Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
AQA Level 2 Certificate in Further Maths
The AQA Level 2 Certificate in Further Maths is designed for high-achieving students to develop advanced skills in algebra, geometry, calculus, matrices, trigonometry, functions, and graphs. The course covers topics like number fractions, decimals, algebraic fractions, coordinate geometry, calculus,
7 views • 9 slides
Exporting STATA Results to Excel Using PutExcel Feature
Learn how to utilize the PutExcel feature in STATA to effortlessly export your results to an Excel file. With PutExcel, you can export matrices, stored results, images, estimation tables, and even add formulas for calculations. This tool streamlines the process of transferring statistical data to Ex
6 views • 32 slides
Matrix Systems in Restorative Dentistry: A Comprehensive Overview
Understanding the role of matrices and retainers in restorative dentistry is crucial for achieving optimal results in direct restorative procedures. This article covers the definitions, ideal requirements, functions, and parts of matrices, providing valuable insights into their importance and usage
1 views • 55 slides
2x2 Matrices in Political Science: An Irreverent Perspective
Delve into the world of 2x2 matrices in political science with a humorous twist, uncovering their foibles, fallacies, and effectiveness. From youthful rigidity to complex behavioral continuums, this unconventional take on matrices unveils their application in various scenarios like spouse choices, b
2 views • 34 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
2 views • 27 slides
Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
2 views • 17 slides
Linear Transformations and Matrices in Mathematics
Linear transformations play a crucial role in the study of vector spaces and matrices. They involve mapping vectors from one space to another while maintaining certain properties. This summary covers the introduction to linear transformations, the kernel and range of a transformation, matrices for l
1 views • 85 slides
Matrices in Precalculus: Order, Augmented Matrix, and Row-Echelon Form
Delve into the world of matrices in Precalculus with a focus on identifying matrix orders, creating augmented matrices for systems of equations, transforming matrices into row-echelon form, and solving linear equations using matrices. Explore elementary row operations, row-echelon form, and reduced
2 views • 37 slides
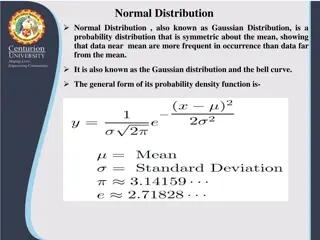
Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
2 views • 8 slides
Singular Value Decomposition
The Singular Value Decomposition (SVD) is a powerful factorization method for matrices, extending the concept of eigenvectors and eigenvalues to non-symmetric matrices. This decomposition allows any matrix to be expressed as the product of three matrices: two orthogonal matrices and a diagonal matri
0 views • 35 slides
Immobilization of Enzymes in Biochemistry
Enzyme immobilization involves confining enzyme molecules to a distinct phase from substrates and products, attaching them to solid matrices for enhanced specificity and reduced inhibition. Inert polymers or inorganic materials are used as carrier matrices with methods like physical adsorption onto
0 views • 24 slides
Introduction to Matrices in Mathematical Analysis
Matrices play a crucial role in simplifying complex systems of equations and are well-suited for systematic mathematical treatments and computer computations. This introduction covers the definition of matrices, their properties such as size and notation, and various types of matrices including colu
0 views • 77 slides
Matrices and Solving Equations in Electrical Engineering
Matrices play a crucial role in solving linear equations in Electrical Engineering applications. Learn about matrix structures, special matrices, inverses, transposes, system of linear equations, and solving methods using MATLAB/Python. Explore the application of matrices in solving voltage-current
2 views • 24 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Rank in Matrices
Rank in matrices represents the maximum number of independent columns, with implications for pivot columns, basic variables, and free variables. The rank of a matrix is essential for determining its properties and dependencies. Learn about rank-deficient matrices, basic versus free variables, and mo
0 views • 7 slides
Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Learning-Based Low-Rank Approximations and Linear Sketches
Exploring learning-based low-rank approximations and linear sketches in matrices, including techniques like dimensionality reduction, regression, and streaming algorithms. Discusses the use of random matrices, sparse matrices, and the concept of low-rank approximation through singular value decompos
0 views • 13 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
MATLAB Basics for Electrical Engineering Students
In this instructional content from the Government Polytechnic West Champaran Department of Electrical Engineering, students are introduced to the fundamentals of MATLAB. Topics covered include transposing matrices, concatenating matrices, matrix generators, arrays, entering matrices, and manipulatin
0 views • 48 slides
Eigenvectors in Linear Algebra
Explore the concept of eigenvectors in linear algebra, covering topics such as linear transforms, eigenvalues, symmetric matrices, and their practical applications. Learn how eigenvectors represent directions in which a transformation only stretches or compresses without changing direction, and unde
0 views • 25 slides
Linear Algebra Concepts: Systems of Equations, Orthogonal Matrix, and Quadratic Forms
Explore the concepts of simultaneous linear equations, homogeneous and non-homogeneous systems, orthogonal matrices, and various types of quadratic forms in linear algebra. Learn about the characteristics of positive definite, semi-positive definite, and negative definite quadratic forms represented
0 views • 7 slides
Hazard Matrices and Impact-Based Forecasting
Hazard matrices are essential tools for coordinating emergency preparedness and response by categorizing primary, secondary, and tertiary effects of hazards. Impact matrices help organizations assess risks and determine potential impacts of events, allowing for better planning and mitigation strateg
0 views • 12 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Solving Systems of Equations using Inverse Matrices
Learn how to solve systems of equations using inverse matrices, find the determinant of matrices, use matrix multiplication, calculate the inverse matrix, and apply it to solve simultaneous equations. Explore examples and applications in investment scenarios.
0 views • 14 slides
Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Directed Graphs and Adjacency Matrices in Discrete Structures
Explore the concepts of binary relations, directed graphs, adjacency matrices, transitive closure, and walks in the context of discrete structures. Learn how vertices, edges, in-degrees, out-degrees, and self-loops are defined in directed graphs. Understand the importance of adjacency matrices in re
1 views • 28 slides
Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides