Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
3 views • 27 slides
Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
2 views • 17 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
1 views • 28 slides
Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
1 views • 24 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
2 views • 15 slides
Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
1 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
1 views • 21 slides
Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
1 views • 32 slides
Communication Lower Bounds of Key-Agreement Protocols
Key-agreement protocols play a vital role in secure communication between parties. This document explores lower bounds of key-agreement protocols through density increment arguments, idealization of symmetric primitives, Merkle puzzles, and the impact of communication bits between Alice and Bob. Var
1 views • 10 slides
Fill Area Primitives in Computer Graphics
An overview of fill area primitives in computer graphics, including the concept of fill areas, polygon fill areas, and polygon classifications into convex and concave polygons. This module covers the efficient processing of polygons, approximating curved surfaces, and generating wire-frame views of
0 views • 63 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
1 views • 14 slides
Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Graphics Output Primitives and Coordinate Reference Frames
Graphics output primitives and coordinate reference frames play a crucial role in describing scenes and drawing basic geometric structures in 2D space. These concepts involve defining points, drawing lines, and understanding pixel coordinates within a coordinate system. Absolute and relative coordin
5 views • 35 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
1 views • 11 slides
Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides
Symmetric Encryption and Basic Terminology
This content covers symmetric encryption techniques, substitution and transposition methods, rotor machines, and basic cryptographic terminology such as plaintext, ciphertext, cipher, and key. It also discusses the requirements and assumptions for secure symmetric encryption, and the model of symmet
0 views • 49 slides
Classical Encryption Techniques Overview
Delve into the realm of classical encryption techniques with insights on symmetric encryption, basic terminology, symmetric cipher model, and requirements for secure encryption. Explore the foundations of cryptography, different encryption operations, and the central problem in symmetric cryptograph
0 views • 65 slides
Practical Cryptography Topics: AES and Substitution Permutation Networks
Dive into the world of practical cryptography with insights into the Advanced Encryption Standard (AES) and Substitution Permutation Networks. Explore the history of AES, its design principles, key sizes, and basic operations like AddRoundKey, SubBytes, ShiftRows, and MixColumns. Understand the sign
1 views • 24 slides
IEEE 802.11-21/1774r0 ARC Clause 6: Overview of Management Primitives
This content delves into Clause 6 of IEEE 802.11-21/1774r0, focusing on the overview of management primitives such as SME, MLME, PLME, and SAP. It discusses the communication between SME and MAC, generic management primitives dealing with MIBs, and MLME SAP Interface services in an abstract manner.
0 views • 13 slides
Basic Cryptography
Cryptography is a mathematical method used to protect information in modern computing. This course covers cryptographic primitives such as hash functions, symmetric and asymmetric encryption, digital signatures, and their applications. Learn about the importance of cryptographic hash functions, usin
0 views • 19 slides
Synchronization and Scaling Challenges
Study the impact of synchronization on scaling, exploring hardware artifacts and higher-level primitives. Learn how synchronization ensures coordination, the hindrance to scalability, and the overheads that arise. Understand basic hardware artifacts like CAS, TAS, FAI, and synchronization primitives
0 views • 53 slides
OpenGL Primer: Drawing Graphics Primitives and Rendering Polygons
This content covers fundamental concepts of OpenGL, including drawing graphics primitives, rendering polygons as points, outlines, or solids, and working with buffers. It explains the use of OpenGL functions for defining points, lines, triangles, and polygons, along with techniques for adjusting ren
0 views • 34 slides
Efficiency Improvement in L0 Performance Simulation Using Primitives Alignment
In the L0 performance simulation scenario presented, the alignment of primitives from detectors within timeslots plays a crucial role in enhancing trigger efficiency. Timeslot width expansion to accommodate measurement errors and the impact of detector primitive alignment on resolution are discussed
1 views • 10 slides
Investigating Semantic Primitives Using an OWL-based Ontology
The investigation focuses on identifying semantic primitives in English using an OWL-based ontology approach. By analyzing basic concepts and frequent words, the study aims to determine the minimal set of semantic relations essential for logical representation, emphasizing the importance of minimizi
0 views • 22 slides
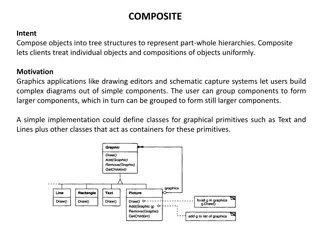
Representing Part-Whole Hierarchies with Composite Pattern
The Composite pattern allows for composing objects into tree structures to represent part-whole hierarchies, enabling clients to treat individual objects and compositions uniformly. This pattern is commonly used in graphics applications for creating complex diagrams out of simple components. By defi
0 views • 43 slides
Understanding Synchronization Primitives in Concurrent Programming
Explore the dangers of sharing data without synchronization and learn about hardware and software primitives to address this issue in concurrent programming. Discover the risks of conflicting increments in shared counters among threads and the potential solutions to ensure data integrity and reliabi
0 views • 65 slides
Unclonable Secret Sharing and Quantum Primitives Overview
Explore the concept of unclonable secret sharing, its implications in quantum cryptography, and the advancement of quantum primitives such as quantum key distribution and quantum copy-protection. Discover the potential of unclonable encryption in preventing data copying by cloud servers, and delve i
0 views • 23 slides
Understanding IEEE 802.15.8 Architecture for WPANs
Explore the detailed architecture of IEEE 802.15.8 for Wireless Personal Area Networks (WPANs), delving into MAC information flow, service primitives, and management aspects. This document offers insights into the organization of MAC layers, access points, and data primitives for efficient network o
0 views • 14 slides
Understanding Independent and Symmetric Channels in Information Theory
Explore the concepts of independent and symmetric transmission in information theory, including how they differ from noiseless channels. Learn about the properties of symmetric channels like Binary Symmetric Channels (BSC) and Ternary Symmetric Channels (TSC). Discover how to specify and model diffe
1 views • 5 slides
Idealized Model for Cryptographic Primitives and Indifferentiability Framework
Explore new notions and constructions in public key crypto-systems, leakage resilience, related-key attack PKE, and idealized models for cryptographic primitives such as hash functions, random oracles, and more. Learn about the concept of Ideal NIKE and the Indifferentiability Framework in the conte
0 views • 20 slides
Hardware Description Language Overview: Verilog, HDL, and Primitives Explained
Learn about Hardware Description Language (HDL) and its key components like Verilog and Primitives. Explore how HDL is used to describe digital system hardware, the concepts behind it, and its significance in integrated circuit design.
0 views • 16 slides