Understanding How the Internet Works
Delve into the intricacies of the Internet, exploring its fundamental architecture, the concept of packet switching, latency and ping measurements, and how data travels through this vast network. Discover the essential components that make up this interconnected web of networks and gain insights into the technology that powers our digital world.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
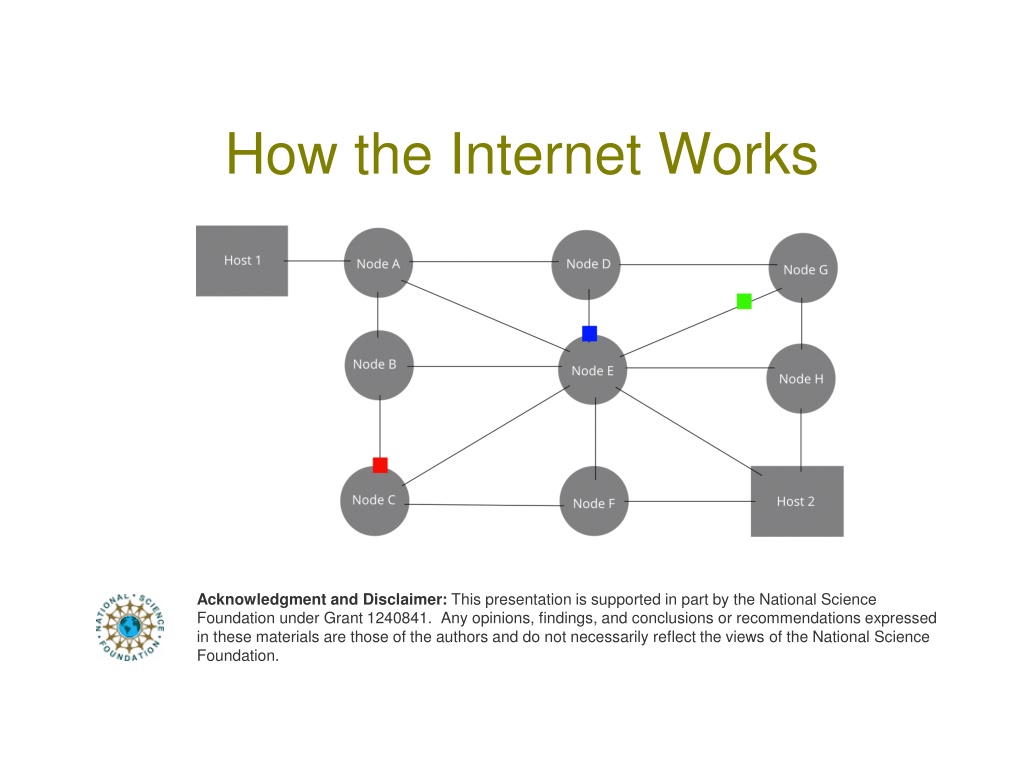
How the Internet Works Acknowledgment and Disclaimer: This presentation is supported in part by the National Science Foundation under Grant 1240841. Any opinions, findings, and conclusions or recommendations expressed in these materials are those of the authors and do not necessarily reflect the views of the National Science Foundation.
How is the Internet connected together?
Basic Architecture The Internet is a network of networks R R R R
Basic Architecture The Internet is a network of networks in which host computers Hosts R R R R
Basic Architecture The Internet is a network of networks in which host computers are connected by routers. Hosts Routers R R R R
Latency and Ping Latency is a measure of the time it takes a piece of data to reach its destination typically measured in milliseconds (ms) Wireless connections have higher latency than wired Ping is a networking utility to measure the latency on the Internet Ping takes a hostname or IP address as a parameter and sends a small test packet to the node that is echoed by it Once the echo is received time is measured Examples from linux ping www.arizona.edu ping www.google.com ping www.govt.nz
How does data travel through the Internet?
Packet Switching Messages are broken into fixed-sized packets -- e.g., P1, P2, P3. 1. Break the Message into Packets Message P1P2P3 Packets P1 P2 P3
Packet Switching Messages are broken into fixed-sized packets -- e.g., P1, P2, P3. Packets are routed independently ( , , ) 1. Break the Message into Packets Message P1P2P3 Packets P1 P2 P3 2. Send the packets to destination
Packet Switching Messages are broken into fixed-sized packets -- e.g., P1, P2, P3. Packets are routed independently ( , , ) The original message is re-assembled at the destination. 1. Break the Message into Packets Message P1P2P3 Packets P1 P2 P3 Packets P1 P2 P3 Message P1P2P3 2. Send the packets to destination 3. Reassemble the packets.
Packet Switching: Basic Ideas Motivated in the 1960s by the desire for a network that could withstand a nuclear attack: o A decentralized network with multiple paths between points A and B o Dividing the message into small packets that are routed independently o Each router along the path forwards packets to another router along the path
Decentralization and Redundancy Decentralized networks with redundant paths provide robustness in network design
Decentralization and Redundancy Decentralized networks with redundant paths provide robustness in network design Centralized Network B A
Decentralization and Redundancy Decentralized networks with redundant paths provide robustness in network design Centralized Network B A Vulnerability: Single route from A to B. The network is destroyed by knocking out the center.
Decentralization and Redundancy Decentralized networks with redundant paths provide robustness in network design Centralized Network Decentralized Network A B A B Vulnerability: Single route from A to B. The network is destroyed by knocking out the center.
Decentralization and Redundancy Decentralized networks with redundant paths provide robustness in network design Centralized Network Decentralized Network A B A B Robustness: Redundant routes from A to B. Network survives attacks to individual nodes. Vulnerability: Single route from A to B. The network is destroyed by knocking out the center.
Packet vs Circuit Switching In a circuit-switched network (telephones) there is a dedicated channel between A and B In a packet-switched network there is no sustained connection between A and B Browsing: Navigating from one page to another may seem like it s a dedicated channel, but it s not Packet switching increases redundancy and robustness
Traceroute Traceroute is a networking utility used to trace the route and measure delays of packets moving through the Internet Traceroute repeatedly sends packets from the source to destination with increasing time to live (TTL or number of hops) starting at 1, 2, 3, 1 2 1 Source Destination It uses data received to build a list of hops
traceroute wikipedia.org Destination host Die after this many hops Hop number Domain names and IP addresses of routers and hosts along the way Round trip times (RTT) or latency for 3 packets to the hop and back.
Global Bandwidth Bandwidth speeds vary across the globe The current global average is 18.4 Mbps download Korea leads the world with 52.6 Mbps In the US the average is 24.4 Mbps
Broadband Access Broadband: high speed Internet service that is always on, typically through cable or DSL modems (Src: OECD) 72.4% Penetration in OECD Countries 6 Countries have over 100% penetration 7 for 3 people in my house
Bandwidth Bandwidth or throughput is the rate at which data are downloaded or uploaded in a network. o Measured in Kilobits per second (Kbps) -- thousands, or o Megabits per second (Mbps) -- millions Untitled.tiff Click me