Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Tamil Nadu Uniformed Service Recruitment Board (TNUSRB)
Tamil Nadu Uniformed Service Recruitment Board (TNUSRB) \nTamil Nadu Uniformed Services Recruitment Board (TNUSRB) was established in 1991 by the Government of Tamil Nadu to recruit individuals for the state\u2019s uniformed services, which include the Police, Prison, and Fire and Rescue Services.\
6 views • 5 slides
JENIS-JENIS RELASI
Exploring various types of relations in mathematics such as reflexive, symmetric, transitive, and equivalence relations with examples. Understand the definitions and properties of each type to enhance your comprehension of mathematical concepts.
2 views • 10 slides
Understanding TSP Fees: A Guide for Federal Pension Advisors
Unlock the full potential of your clients' retirement savings by mastering TSP fees. Learn to minimize costs and maximize growth with expert guidance tailored for federal pension advisors.\n
1 views • 2 slides
Plan Your Financial Future with an Advanced TSP Calculator
Federal Pension Advisors offers a comprehensive TSP Calculator, designed to help federal employees optimize their Thrift Savings Plan contributions. This user-friendly tool allows you to input various financial data, such as salary, contribution rates, and retirement goals, to generate accurate proj
1 views • 3 slides
Understanding Relationships in Bibliographic Universe
Relationships in bibliographic universe connect entities, providing context through entity-relationship models like IFLA LRM. Learn key terms, principles, and diagrams to identify relationships defined in IFLA LRM. Explore domains, ranges, inverse, recursive, and symmetric relationships. Enhance you
0 views • 23 slides
Understanding Vesting in the Thrift Savings Plan (TSP) and Retirement Saving Importance
Explore the concept of vesting in the Thrift Savings Plan, learn why saving for retirement is crucial, and discover the benefits of early investing. Delve into the Blended Retirement System components and reasons to prioritize retirement savings for financial security.
0 views • 23 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Understanding the Unique Features of Phylum Cnidaria in Life Science
Phylum Cnidaria comprises diverse marine animals like jellyfish, sea anemones, corals, and Hydra, exhibiting radially symmetric bodies with unique structures called cnidocytes. These cnidocytes serve as sensory-effector cells that contain specialized stinging organelles called cnidae, aiding in defe
0 views • 7 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
1 views • 17 slides
Advanced Troubleshooting Guide for P2P Connectivity in ISP and Wide Networks
This troubleshooting guide is tailored for operators, network experts, and engineers dealing with Dahua P2P NAT traversal protocol issues. It covers different types of NAT, including Full Cone NAT, Restricted Cone NAT, Port Restricted Cone NAT, and Symmetric NAT, providing insights and solutions for
0 views • 17 slides
Understanding Computer System Architectures
Computer systems can be categorized into single-processor and multiprocessor systems. Single-processor systems have one main CPU but may also contain special-purpose processors. Multiprocessor systems have multiple processors that share resources, offering advantages like increased throughput, econo
2 views • 25 slides
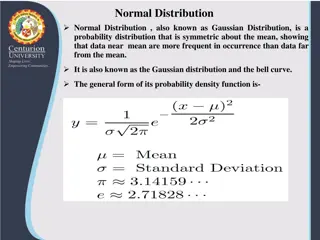
Understanding Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
1 views • 8 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Understanding Hopfield Nets in Neural Networks
Hopfield Nets, pioneered by John Hopfield, are a type of neural network with symmetric connections and a global energy function. These networks are composed of binary threshold units with recurrent connections, making them settle into stable states based on an energy minimization process. The energy
0 views • 37 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Exploring Distributed Solvers for Scalable Computing in UG
This project discusses the use of distributed solvers in UG to enable multi-rank MPI-based solvers with varying sizes, addressing the need for scalable solver codes and dynamic resource allocation. It introduces the UG solver interface, revisits the Concorde solver for TSP problems, and explores run
0 views • 14 slides
Understanding Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Understanding Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Improved Algorithms for MST and Metric-TSP Interdiction
This research discusses improved algorithms for Minimum Spanning Tree (MST) and metric Travelling Salesman Problem (TSP) interdiction to maximize the weight of MST in a graph by removing a specified number of edges. It explores various scenarios, including interdiction costs and budgets, aiming to o
0 views • 29 slides
Understanding the Traveling Salesman Problem and Its Formulation
The Traveling Salesman Problem (TSP) is a classic optimization problem seeking the shortest route visiting a set of points exactly once. This involves symmetric and asymmetric cases, ILP models, subtours, and quadratic assignment formulations. By employing decision variables and constraints, optimal
0 views • 38 slides
Emergence of Phonotactic Complexity in Early Phonological Development
Barbara L. Davis, Ph.D., from The University of Texas at Austin, presents research on phonotactic complexity in early phonological development using the Texas Speech Production (TSP) database. The study examines the emergence of phonotactic properties in speech acquisition among typically developing
0 views • 39 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Exploring Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Fertilizer Application and Cost Analysis for Soil Nutrients
This detailed agricultural analysis discusses the cost-effectiveness of applying anhydrous ammonia versus urea based on nitrogen content per pound, provides recommendations for nitrogen rates based on yield goals and soil analysis, calculates pounds of nutrients and fillers in a fertilizer blend, an
0 views • 7 slides
Understanding Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Combinatorial Optimization in Integer Programming and Set-Cover Problems
Explore various combinatorial optimization problems such as Integer Programming, TSP, Knapsack, Set-Cover, and more. Understand concepts like 3-Dimensional Matching, SAT, and how Greedy Algorithms play a role. Delve into NP-Hard problems like Set-Cover and analyze the outcomes of Greedy Algorithm se
0 views • 60 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Understanding Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides