Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Understanding Hash Maps: A Common Data Structure
In this module, learn about Hash Maps, a common data structure used in various programming languages like Java, C#, C++, Python, and PHP. Hash Maps allow you to store key-value pairs without duplicate keys, making it efficient for mapping relationships between data elements. Explore how to declare,
6 views • 16 slides
Quick Hash Delivery in Ottawa Canafast.ca
Craving premium hashish in Ottawa? Look no further. Our service offers prompt and discreet hash delivery right to your doorstep in Ottawa. Indulge in the finest hash products without leaving the comfort of your home.
3 views • 6 slides
Understanding Hash Join Algorithm in Database Management Systems
In this lecture, Mohammad Hammoud explores the Hash Join algorithm, a fundamental concept in DBMS query optimization. The algorithm involves partitioning and probing phases, utilizing hash functions to efficiently join relations based on a common attribute. By understanding the intricacies of Hash J
1 views • 41 slides
Understanding Different Types of SQL Joins
Explore the various types of SQL joins such as INNER JOIN, LEFT (OUTER) JOIN, RIGHT (OUTER) JOIN, and FULL (OUTER) JOIN. Learn how each type functions and the syntax for implementing them. Get insights into examples of INNER JOIN and LEFT OUTER JOIN operations to enhance your SQL knowledge.
0 views • 26 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
1 views • 17 slides
Understanding Joins in DBMS: INNER JOIN, LEFT JOIN, and Examples
Join statements in DBMS, such as INNER JOIN and LEFT JOIN, are used to combine data from multiple tables based on a common field. INNER JOIN selects rows that satisfy a condition from both tables, while LEFT JOIN returns all rows from the left table and matching rows from the right table. Examples i
3 views • 19 slides
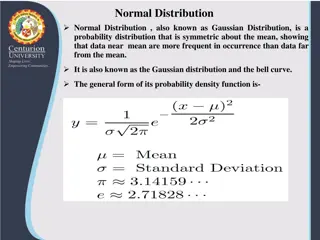
Understanding Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
1 views • 8 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Buy Playboy Hash Online - globaldrugsstore.com
Buy Playboy Hash Online is an Indica dominant hash that originated from Morocco where it is widely known to produce some of the best hash in the world. This hash is quite potent but very easy on the throat. It smokes incredibly smooth and has a sweet
1 views • 3 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Massively Parallel Sort-Merge Joins in Main Memory Multi-Core Database Systems
Explore the hardware trends and techniques used at Technische Universität München for massively parallel sort-merge joins in main memory multi-core database systems. The research focuses on exploiting fast main memory access, parallelizing algorithms, and optimizing performance in a NUMA environme
0 views • 29 slides
Understanding Distributed Hash Tables in Peer-to-Peer Systems
Distributed Hash Tables (DHTs) are a fundamental component in organizing nodes in peer-to-peer networks. By using hash functions to assign keys to peers, DHTs enable efficient storage and retrieval of objects. Peers in a DHT are responsible for storing and managing key-value pairs, with each key bei
0 views • 31 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Understanding Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Understanding Joins, Views, and Subqueries in SQL
This informative guide delves into the essentials of joining, viewing, and utilizing subqueries in SQL. Explore multi-table selects, various join types, and examples of inner, left outer, and right outer joins, offering a clear understanding of how to manipulate and combine data in SQL queries effec
0 views • 28 slides
Understanding Table Joins in SQL
Exploring various types of table joins in SQL, including Cross Join, Inner Join, Outer Join, and Self Join. Learn how these joins work, when to use them, and see practical examples for better comprehension.
0 views • 22 slides
Understanding Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Understanding Joins in DBMS: Types and Operations
Joins in DBMS are binary operations that allow you to combine data from multiple tables using primary and foreign keys. There are two main types of joins: Inner Joins (Theta, Natural, EQUI) and Outer Joins (Left, Right, Full). Inner joins help merge data from tables based on specified conditions, wh
0 views • 16 slides
Understanding SQL Joins in ASP.Net 2.0 with Visual Studio 2005
Exploring the importance of query joins in SQL, this instructional content delves into inner, outer, left outer, and right outer joins for integrating data from multiple database tables in ASP.Net 2.0. Detailed guidance is provided on setting up SQL databases in Visual Studio .NET 2005, creating tab
0 views • 11 slides
Understanding Join Algorithms in Database Systems
This presentation delves into the intricacies of join algorithms in DBMS, focusing on various techniques such as simple nested loops join, block nested loops join, index nested loops join, sort-merge join, and hash join. The importance of optimizing joins to avoid unnecessary cross-products is empha
0 views • 67 slides
Overview of Different Types of SQL Joins
Examine the various types of SQL joins including INNER JOIN, LEFT JOIN, RIGHT JOIN, and FULL JOIN. Understand the differences between these join types and how they retrieve data from multiple tables based on specified conditions. Explore practical examples of joining tables and creating relationship
0 views • 18 slides
Accelerating Lemma Learning Using Joins in Satisfiability Modulo Theories
Explore the use of joins in accelerating lemma learning within the context of Satisfiability Modulo Theories (SMT). The study covers various SMT applications at Microsoft and delves into the development of the Z3 solver. Key topics include theories, arithmetic operations, array theory, uninterpreted
0 views • 25 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Understanding Overlay Networks and Distributed Hash Tables
Overlay networks are logical networks built on top of lower-layer networks, allowing for efficient data lookup and reliable communication. They come in unstructured and structured forms, with examples like Gnutella and BitTorrent. Distributed Hash Tables (DHTs) are used in real-world applications li
0 views • 45 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Understanding Hash Functions in Data Structures
Hash functions are crucial in storing data efficiently by converting a sized amount of data into a single integer. They are used to generate hash values, hash codes, or hash sums, which serve as indexes in arrays. The hash function should be quick to compute and distribute hash addresses uniformly t
0 views • 200 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Exploring Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Understanding the Relationship between Decisional Second-Preimage Resistance and Preimage Resistance in Cryptographic Hash Functions
This work delves into the subtle question of when Decisional Second-Preimage Resistance (SPR) implies Preimage Resistance (PRE) in hash functions. It presents a tool for enabling tight security proofs for hash-based signatures by exploring the success probability of adversaries against collision res
0 views • 25 slides
Foundations of Cryptography: Digital Signatures and Collision-Resistant Hash Functions
Foundations of Cryptography explores the construction of digital signature schemes and collision-resistant hash function families using one-way functions and safe primes. The content delves into the concept of collision-resistant hash functions and their construction from the discrete logarithm prob
0 views • 31 slides
Foundations of Cryptography: Lecture 12 - Digital Signatures and Collision-Resistant Hash Functions
The lecture covers the construction of collision-resistant hash functions from discrete log, the security behind it, and the implications for digital signature schemes. It delves into the theoretical foundations of cryptography, showcasing the interplay between one-way functions, hash functions, and
0 views • 25 slides
Understanding Hash Tables and Hashing Concepts in Computer Algorithms
This content delves into the concept of Hash Tables, covering topics such as the support for dictionary operations, achieving constant time through direct address tables, case studies in web server maintenance, and an exploration of hashing functions and collision avoidance. It also touches upon key
0 views • 40 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides