Brennan , Author Retains Full Rights AD Using Snort For a Distributed Intrusion Detection System , Version 1.3, SANS Institute , 29.01.2002
References DIDS [6] Andrew Baker, Andrew R. Baker, Brian Caswell, Jay Beale, Joel Esler, Snort IDS and IPS Toolkit , Syngress Media Inc Publishing, 2007 [7] Ronald L. Krutz, Securing SCADA Systems , Wiley Publishing, December 2005 [8] D. Gavrilis, E. Dermatas, Real-Time Detection of Distributed Denial of Service Attack Using RBF Network and Statistical Feature , International Journal of Computer Network, Vol 48, pp 235-245, 2005. [9] Paul Innella and Oba McMillan, An Introduction to Intrusion Detection Systems , Tetrad Digital Integrity,. LLC, 2001 [10] A Mouinji, B L Charlier, D Zampunieris, N Habra, Distributed Audit Trail Analysis , Proceedings of the ISOC 95 Symposium on Network and Distributed System Security , pp. 102- 112, 1995 [11] R A Kemmerer, NSTAT: a Model-based Real-time Network Intrusion Detection System , Technical Report TRCS97-18, Reliable Software Group, Department of Computer Science, University of California at Santa Barbara, 1997
References DIDS [12] S R Snapp, J Bretano, G V Diaz, T L Goan, L T Heberlain, C Ho , K N Levitt, B Mukherjee, S E Smaha, T Grance, D M Teal, D Mansur, DIDS (Distributed Intrusion Detection System) motivation architecture and an early prototype , Proceedings 14th National Computer Security Conference, Washington DC, October, pp. 167-176, 1999 [13] G Vigna, R A Kemmerer, NetSTAT: A network-based intrusion detection system , Journal Computer Security, Vol. 7, No, 1, pp. 37-71, 1999 [14] P A Porras, P G Neumann, EMERALD: event monitoring enabling response to anomalous live disturbances , Proceedings 20th National Information Security Conference, NIST 1997 [15] S Staniford-Chen, S Cheung, R Crawford, M Dilger, J Frank, J Hoagland, K Levitt, C Wee, R Yipi, D Z Erkle, GriDS a large scale intrusion detection system for large networks , Proceedings 19th National Information Security Conference, Vol. 1, pp. 361-370, 1996 [16] E H Spafford, D Zamboni, Intrusion detection using autonomous agents , Computer Networks, 34, pp. 547-570, 2000
References DIDS [17] ) S Staniford-Chen, S, B Tung, and D Schnackenberg, The Common Intrusion Detection Framework (CIDF) . Proc. Information Survivability Workshop, Orlando FL, October 1998 [18] R Feiertag, S Rho, L Benzingher, S Wu, T Redmond, C Zhang, K Levitt, D Peticolas, M Heckman, S Staniford, J McAlerney, Intrusion Detection Inter-Component Adaptive Negotiation . Computer Networks, Vol. 34, pp. 605-621, 2000 [19] W Lee, R A Nimbalker, K K Yee, S B Patil, P H Desai, P P Tran, S J Stolfo, A data mining and CIDF based approach for detecting novel and distributed intrusions , Proc. 3rd International Workshop on Recent Advances in Intrusion Detection, 2000 [20] P Ning, S Jajodia, X S Wang, Design and implementation of a decentralized prototype system for detecting distributed attacks , Computer Communications, Vol. 25, pp. 1374-1391, 2002 [21] Ajith Abraham, Johnson Thomas, Distributed Intrusion Detection Systems: A Computational Intelligence Approach , ABBASS H.A. AND ESSAM D. (EDS.), IDEA GROUP INC. PUBLISHERS, USA , Vol. 5, pp. 105-135, 2005 2009 2009 Snort 22 23 [ [ ] ]