Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
APAC Position, Navigation, and Timing Solution Market Analysis & Forecast
The Asia-Pacific position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $1,410.5 million by 2033 from $466.1 million in 2023, at a CAGR of 11.71% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/asia-pacific-position
11 views • 3 slides
Position, Navigation, and Timing Solution Market Forecast to 2033
The global position, navigation, and timing (PNT) solution (satellite) market is estimated to reach $5.24 billion in 2033 from $1.23 billion in 2022, at a CAGR of 10.85% during the forecast period 2023-2033.\nRead Report Overview: \/\/bisresearch.com\/industry-report\/position-navigation-timing-solu
0 views • 3 slides
Machine Learning for Predicting Path-Based Slack in Timing Analysis
Utilizing machine learning to forecast path-based slack in graph-based timing analysis offers a solution for optimizing power and area efficiency in the design process. The Static Timing Analysis incorporates accurate path-based analysis (PBA) and fast graph-based analysis (GBA) to estimate transiti
1 views • 31 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Designing a Traffic Signal Timing Plan: Steps and Guidelines
This comprehensive guide covers the essential steps involved in designing a traffic signal timing plan, including determining lane configurations, proposing phase plans, identifying critical volumes, recommending phase plans, and establishing clearance intervals. It also provides insights into aspec
1 views • 26 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Numerical Abstract Domain with Max Operator in Timing Analysis
Explore a numerical abstract domain based on expression abstraction and the Max operator with applications in timing analysis. The challenges in timing analysis, such as disjunctive and non-linear bounds, are discussed along with simple examples illustrating these concepts. The difficulty of proving
0 views • 21 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Harvesting and Postharvest Techniques for Quality Seed Production
Understand the importance of harvesting crops at the right timing to maximize seed quality. Learn about half-matured and full-matured stages, postharvest ripening, and indicators for precise timing. Discover the significance of counting days from flowering/pollination for determining harvest timing.
0 views • 24 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
Cesarean Delivery Timing Guidelines for Women with Prior Uterine Scars
Society for Maternal Fetal Medicine provides cesarean delivery timing recommendations for women with prior uterine scars. For those with a history of classical cesarean, the risk of uterine rupture guides the timing of repeat cesarean. Similarly, women with prior myomectomy should plan delivery betw
0 views • 10 slides
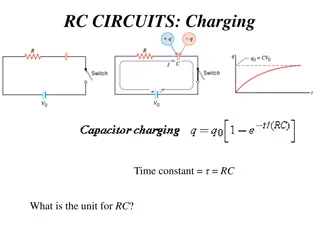
Applications of RC Circuits in Electronics and Biomedical Devices
RC circuits play a crucial role in various applications such as camera flashes, timing devices in automobiles, and heart pacemakers. These circuits involve charging and discharging a capacitor through a resistor, controlling voltage pulses for precise timing. In devices like camera flashes, the flas
0 views • 7 slides
NTN RRM Timing Related Requirements for Xiaomi Devices at 3GPP TSG-RAN4 Meeting #98-e
The agenda item for the 3GPP TSG-RAN4 Meeting #98-e involves discussing NTN RRM timing related requirements, specifically focusing on UE timing synchronization for Xiaomi devices. Key aspects include UE transmit timing error limits, timing advance accuracy, and UE timer accuracy requirements for NTN
0 views • 6 slides
WylasTiming - Wireless Semi-Automatic Timing System Overview
WylasTiming is a wireless semi-automatic timing system developed in Australia, utilizing off-the-shelf hardware and Android handsets. It provides accurate timing with automatic race starting and instantaneous data transmission. The timekeeper simply stops the clock at the end of the race, and data i
0 views • 15 slides
Simplifying Post-Silicon Timing Diagnosis with NGSPA Tool
Explore how the NGSPA tool by Intel simplifies post-silicon timing diagnosis, replacing costly machines with a CAD application running on an x86 server, saving resources and enabling parallelized CAD operations. Learn about the challenges in post-silicon speed debugging, the importance of static tim
0 views • 26 slides
Defending Against Cache-Based Side-Channel Attacks
The content discusses strategies to mitigate cache-based side-channel attacks, focusing on the importance of constant-time programming to avoid timing vulnerabilities. It covers topics such as microarchitectural attacks, cache structure, Prime+Probe attack, and the Bernstein attack on AES. Through d
0 views • 25 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Understanding Timing Models in Cell Design Environments
Delve into the intricacies of timing models for cells in design environments, exploring factors affecting delay, output transitions, linear and non-linear models, and the use of table models in cell libraries to specify delays and timing checks. Discover how input transitions and output capacitance
0 views • 11 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Timing Vulnerabilities in Computing Systems
Explore the evolution of timing attacks in computing systems, from traditional crypt-analysis to modern web-focused techniques. Discover the gap in implementing security measures and how universities can bridge this disparity. Delve into the history, challenges, and implications of timing vulnerabil
0 views • 26 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Discussion on Timing Mask Requirement for ULSUP-TDM in RAN4#94e Meeting
In the RAN4#94e and #94e-Bis meetings, discussions were held on the timing mask requirement for ULSUP-TDM, particularly focusing on sub-topics like evaluating uplink timing differences between LTE and NR, clarifying present time mask conditions, and testing time mask requirements. The key issue cent
0 views • 4 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Understanding Static Timing Analysis in Advanced VLSI Design
Static timing analysis is a crucial aspect of VLSI design, helping predict chip performance before fabrication. This article explores the importance of static timing analysis, its effectiveness, and the limitations of dynamic simulation tools like SPICE. Learn about the challenges in testing critica
0 views • 76 slides
Understanding Sequential Circuit Timing and Clock Frequency
Sequential circuit timing is crucial for designing digital systems. The minimum clock period, slack values, clock frequency, and critical paths play key roles in determining the operational speed and performance of sequential circuits. By analyzing flip-flop timing parameters, combinatorial logic de
0 views • 20 slides
Understanding Variable Valve Timing (VVT) in Internal Combustion Engines
Variable Valve Timing (VVT) optimizes engine performance by adjusting valve duration, timing, and lift according to engine speed, enhancing torque, power, and fuel efficiency. VVT operates by varying intake valve opening/closing, regulating valve timing, and adjusting lift for better volumetric effi
0 views • 14 slides
Understanding DDoS Attacks: Simulation, Analysis & Defense
Delve into the world of Distributed Denial of Service (DDoS) attacks with this comprehensive study covering the architecture, advantages, bot installation phases, attack methods, defenses, and simulation. Learn about the detrimental impact of DDoS attacks on servers, their multi-tiered structure, an
0 views • 20 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides
Understanding Side Channels and Information Hiding Techniques in Advanced Information Assurance
This content covers various aspects of advanced information assurance, focusing on side channels and information hiding techniques such as digital watermarking, steganography, and covert channels. It discusses the concept of side-channel attacks, types of system and network channels, fault attacks,
0 views • 24 slides