Verification Environment for ALTIROC3 ASIC in ATLAS High Granularity Timing Detector
The verification environment for the ALTIROC3 ASIC in the ATLAS High Granularity Timing Detector is crucial for the upgrades in the ATLAS HL-LHC experiment, aiming to improve particle detection performance in the forward region, mitigate pile-up effects, and provide luminosity measurement. The ALTIR
7 views • 26 slides
APAC Position, Navigation, and Timing Solution Market Analysis & Forecast
The Asia-Pacific position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $1,410.5 million by 2033 from $466.1 million in 2023, at a CAGR of 11.71% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/asia-pacific-position
11 views • 3 slides
Position, Navigation, and Timing Solution Market Forecast to 2033
The global position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $5.24 billion in 2033 from $1.23 billion in 2022, at a CAGR of 10.85% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/position-navigation-timing-solu
0 views • 3 slides
Machine Learning for Predicting Path-Based Slack in Timing Analysis
Utilizing machine learning to forecast path-based slack in graph-based timing analysis offers a solution for optimizing power and area efficiency in the design process. The Static Timing Analysis incorporates accurate path-based analysis (PBA) and fast graph-based analysis (GBA) to estimate transiti
1 views • 31 slides
Importance of Timely Verification in Care After Death
Understanding the verification process and importance of timely verification in care after death is crucial for improving the experience of death and dying for families. This session covers the definitions, process, and care after death, emphasizing the significance of timely verification in end-of-
1 views • 15 slides
Electors Verification Programme Overview
The Electors Verification Programme (EVP) is a campaign initiative encouraging citizens to verify and authenticate electoral details, including family members. Various methods such as NVSP, Mobile App, and 1950 helpline are utilized for verification. Citizens can also submit details through BLOs to
1 views • 25 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
2 views • 15 slides
GLP.BBBEE.(PTY).LTD - Your Trusted BEE Verification Agency
GLP.BBBEE.(PTY).LTD is a level 3 SANAS accredited BEE verification agency with 9 years of experience specializing in complex ownership structures. They offer professional BEE verification services with a team of technical signatories ensuring fair ratings for clients across various sectors. Their ef
0 views • 7 slides
Integrated Verification and Repair in Control Plane
Modern networks face challenges from incorrect configurations affecting millions of users. This presentation discusses the integration of verification and repair processes into the control plane, aiming for consistent and policy-compliant network operations. It explores the complexities of network c
0 views • 16 slides
Formal Verification and Automata Abstraction in Esterel
This content delves into the applications of formal verification and automata abstraction in Esterel, focusing on techniques such as verification by abstraction of automata, boolean verification using BDDs, bounded model checking in SAT/SMT, and more. The work of Gérard Berry at the Collège de Fra
0 views • 38 slides
Designing a Traffic Signal Timing Plan: Steps and Guidelines
This comprehensive guide covers the essential steps involved in designing a traffic signal timing plan, including determining lane configurations, proposing phase plans, identifying critical volumes, recommending phase plans, and establishing clearance intervals. It also provides insights into aspec
1 views • 26 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Program Verification via an Intermediate Verification Language
Dive into the world of program verification through an intermediate verification language with a focus on static program verification, reasoning about programs, and separation of concerns. Explore tools like Dafny and verification architectures like Boogie and Why3, along with key concepts including
0 views • 36 slides
Numerical Abstract Domain with Max Operator in Timing Analysis
Explore a numerical abstract domain based on expression abstraction and the Max operator with applications in timing analysis. The challenges in timing analysis, such as disjunctive and non-linear bounds, are discussed along with simple examples illustrating these concepts. The difficulty of proving
0 views • 21 slides
Harvesting and Postharvest Techniques for Quality Seed Production
Understand the importance of harvesting crops at the right timing to maximize seed quality. Learn about half-matured and full-matured stages, postharvest ripening, and indicators for precise timing. Discover the significance of counting days from flowering/pollination for determining harvest timing.
0 views • 24 slides
Understanding Verification Methods in Spring 2022 Tufts University Lectures
Explore the lectures by Joel Grodstein and Scott Taylor at Tufts University focusing on verification methods, including self-checking tests, cycle-by-cycle comparison, and the importance of getting the correct data and timing. The lectures discuss the challenges of ensuring correctness in designs an
0 views • 54 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
1 views • 26 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
Formal Verification of Cyberphysical Systems and Future Certification Methods
Explore the formal verification techniques and tools used in cyberphysical systems, including KeYMaera verification tool, applications in distributed car control and adaptive cruise control, and the formal verification of ACC algorithms. The future work section highlights considerations for sensor d
0 views • 17 slides
Comprehensive Solution for EU Digital COVID Certificate Verification
This solution offers face recognition, temperature monitoring, and verification of EU Digital COVID Certificates for personnel. It includes products like DHI-ASI7213X-V1-T1 and ASF172X-T1, with various unlocking modes and support for certificate verification. The system allows for accurate and fast
0 views • 7 slides
Automated Static Verification of Higher-order Functional Programs
Explore the automated static verification of higher-order functional programs, focusing on Haskell code. Learn about denotational semantics, program assertions, and tools like GHC for verification. Discover the emphasis on simplicity and structural properties for easy proofs. Consider utilizing exis
0 views • 22 slides
Cesarean Delivery Timing Guidelines for Women with Prior Uterine Scars
Society for Maternal Fetal Medicine provides cesarean delivery timing recommendations for women with prior uterine scars. For those with a history of classical cesarean, the risk of uterine rupture guides the timing of repeat cesarean. Similarly, women with prior myomectomy should plan delivery betw
0 views • 10 slides
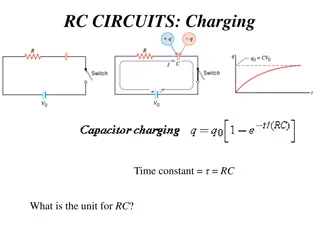
Applications of RC Circuits in Electronics and Biomedical Devices
RC circuits play a crucial role in various applications such as camera flashes, timing devices in automobiles, and heart pacemakers. These circuits involve charging and discharging a capacitor through a resistor, controlling voltage pulses for precise timing. In devices like camera flashes, the flas
0 views • 7 slides
Gradual Program Verification and its Techniques
Gradual Program Verification introduces a method where static verification is combined with dynamic verification to ensure program correctness gradually. This approach allows for partial specifications and runtime checks to be gradually applied, reducing the risk of errors and overhead in software d
0 views • 18 slides
NTN RRM Timing Related Requirements for Xiaomi Devices at 3GPP TSG-RAN4 Meeting #98-e
The agenda item for the 3GPP TSG-RAN4 Meeting #98-e involves discussing NTN RRM timing related requirements, specifically focusing on UE timing synchronization for Xiaomi devices. Key aspects include UE transmit timing error limits, timing advance accuracy, and UE timer accuracy requirements for NTN
0 views • 6 slides
WylasTiming - Wireless Semi-Automatic Timing System Overview
WylasTiming is a wireless semi-automatic timing system developed in Australia, utilizing off-the-shelf hardware and Android handsets. It provides accurate timing with automatic race starting and instantaneous data transmission. The timekeeper simply stops the clock at the end of the race, and data i
1 views • 15 slides
Simplifying Post-Silicon Timing Diagnosis with NGSPA Tool
Explore how the NGSPA tool by Intel simplifies post-silicon timing diagnosis, replacing costly machines with a CAD application running on an x86 server, saving resources and enabling parallelized CAD operations. Learn about the challenges in post-silicon speed debugging, the importance of static tim
0 views • 26 slides
Understanding Timing Models in Cell Design Environments
Delve into the intricacies of timing models for cells in design environments, exploring factors affecting delay, output transitions, linear and non-linear models, and the use of table models in cell libraries to specify delays and timing checks. Discover how input transitions and output capacitance
0 views • 11 slides
Warning Verification and Scoring Guidelines in Weather Forecasting Workshop
Learn about the verification of warnings, classical contingency scoring, false alarm ratio, hits, false alarms, missed alarms balance, threshold-based warning verification, and impact-based warning verification discussed in the IMS Warning workshop at KNMI Block III. Understand the importance of mai
0 views • 13 slides
Verification Modulo Versions: Towards Usable Verification
Explore the challenges and solutions in compile-time verification with CodeContracts in Visual Studio. Delve into addressing warnings, improving analysis precision, and managing syntactic baselines for a more reliable verification process.
0 views • 33 slides
SKA1 Low Assembly Integration & Verification Plan
The SKA1 Low Assembly, Integration, and Verification (AIV) Plan outlines the responsibilities of the AIV Consortium, consortium partners, and the roll-out plan for the SKA1 Low telescope. The plan encompasses user requirements validation, system verification, operational concepts, and more. It detai
0 views • 12 slides
Understanding Timing Vulnerabilities in Computing Systems
Explore the evolution of timing attacks in computing systems, from traditional crypt-analysis to modern web-focused techniques. Discover the gap in implementing security measures and how universities can bridge this disparity. Delve into the history, challenges, and implications of timing vulnerabil
0 views • 26 slides
ICAO Strategic Objective: Economic Development of Air Transport Verification and Validation Overview
This content provides an in-depth analysis of the ICAO Strategic Objective focusing on the economic development of air transport through verification and validation processes for air carriers. It includes details on forms verification, economic analysis, and policy considerations discussed at the IC
0 views • 22 slides
Overview of Program Verification Tools and Techniques
Explore the pillars of program verification, early mechanical verification systems, software quality assurance, and a spectrum of verification tools used for ensuring functional correctness, safety-critical systems, and more. Discover the role of proof assistants and automatic decision procedures in
0 views • 21 slides
Discussion on Timing Mask Requirement for ULSUP-TDM in RAN4#94e Meeting
In the RAN4#94e and #94e-Bis meetings, discussions were held on the timing mask requirement for ULSUP-TDM, particularly focusing on sub-topics like evaluating uplink timing differences between LTE and NR, clarifying present time mask conditions, and testing time mask requirements. The key issue cent
0 views • 4 slides
Understanding Static Timing Analysis in Advanced VLSI Design
Static timing analysis is a crucial aspect of VLSI design, helping predict chip performance before fabrication. This article explores the importance of static timing analysis, its effectiveness, and the limitations of dynamic simulation tools like SPICE. Learn about the challenges in testing critica
0 views • 76 slides
Introduction to UVM: Verification Methodologies Overview
Explore the Universal Verification Methodology (UVM) for writing modular, scalable, and reusable testbenches. Learn about UVM's key technical highlights, its support for migration towards Coverage Driven Verification (CDV), and the advantages of Constrained Random Verification (CRV) in functional ha
0 views • 20 slides
Advancing AMS Assertions for Analog/Digital Interface Verification
AMS assertions play a crucial role in verifying analog/digital interfaces, checking properties related to voltages, currents, and complex timing constraints. They bring advantages similar to SVAs in digital verification, addressing specific AMS requirements. Examples showcase comparisons of voltage/
0 views • 11 slides
Understanding Variable Valve Timing (VVT) in Internal Combustion Engines
Variable Valve Timing (VVT) optimizes engine performance by adjusting valve duration, timing, and lift according to engine speed, enhancing torque, power, and fuel efficiency. VVT operates by varying intake valve opening/closing, regulating valve timing, and adjusting lift for better volumetric effi
0 views • 14 slides
DeepFace: Advancements in Face Verification Technology
DeepFace by Yaniv Taigman, Ming Yang, Marc Aurelio Ranzato, and Lior Wolf from Facebook AI Group and Tel Aviv University presents a breakthrough in face verification technology. The system achieves human-level performance by utilizing deep neural networks for face recognition, detection, alignment,
0 views • 12 slides