MONITORING OF TREASURY OPERATIONS
The state financial control system in Uzbekistan is governed by the Budget Code and involves various bodies such as the Accounts Chamber, Ministry of Economy and Finance, and Treasury Service Committee. It includes methods like full control and selective control, types such as preliminary and ongoin
5 views • 10 slides
Budget Execution Challenges in Somalia's Social Sectors
Addressing malnutrition in Somalia is hindered by low budget execution rates in the health and education sectors. Only a small portion of Official Development Assistance (ODA) is channeled through government systems, impacting service delivery and development financing. Donor-supported budgets for h
0 views • 32 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
Comprehensive Marketing Process Implementation Plan Presentation
This comprehensive marketing process implementation plan template is designed to guide project teams through the phases of project execution. It includes detailed tasks, timelines, milestones, and phases to ensure successful implementation. The plan covers key aspects from initial project setup to f
5 views • 7 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
0 views • 26 slides
Enhancing Health Data Usage for Transient Populations in Malawi
Exploring the challenges and successes in using health data for transient populations in Malawi, this presentation covers migration trends, potential opportunities, and recommendations for data use and exchange. Case studies illustrate the complexities of managing health data for mobile populations,
1 views • 15 slides
Understanding Transient Conduction in Heat Transfer
Transient conduction in heat transfer occurs when boundary temperatures change, causing temperature variations within a system until a steady state is achieved. This phenomenon is commonly seen in processes like quenching hot metals. The Lumped Capacitance Method is used to analyze such scenarios, i
0 views • 55 slides
Understanding the Neglected Provisions of Order XXI CPC, 1908
Explore the overlooked aspects of Order XXI CPC, 1908, focusing on the definitions, types of decrees, modes of execution, procedures for executing decrees, reasons for neglect, impact, recommendations, and conclusion. Learn about neglected provisions like summary execution, execution against legal r
0 views • 14 slides
Understanding Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
Transient Conduction in Thermal Energy Storage Units and Cylinders
Explore examples of transient conduction phenomena in thermal energy storage units, cylinders, and spheres. Learn how to calculate time durations, temperature changes, and energy removal rates during these heating and cooling processes. The examples cover scenarios involving aluminum slabs, oil bath
0 views • 10 slides
Power System Stability Lecture: Transient Solutions and Load Models
This lecture delves into transient stability solutions and load models in power systems. It covers the simultaneous implicit method for solving algebraic and differential equations, focusing on the Trapezoidal approach for linear systems. The discussion extends to nonlinear cases, particularly using
0 views • 47 slides
Understanding Transient Interference Suppression in Speech Enhancement
Transient interference, characterized by abrupt sounds followed by decaying oscillations, poses a challenge for standard speech enhancement algorithms. This article delves into the statistical modeling and problem formulation of transient suppression, exploring band-to-band filters, spectral varianc
5 views • 11 slides
Power System Transient Stability Overview: ECEN 667 Lecture Summary
This summary covers the key points discussed in the lecture on transient stability in power systems by Professor Tom Overbye at Texas A&M University. Topics include contingency analysis, results interpretation, PowerWorld Simulator usage, plotting results, and more. Detailed information is provided
0 views • 43 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Modes of Execution of Decree in Civil Law
The lecture discusses the various modes of execution of decree in civil law, such as execution against a person through arrest and detention, and execution against property. It explains the procedures involved in arrest and detention, including the conditions for release, restrictions on arrest, and
0 views • 9 slides
Power System Analysis Lecture: Transient Stability with Prof. Tom Overbye
In Lecture 23 of ECE 476, Prof. Tom Overbye discusses transient stability in power systems. Topics include power system time scales, frequency variations, dynamics behavior, grid disturbances, and power flow analysis. Announcements regarding assignments and exams are also highlighted.
1 views • 25 slides
Understanding Weird Machines in Transient Execution
Weird machines refer to models exhibiting unintentional behaviors triggered by adversarial inputs. They serve as computation primitives, enabling tasks like program obfuscation and secret computations. TSX weird machines, computing with time, manipulate cache states through gates like Assign, AND, O
0 views • 18 slides
Understanding Java Memory Management
Explore how memory is managed in Java programs, including memory allocation for code, objects, and execution stack. Learn about memory areas like the execution stack and heap, and understand the concept of activation records in method execution.
0 views • 27 slides
Exploring Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Evolution of Execution Methods in Modern Society
Explore the historical and modern methods of execution, from hanging to lethal injection, and the transition towards more civilized approaches. Learn about the contributions of prominent figures like Elbridge Gerry in advocating for humane execution methods. Delve into the commercial rivalry between
0 views • 13 slides
Secure and Efficient Multi-Variant Execution in Distributed Settings
This paper discusses dMVX, a system for secure multi-variant execution in distributed settings to mitigate memory errors and protect against attacks. Using leader and follower variants, diversified program variants run in lockstep to ensure security. The system monitors and replicates I/O results, e
0 views • 35 slides
Proposal for Transient Station Identification in IEEE 802.11-21
TGbh use cases necessitate a form of Identity for Non-AP STAs for access control. This proposal delves into the concept of a Transient ID, detached from a MAC address, to support use cases securely. It explores the generation and validation of Transient Identity (TSID) and its key (TSIDK) in conjunc
0 views • 13 slides
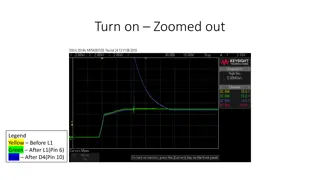
Understanding Transient Behavior in Electrical Systems
Explore the transient behavior in electrical systems through a series of zoomed-in and zoomed-out images depicting different stages during power transitions. Follow along as signals oscillate, square shapes are lost, and switches are cycled, offering insights into system behavior under various condi
0 views • 12 slides
Hardware-Assisted Task Scheduler for OS Intensive Applications
A hardware-assisted task scheduler called SchedTask is proposed to address the issue of instruction cache pollution in OS intensive applications. By utilizing SuperFunction characterization and a specialized scheduler, the system aims to optimize task execution on different cores for improved perfor
0 views • 28 slides
Understanding Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
State and Local Transient Room Tax Reporting System Considerations
The Kentucky Department of Revenue discussed the costs and benefits of integrating the local transient room tax reporting and distribution system. The study also looked into the experiences of border states like Virginia and Indiana with similar tax structures. While no fully integrated system was f
0 views • 9 slides
Multi-Messenger Searches for Transient Astrophysical Sources
This talk reviews three classes of transient astrophysical sources capable of producing gravitational wave (GW) signals in the LIGO and Virgo frequency range. These sources include coalescence of neutron star (NS) and black hole (BH) binary systems, core collapsing stars, and flaring/bursting NSs. T
0 views • 38 slides
Understanding Processes in Operating Systems - ECE344 Lecture 3 Summary
This lecture delves into the essential concepts of processes, threads, and synchronization in operating systems. Key topics covered include units of execution, representation of units of execution in the OS, process execution states, and state transitions. Users, programs, and the role of processes
0 views • 45 slides
InvisiSpec: Making Speculative Execution Invisible
InvisiSpec presents a novel defense mechanism to address speculative execution attacks in the cache hierarchy. By making speculative execution invisible to potential attackers, this holistic approach aims to mitigate the risks associated with exploiting side effects on incorrect paths, such as Spect
0 views • 18 slides
Multicycle Datapath and Execution Steps Overview
This content provides a detailed explanation of a multicycle datapath and the execution steps involved in processing instructions. It covers key elements such as instruction fetching, decoding, memory referencing, ALU operations, branch and jump instructions, as well as memory access for read and wr
0 views • 11 slides
Understanding Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Understanding Transient Simulations in MODFLOW
Explore the key aspects of transient simulations in MODFLOW such as storage coefficients, initial conditions, stress periods, and the Changing Head Boundary package. Learn about the importance of storage parameters, LPF package options, defining initial conditions, and utilizing model-generated head
0 views • 16 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Rethinking Processes with Threads in Operating Systems
Processes in operating systems traditionally include various resources and execution states, leading to inefficiencies in communication and parallel program execution. By separating the concept of a process from its execution state, modern OSes like Mac, Windows, and Unix introduce threads as lightw
0 views • 29 slides
Python Programming Essentials: Basics, Operators, Expressions, and Control Flow
This segment delves into the fundamentals of Python programming with a focus on essential concepts such as comments, numbers, strings, variables, arithmetic operators, logical operators, order of execution, expressions, and control flow statements like conditional execution and looping. Learn about
0 views • 12 slides
Cloud-Scale VM Deflation for Running Interactive Applications on Transient Servers
This research explores the concept of deflatable virtual machines to run interactive applications on transient cloud servers without facing unexpected preemption. By reclaiming resources from low-priority VMs and allowing forward progress with some performance degradation, the method aims to provide
0 views • 29 slides
Understanding Operating System Concepts: Multiprogramming, Multiprocessing, Multitasking, and Multithreading
In the realm of operating systems, terms like multiprogramming, multiprocessing, multitasking, and multithreading can often be confusing due to their similar appearance but distinct meanings. These concepts play a crucial role in efficiently managing resources in a computing system, particularly in
0 views • 6 slides
Lead Compensator Design for Improved Transient Response in Automatic Control Systems
Lead compensators are utilized in automatic control systems to enhance transient response. By designing a lead compensator, one can adjust stability and error parameters for optimal system performance. This involves determining the appropriate gain and phase margin to meet error constraints and achi
0 views • 12 slides
Memory Allocation and Program Execution Overview
Understanding memory allocation is crucial for efficient program execution. This content delves into the importance of memory allocation, considerations for storing data during program execution, and the requirements for allocating memory efficiently. It also explores solutions for managing memory s
0 views • 35 slides
Understanding CPU Virtualization and Execution Control in Operating Systems
Explore the concepts of CPU virtualization, direct execution, and control mechanisms in operating systems illustrated through a series of descriptive images. Learn about efficient CPU virtualization techniques, managing restricted operations, system calls, and a limited direct execution protocol for
0 views • 18 slides