City Revenue and Economic Forecast Update for Fiscal 2023
Council Finance projects a mild recession and weak recovery, with tax revenues exceeding OMB's forecast but constrained by inflationary pressures. Despite economic challenges, FY23 tax collections are higher, driven by strong consumer spending and real estate activity.
8 views • 5 slides
Extension Teaching Methods
Extension teaching methods play a crucial role in facilitating communication and knowledge transfer between rural communities and extension workers. These methods aim to engage, stimulate, and guide learners through the process of acquiring new skills and knowledge. Centurion University in India emp
4 views • 8 slides
Understanding Strong and Weak Forms in English Pronunciation
Exploring the concept of strong and weak forms in English pronunciation, this content discusses the importance of using weak forms in speech, the rules of occurrence of strong forms, and how to recognize the position of weak forms. Examples and explanations illustrate how function words are weakened
1 views • 25 slides
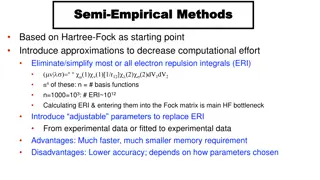
Overview of Semi-Empirical Methods Based on Hartree-Fock
Semi-empirical methods derived from Hartree-Fock theory aim to reduce computational effort by approximating or eliminating electron repulsion integrals. Strategies include introducing adjustable parameters to replace ERI calculations and utilizing zero differential overlap methods like CNDO, INDO, N
1 views • 11 slides
3D Human Pose Estimation Using HG-RCNN and Weak-Perspective Projection
This project focuses on multi-person 3D human pose estimation from monocular images using advanced techniques like HG-RCNN for 2D heatmaps estimation and a shallow 3D pose module for lifting keypoints to 3D space. The approach leverages weak-perspective projection assumptions for global pose approxi
0 views • 8 slides
Understanding Central and Non-Central Forces in Physics
Newton's laws of motion introduced the concept of forces, leading to the classification of fundamental forces like gravitational, electromagnetic, strong nuclear, and weak nuclear forces. Central forces act toward or away from a fixed center, while non-central forces are affected by additional param
0 views • 7 slides
Understanding Contraception: Methods, Importance, and Considerations
Contraception refers to methods used to prevent unwanted pregnancies, regulate pregnancy timing, and spacing between pregnancies. It is essential for women's reproductive health and can include barrier methods, hormonal methods, emergency contraception, and intrauterine devices. These methods are sa
1 views • 28 slides
Artificial Intelligence Heuristic Search Techniques
Assistant Professor Manimozhi from the Department of Computer Applications at Bon Secours College for Women in Thanjavur is exploring Artificial Intelligence concepts such as weak methods and Generate-and-Test algorithms. The content covers heuristic search techniques like generating and testing, hi
0 views • 7 slides
Introduction to Numerical Methods: A Comprehensive Overview
Numerical methods play a crucial role in solving mathematical problems efficiently through arithmetic operations. This lecture by Dr. Nur Uddin covers the fundamental concepts of numerical methods, emphasizing their importance in engineering problem-solving with the use of modern digital computers.
1 views • 17 slides
Understanding Methods of Social Work
Methods of social work encompass various approaches aimed at enhancing social functioning and addressing problems in individuals and communities. These methods are categorized into primary and secondary methods, each serving different purposes in the field. Primary methods involve direct interaction
0 views • 20 slides
Understanding Weak Signal Propagation in Radio Waves
This informative content delves into weak signal propagation and its various aspects related to electromagnetic waves, particularly in the context of radio communication. It covers topics such as radio waves, radio horizon, knife-edge diffraction, tropospheric scatter mode, auroral reflection, and m
0 views • 37 slides
Adapting Contest Strategies for Declining Solar Cycle 24 and Solar Cycle 25 Precursors
As Solar Cycle 24 rapidly declines, preparations for the subsequent Solar Cycle 25 are crucial. Insights on weak solar activity, potentially weak Cycle 25, and the impact on contest strategies are discussed. Improved DX propagation, reliable openings, and signal strengths to Europe and Japan, amidst
0 views • 12 slides
The Vital Role of Encryption in Safeguarding the Digital Economy
Encryption plays a crucial role in protecting the digital economy by providing secure communication channels. Professor Peter Swire from Ohio State University emphasizes the need for strong encryption over weak cybersecurity measures. He discusses the history of wiretaps, the shift to strong cryptog
0 views • 15 slides
Understanding Moving Averages and Exponential Smoothing Methods
Forecasting methods like moving averages and exponential smoothing are essential for analyzing time series data. Averaging methods involve equally weighted observations, while exponential smoothing methods assign unequal weights that decay exponentially. Both methods can be useful for forecasting in
0 views • 18 slides
Interactions of Planar Organic Radicals: Stacking and Bonding
Examination of the stacking interactions and bonding in planar organic radicals reveals a variety of non-covalent and weak covalent interactions such as hydrogen bonding, halogen bonding, and pancake bonding. This study highlights the significance of multicentric two-electron bonding and explores th
0 views • 29 slides
Understanding the Connection Between Lithium and Suicide Rates
Examining the correlation between lithium levels and suicide rates reveals mixed findings, with some studies suggesting a potential association while others show weak statistical significance. Factors such as gender, statistical methods, and concentration thresholds further complicate the relationsh
0 views • 23 slides
Types of Birth Control Methods and Their Effectiveness
Explore the different types of birth control available, including abstinence, hormonal methods, barrier methods, and permanent methods. Learn about the effectiveness rates, how they work, and their pros and cons to make an informed decision about contraception. From hormonal options like pills, patc
0 views • 23 slides
Understanding Acids and Bases in Chemistry
Acids donate protons, while bases accept them. Strong acids ionize completely while weak acids only partially ionize, resulting in a Ka value less than one. Water, being amphoteric, can both donate and accept protons. The ionization of water leads to a constant Kw value of 10^-14. Explore the ioniza
0 views • 15 slides
An Lp Theory for Outer Measures: Application to Singular Integrals II
This discussion covers various topics such as tents (or Carleson boxes), outer measures on the open upper half-plane, sizes of functions on tents, outer essential supremum on subsets, outer Lp spaces, embedding theorems, and estimates related to Linfity-Sinfty and weak L1-Sinfty. The content delves
0 views • 34 slides
Solving Systems of Equations: New Methods and Applications
The content discusses various methods for solving systems of equations, including substitution and elimination methods. It presents real-world problems involving money, sales figures, and fishing competitions to demonstrate the application of these methods. Readers will learn how to apply these tech
0 views • 10 slides
Procedural Decomposition and Static Methods in Programming
Understanding procedural decomposition and static methods is essential in programming to reduce redundancy, organize code effectively, and manage complexity. Procedural decomposition involves dividing a problem into methods, while static methods help in code reuse and managing complexity. By designi
0 views • 18 slides
Weak Interactions and Hydrogen Bonding in Molecular Forces
Exploring van der Waals forces, hydrogen bonding, and weak interactions in intermolecular forces and surface interactions. Understanding interactions between backbone peptide groups and orientation dependence of hydrogen bonding through dispersion forces and repulsive potentials.
0 views • 22 slides
Assay of Hydrogen Peroxide (H2O2) - Experimental Study
Hydrogen peroxide (H2O2) is a weak acid with both oxidant and reductant properties. It is an unstable compound that decomposes into oxygen and water. This experiment involves titrating hydrogen peroxide against a standard oxidizing agent solution to determine its concentration. The physical and chem
0 views • 9 slides
Graph Partitioning and Decomposition Techniques
Explore various graph partition problems and decomposition methods such as regularity partitions, representative sets, and 2-neighborhood representations. Learn about techniques to aggregate, scale down, sample, and divide graphs for efficient analysis and computation. Discover how nodes can be repr
0 views • 45 slides
Instrument Development in Mixed Methods Framework by Vanessa Scherman
Mixed methods research presented by Vanessa Scherman from the University of South Africa explores the development of instruments within a mixed methods framework. The content covers an overview of mixed methods, methodological norms, instrumental development, and closing the loop. It discusses the i
0 views • 40 slides
Understanding Strong and Weak Ties in Social Networks
Explore the concepts of strong and weak ties in social networks based on Easley and Kleinberg's theories. Delve into the flow of information, structural differences among nodes, and the evolution of networks over time. Discover the significance of triadic closure principle and clustering coefficient
0 views • 60 slides
Understanding Buffers in Chemistry
Buffers play a crucial role in maintaining stable pH levels in solutions. They are composed of a weak acid and its conjugate base or a weak base and its conjugate acid. This summary covers the definition of buffers, differentiation between buffer and non-buffer systems, the behavior of buffers when
3 views • 23 slides
Dynamo and Bayou: High Availability and Weak Consistency in Modern Applications
Dynamo and Bayou databases offer high availability and weak consistency, making them suitable for modern applications with super high demands. Examples of suitable applications include flight ticket booking, Amazon shopping carts, and more. Availability is crucial for accommodating millions of custo
0 views • 38 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Understanding Weak Superconductivity and Functional Coordinates
Delve into the realm of weak superconductivity and the significance of functional coordinates in this informative presentation. Explore the intricacies of these concepts through a series of visually appealing slides that shed light on their characteristics and applications. Gain insights into the re
0 views • 8 slides
Understanding the Titration of Weak Acids and Amino Acids
Titration is a crucial technique used to determine the properties of weak acids and amino acids. This process involves calculating pH values, degree of ionization, and understanding the ionization equilibrium of different acid-base systems. Various examples, including glycine hydrochloride, isoelect
0 views • 15 slides
Understanding Acids and Bases: Ionization and Properties
Acids donate protons while bases accept them. Strong acids and bases ionize completely, while weak acids ionize partially. Water is amphoteric, capable of both accepting and donating protons. The equilibrium constant Kw for water is 10^-14. Understanding the ionization of weak acids and weak bases h
0 views • 15 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Weak Visibility Queries of Line Segments in Simple Polygons - Overview
This information discusses weak visibility queries of line segments in simple polygons, focusing on topics such as visibility of line segments, visibility polygons, visibility graphs, and related previous work on preprocessing and data structures for visibility queries in simple polygons.
0 views • 26 slides
Understanding Weak Points in Web Application Architecture
Information collected during the reconnaissance process can unveil critical aspects of a web application's architecture, including technologies used, API endpoints, functionality, domains, configurations, and authentication systems. Vulnerabilities in web applications often stem from poorly designed
4 views • 13 slides
Equilibrium and Acid-Base Problems in Chemistry Lecture
In this lecture, topics such as Advanced Equilibrium, Acid/Base Equilibria, Systematic Method for solving chemical problems, Strong Acid/Strong Base scenarios, and General Comments on reactions are discussed. Examples using the systematic method are provided for practical understanding. Key points o
0 views • 13 slides
Mastering Weak 2 Opening Hands in Bridge Strategy
Learn the history and strategies behind weak 2 opening bids in Bridge, including the goals, rules, and considerations like suit quality, point range, and vulnerability. Expert recommendations emphasize the importance of partnership agreements for successful preempts.
0 views • 23 slides
Understanding Acids and Bases in Chemistry: Key Concepts and Terminology
This chapter delves into the fundamental concepts of acids and bases in chemistry, covering Arrhenius, Bronsted-Lowry, and Lewis definitions. It discusses conjugate acids and bases, acid dissociation, dissociation of strong and weak acids, and the differences between strong and weak acids/bases. The
0 views • 41 slides
Weak Supervision for NLP: Overcoming Labelled Data Challenges
Addressing the challenge of acquiring labelled data for NLP models, weak supervision techniques offer solutions through alternative annotation methods and leveraging diverse data sources. This talk highlights the importance of overcoming the scarcity of labelled data in machine learning and NLP task
0 views • 18 slides
Memory Models: Enhancing Semantics for Programs with Data Races
This content delves into the importance of establishing stronger memory models to provide better semantics for programs experiencing data races. It highlights the challenges faced due to weak semantics in programming languages like C++ and Java, emphasizing the need for improved memory models to add
0 views • 61 slides