Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Understanding Relationships in Bibliographic Universe
Relationships in bibliographic universe connect entities, providing context through entity-relationship models like IFLA LRM. Learn key terms, principles, and diagrams to identify relationships defined in IFLA LRM. Explore domains, ranges, inverse, recursive, and symmetric relationships. Enhance you
0 views • 23 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
1 views • 17 slides
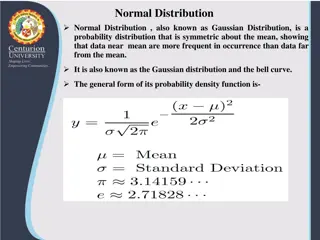
Understanding Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
1 views • 8 slides
Understanding the Normal Probability Curve
The Normal Probability Curve, also known as the normal distribution, is a fundamental concept in statistics. It is symmetric around the mean, with key characteristics such as equal numbers of cases above and below the mean, and the mean, median, and mode coinciding. The curve's height decreases grad
0 views • 10 slides
Overview of Basic Security Properties and Cryptography Fundamentals
This content provides an introduction to basic security properties such as confidentiality, authenticity, integrity, availability, non-repudiation, and access control. It also covers the fundamentals of cryptography, including symmetric and asymmetric encryption, public-key cryptography, and the imp
1 views • 41 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Understanding Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
Leakage-Resilient Key Exchange and Seed Extractors in Cryptography
This content discusses the concepts of leakage-resilient key exchange and seed extractors in cryptography, focusing on scenarios involving Alice, Bob, and Eve. It covers non-interactive key exchanges, passive adversaries, perfect randomness challenges, and leakage-resilient settings in symmetric-key
6 views • 35 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Cutting-edge Proton EDM Storage Ring Experiment Insights
Detailed overview of the Proton EDM Storage Ring Experiment by William Morse, highlighting challenges in neutron EDM sensitivity, magic momentum phenomenon in electric fields, and advancements in proton EDM experiment sensitivity. Explore the critical parameters related to axion physics, CP-violatio
1 views • 16 slides
Understanding Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Cryptography Concepts and Encryption Methods Overview
Exploring elementary cryptography concepts such as encryption, cryptanalysis, symmetric and asymmetric encryption algorithms like DES, AES, and RSA. Delve into key exchange protocols, digital signatures, cryptographic hash functions, and the process of encryption and decryption in a cryptosystem.
0 views • 23 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Understanding Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Communication Lower Bounds of Key-Agreement Protocols
Key-agreement protocols play a vital role in secure communication between parties. This document explores lower bounds of key-agreement protocols through density increment arguments, idealization of symmetric primitives, Merkle puzzles, and the impact of communication bits between Alice and Bob. Var
0 views • 10 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Practical Aspects of Modern Cryptography: November 2016
Exploring session-based protocols, SSL/TLS, certificates, and public key infrastructure, this presentation delves into the motivation behind secure online interactions, discussing the importance of verifying identities, ensuring data confidentiality, maintaining message integrity, and authenticating
0 views • 137 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Exploring Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Understanding Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides
New Directions in Cryptography: Harta Dwijaksara, Yi Jae Park
Explore the world of cryptography through this comprehensive guide covering topics such as conventional cryptography, public key cryptography, one-way authentication, trap doors, computational complexity, and more. Learn about the importance of privacy in communications and the key principles behind
0 views • 20 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides
Understanding Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides