Rescue Drone: Increasing Autonomy and Implementing Computer Vision
Focuses on developing a rescue drone with increased autonomy and implementing computer vision for advanced object detection. The team, consisting of Cody Campbell (Hardware Engineer), Alexandra Borgesen (Computer Engineer), Halil Yonter (Team Leader), Shawn Cho (Software Engineer), Peter Burchell (M
78 views • 44 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Exploring the Impact of Social Media on Communication
Delve into the influence of social media on communication styles, analyzing popular terms like "selfie, YOLO, like, bae, hashtag." Understand the evolution of language through social media platforms, discussing its pros and cons on interpersonal interactions. Explore the challenges in deciphering so
1 views • 6 slides
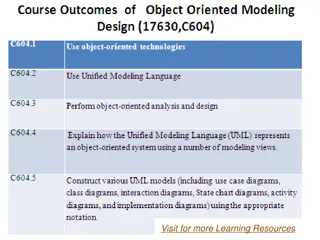
Understanding Data Modeling vs Object Modeling
Data modeling involves exploring data-oriented structures, identifying entity types, and assigning attributes similar to class modeling in object-oriented development. Object models should not be solely based on existing data schemas due to impedance mismatches between object and relational paradigm
0 views • 17 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
NC22Plex STR Detection Kit: Advanced 5-Color Fluorescence Detection System
Explore the cutting-edge NC22Plex STR Detection Kit from Jiangsu Superbio Biomedical, offering a 5-color fluorescence detection system suitable for multiple applications. Enhance your research capabilities with this innovative product designed for precision and efficiency.
0 views • 20 slides
Understanding Object Behaviors and Statechart Diagrams in Software Design
Object behaviors and UML statechart diagrams play a crucial role in software requirements and design. State machines, transitions, events, and states are essential concepts in modeling object behavior in response to external events. By utilizing UML statechart diagrams, one can effectively represent
0 views • 23 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
Understanding Object Modeling in Software Development
Object modeling is a crucial concept in software development, capturing the static structure of a system by depicting objects, their relationships, attributes, and operations. This modeling method aids in demonstrating systems to stakeholders and promotes a deeper understanding of real-world entitie
1 views • 65 slides
Understanding Object-Oriented Design Principles
Explore the core concepts of object-oriented design, including objects, classes, and the object-oriented paradigm. Learn about the relationship between objects and classes, and how they form the building blocks of software development. Gain insights into class components, attributes, and methods, an
0 views • 18 slides
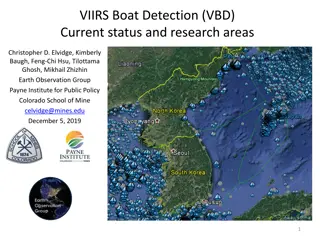
VIIRS Boat Detection (VBD) Research Overview
The Visible Infrared Imaging Radiometer Suite (VIIRS) program, a joint effort between NASA and NOAA, focuses on weather prediction and boat detection using low light imaging data collected at night. The VIIRS system provides global coverage with sensitive instruments and efficient data flow processe
1 views • 13 slides
Promoting Emotional Safety and Well-being at Happy Campers
Happy Campers, led by Marcel Horowitz, MS, MCHES, focuses on creating a positive camp experience for children in Yolo County. The camp emphasizes the value of finding partners, the importance of emotional safety, and the impact of feeling good on campers' experiences. Addressing factors like sleep,
0 views • 10 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Stop Hidden Water Damage: Your Ultimate Guide to Leak Detection in San Diego
Learn how San Diego leak detection services can help protect your home from water damage. Discover the signs of leaks, advanced detection technologies, and tips to prevent costly repairs. Stay ahead with proactive slab leak detection and expert solut
0 views • 6 slides
Configuration Examples for IP SLA with Object Tracking
Learn how to configure and troubleshoot IP SLA with Object Tracking using detailed examples for Static Routing, HSRP, and Policy Based Routing. Find out where Object Tracking can be implemented and when not to use it in various network scenarios. Understand the configuration components, including de
2 views • 17 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
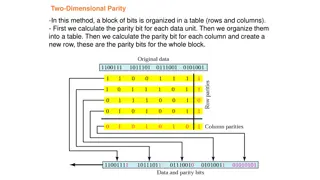
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
Understanding Subject and Object Pronouns
Learn about subject and object pronouns, their usage in sentences, and examples to differentiate between them. Subject pronouns are used as the subject of a sentence, while object pronouns function as the object of a verb or preposition. Understand when to use pronouns like "I" or "me," "they" or "t
0 views • 13 slides
Understanding Direct Objects and Direct Object Pronouns in English and French
Explore the concepts of direct objects and direct object pronouns in English and French languages. Learn how direct objects are used in sentences, the role of direct object pronouns in avoiding repetition, and the differences in sentence structure when using object pronouns in French. Discover commo
0 views • 24 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Overview of Yolo Commons Town Hall Statistics
In the Yolo Commons Town Hall meeting on July 12th, 2022, various charts and data were presented regarding cases referred to the prosecutor, cases prosecuted, rejected cases, diverted cases, and cases sentenced to state prison. Visual representations of these statistics were shared, shedding light o
0 views • 8 slides
Understanding the Difference Between Aggregation and Composition in Object-Oriented Programming
Aggregation and Composition are two important concepts in object-oriented programming. Aggregation refers to a 'has-a' relationship where the contained object can survive independently, while Composition indicates that the member object is part of the containing class and cannot exist separately. Th
0 views • 15 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Innovative Autonomous Ground Robot for Orchard Management
This project showcases an Autonomous Ground Robot designed for orchard management tasks. The robot's hardware, software design, problem identification, and objectives are outlined. Key features include YOLO-based apple counting, SLAM navigation, and soil moisture detection. The system runs on Ubuntu
0 views • 19 slides
Metrics and Lessons Learned for Object-Oriented Projects
This chapter discusses various metrics and lessons learned for object-oriented projects, including the use of major OO metrics, Lorenz's metrics, IBM's Object Oriented Technology Council recommendations, and the CK metrics suite. The CK metrics suite covers six OO design and complexity measures, suc
0 views • 17 slides
Fundamentals of Object-Oriented Programming in Java
Object-Oriented Programming (OOP) is a methodology that simplifies software development by using classes and objects. This paradigm includes concepts like Object, Class, Inheritance, Polymorphism, Abstraction, and Encapsulation. Other terms used in OOP design include Coupling, Cohesion, Association,
0 views • 54 slides
Object-Oriented Python Code for WIMP Direct Detection Signals
Calculating signals for Weakly Interacting Massive Particle (WIMP) direct detection using an object-oriented Python code called WimPyDD. WimPyDD provides accurate predictions for expected rates in WIMP direct detection experiments within the framework of Galilean invariant non-relativistic effective
0 views • 24 slides
Understanding Edge Detection in Image Processing
Edge detection is a fundamental operation in image processing, crucial for identifying object boundaries based on rapid changes in brightness. This process involves detecting areas of discontinuity in gray-level values to locate edges, which hold significant information about objects in an image. Co
0 views • 12 slides
Shy Robot Programming Challenge: Logic-Based Autonomous Robot
The Shy Robot is an autonomous robot equipped with two IR sensors to avoid obstacles. Its behavior is determined by a logical control system - moving backward if both sensors detect an object, turning right if only the left sensor detects an object, turning left if only the right sensor detects an o
0 views • 5 slides
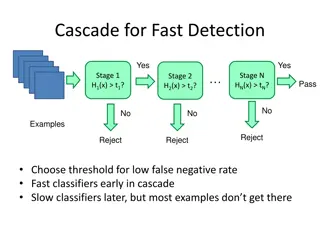
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Understanding Momentum in Physics
Momentum, first introduced by Isaac Newton, is symbolized by the letter p and signifies inertia in motion. It is calculated as mass multiplied by velocity (p = m * v) and has the unit of kg * m/s. The amount of momentum depends on the object's mass and speed. A moving object has more momentum if eit
0 views • 18 slides
Understanding Object Properties and Hierarchy in Excel VBA
Exploring how to activate, manipulate, and work with different Excel object collections such as Workbooks, Worksheets, and Charts in VBA. Learn to navigate object hierarchies, access specific objects, and manage object properties to enhance your Excel macro development skills.
0 views • 16 slides
Development of Deep Learning-Based Logistics Sorting System
Investigating automated parcel sorting with a robotic arm in a simulated environment using object detection and pose estimation based on deep learning. The project aims to enhance sorting efficiency in response to the increasing volume of parcels in the logistics industry with the application of vis
0 views • 10 slides