Affirming Mental Healthcare for LGBTQ+/POC: Understanding the Importance of Client Identities
This presentation delves into the significance of acknowledging client identities in mental healthcare for LGBTQ+ and POC individuals. It covers terminology related to gender identity, sexual orientation, and gender affirmation, emphasizing the importance of respecting diverse identities and experie
3 views • 19 slides
Enhancing Peer Review Quality Through Double-Blind Reviewing in ACM Conferences
Double-blind reviewing (DBR) is increasingly recognized for its effectiveness in reducing biases, improving article quality, and practicality in ACM conferences. Studies show evidence of gender and institutional biases in single-blind reviewing, while DBR enhances fairness and credibility. DBR revie
0 views • 9 slides
Understanding Cultural Identity in Communication Studies
The importance of identity in communication is discussed in relation to cultural, racial, ethnic, gender, national, regional, organizational, personal, and cyber/fantasy identities. Identity development influences social roles and communication interactions. Various social identities shape our self-
1 views • 28 slides
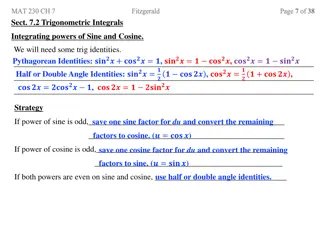
Trigonometric Integrals: Strategies and Identities
Learn useful trigonometric identities and strategies for integrating powers of sine and cosine. Understand when to use Pythagorean, Half or Double Angle Identities, and how to handle odd or even powers efficiently. Examples provided for clarity.
1 views • 14 slides
Affirming Trans & Queer Identities: Exploring Genders and Sexualities
Today's session focuses on exploring and affirming diverse genders and sexualities, while also providing wellness tips for self-love. Topics include gender identities, community agreements, wellness advice, and discussions on sex assigned at birth.
2 views • 19 slides
Understanding Bibliographic Identities and Nomen Clusters in Cataloging
Explore the concept of bibliographic identities, factors influencing the use of Nomens for individuals, and the relationship between Nomens and cataloging rules. Learn how one entity may have multiple Nomens and the significance of context in distinguishing between distinct bibliographic identities.
0 views • 12 slides
Understanding Gender-Based Violence and LGBTI Identities in Interagency Case Management Training
This training module focuses on understanding different terms and definitions related to LGBTI identities, identifying barriers to care for LGBTI survivors, and providing services in a safe and supportive manner. It also discusses the risks of gender-based violence faced by LGBTI-identified individu
0 views • 16 slides
Understanding Cultural Identity in Intercultural Communication
Cultural identity is a vital aspect of intercultural communication, influencing individuals' perceptions and interactions. This complex concept encompasses various social identities such as racial, ethnic, gender, national, regional, organizational, personal, cyber, and fantasy identities. Developin
2 views • 12 slides
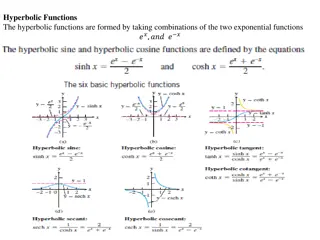
Understanding Hyperbolic Functions and Their Inverses
This content delves into the world of hyperbolic functions, discussing their formation from exponential functions, identities, derivatives, and inverse hyperbolic functions. The text explores crucial concepts such as hyperbolic trigonometric identities, derivatives of hyperbolic functions, and integ
0 views • 9 slides
Trigonometry: Identities, Equations, and Problem Solving Techniques
Explore various trigonometric identities, solve trigonometry equations, and learn problem-solving techniques in trigonometry. Discover how to use basic trigonometry to find missing sides, understand trigonometric identities, and tackle challenging trigonometry problems involving sine, cosine, and ta
1 views • 17 slides
Understanding Intersectionality: Navigating Power and Identities
Explore the significance of intersectionality as a powerful lens to comprehend how various identities intersect and clash, impacting individuals in terms of power dynamics. Learn why recognizing intersecting identities is crucial for fostering awareness and inclusivity. Engage in discussions to refl
0 views • 11 slides
What is the best way to recover my stolen Bitcoin wallet?
If you've fallen victim to a Bitcoin scam, recovering your stolen funds can be a daunting task. However, with the right steps and the assistance of a professional recovery company, you can increase your chances of success. Here is a guide to help you
0 views • 15 slides
How to Retrieve Stolen Bitcoin: Reviews on Recuva Hacker Solutions
The unfortunate reality of the burgeoning cryptocurrency market is the prevalence of scams and theft. If you have had your Bitcoin stolen, the path to recovery can be complex and fraught with challenges. However, there are professional services avail
0 views • 15 slides
How can I recover my stolen Bitcoin from the scammer?
When faced with the unfortunate situation of stolen Bitcoin, it's important to know that recovery is possible. If your Bitcoin has been hacked, there are steps you can take to attempt to retrieve your lost funds.\nFirst, understand that while tracing
0 views • 15 slides
7 Guaranteed Steps to Recover Scammed Bitcoin and Retrieve Stolen Crypto
Losing your cryptocurrency to scams or theft can be a devastating experience, but recovery is possible. By following these seven steps, you can increase your chances of retrieving your stolen crypto. Recuva Hacker Solutions is a trusted service that
0 views • 15 slides
Successful Cases of Recovering Stolen Cryptocurrency
Cryptocurrency theft has been a significant issue since the advent of digital currencies. However, the success stories of recovering stolen cryptocurrency demonstrate that with the right expertise and tools, lost assets can often be retrieved. Recuva
0 views • 15 slides
Best Tools for Tracking and Recovering Stolen Cryptocurrency
Cryptocurrency theft is a growing concern in the digital age, but recovery is possible with the right tools and expertise. Recuva Hacker Solutions offers professional services to help track and recover stolen cryptocurrency, providing a lifeline to t
0 views • 15 slides
Can you really hire a professional hacker to retrieve stolen crypto?
Can you really hire a professional hacker to retrieve stolen crypto? Where do you find\u00a0one?\nWith the rise of cryptocurrency theft, many victims wonder if hiring a professional hacker can help recover their stolen assets. The answer is yes, but
0 views • 15 slides
If truly stolen crypto can be recovered in some way, can someone share the steps
1. Identify the Theft\n\nThe first step in recovering stolen cryptocurrency is to accurately identify and document the theft. This involves:\n\nNoticing unauthorized transactions in your wallet or exchange account.\nRecording all relevant transaction IDs, wallet addresses, and timestamps.\nCollectin
0 views • 15 slides
Understanding Identity and Equity in Education
Exploring the impact of personal identity on student success, the importance of educational equity, and the significance of student and educator identities within the learning partnership. The content delves into constructs like motivation, self-knowledge, self-direction, and relationships that cont
0 views • 15 slides
Understanding Hawaiian Place-Based Identities and Moon Phases
Explore the profound connection between Hawaiian place-based identities and the phases of the moon, uncovering traditional practices, weather disturbances, and emergency management planning rooted in ancestral knowledge and oral culture.
0 views • 28 slides
Post-War Reflections: Voices and Identities of the 1950s and 1960s
Exploring the themes of post-war literature from the 1950s and 1960s, this analysis delves into the tensions, crises, and identities shaped by the era. Writers of the time grapple with finding a voice that reflects the uncertainty of a changing world order, encompassing disillusionment, anger, and i
0 views • 16 slides
Understanding Ethnic Literature
Ethnic literature focuses on the unique cultural identities of different ethnic groups within society, shaped by language, nationality, heritage, and customs. It explores how ethnicity influences social dynamics, discrimination, and group formation. Social sciences and psychology delve into the comp
0 views • 17 slides
Understanding Funds of Knowledge and Adolescent Identities in Education
This lesson explores the concept of funds of knowledge, emphasizing the value of culturally diverse students' expertise in the educational process. It delves into identifying different types of knowledge students bring and reframing misconceptions. Additionally, it examines adolescent identities, hi
0 views • 27 slides
Linguistic Analysis of Drag Queen Identities on RuPaul's Drag Race
This analysis explores how drag queens construct their identities through language on the reality television show RuPaul's Drag Race. The study delves into linguistic patterns, cultural ideologies, and social meanings utilized by drag queens, highlighting the multi-layered and polyphonous nature of
0 views • 17 slides
Supporting Trans and Gender Diverse Students in Educational Settings
Explore the multi-faceted journeys and identities of both staff and students in educational institutions, focusing on supporting trans and gender diverse individuals. Delve into stages of their journeys, diverse spheres of experiences, and other intersecting identities that shape their paths. Engage
0 views • 13 slides
Exploring Stolen Childhood in 'Lost Spring' by Anees Jung
Anees Jung's "Lost Spring" sheds light on the heart-wrenching realities of child labor and stolen childhood in India. Through poignant narratives, the author showcases the struggles of children like Saheb and Mukesh, whose innocence and joy are robbed as they are forced into labor due to socio-econo
0 views • 15 slides
Understanding Intersectionality in the South African Context
Prof. Amanda Gouws discusses intersectionality in the South African experience, touching on issues of gender, race, and discrimination. Kimberle Chrenshaw's work on gender and race oppression is highlighted, emphasizing the complexity of identities and power dynamics. The concept of a matrix of domi
0 views • 10 slides
Unpacking Identities: Hispanic, Latinx, and Ch/Xicanx
Delve into the complexities of Hispanic, Latinx, Chicano/a, and Xicano/a identities through the insightful exploration of language's power in serving marginalized communities like youth. Understand the impact of terms, the inclusivity offered by the "X" suffix, and the historical context behind Hisp
0 views • 16 slides
Understanding Trigonometric Identities for Double Angles
Special identities like the Pythagorean identity and double angle identities for sine and cosine are explored in this content. The Pythagorean identity states that cosine squared plus sine squared equals one, while the double angle identities provide formulas for cosine of double angles. Through the
0 views • 13 slides
Exploring Living Educational Theory Research in Professional Development
Living Educational Theory Research plays a crucial role in shaping post-professional identities and expanding ethical responsibilities beyond conventional standards in physiotherapy educational practice. By engaging in this research, professionals can transform their practices, incorporate existing
0 views • 8 slides
Exploring Matrix Identities in Strong Proof Systems
This study delves into the complexity of matrix identities as potential challenges for robust proof systems. Through new algebraic techniques, the research aims to propose and analyze non-commutative polynomial identities over matrices, shedding light on lower bounds and conjectures for strong arith
0 views • 57 slides
Understanding Identity Theft: Risks for Teens and How to Protect Yourself
Explore the world of identity theft and its potential impact on teenagers. Learn what identity theft entails, why teens are at risk, and the evolving tactics used by criminals. Discover how stolen identities are misused and ways to prevent falling victim to such crimes.
0 views • 41 slides
Exploring the Role of Non-Native Teachers in EAP in the UK
This study delves into the identities, advantages, and challenges faced by non-native English teachers in English for Academic Purposes (EAP) in the UK. By examining the nuanced aspects of non-native identities, accent perceptions, and societal expectations, the research sheds light on the complexit
0 views • 24 slides
Unraveling Relationships and Identities in Richard II
Delve into the intricate web of relationships and identities in Shakespeare's Richard II. Explore the characters' dynamics, the significance of naming, and the ceremonial language that underpins the play's themes of power, order, and belonging in a time of political upheaval.
0 views • 21 slides
Analysis of Gender, Agency, and Nationalism in Feminist Ethnography
Explore the complexities of gender, agency, and Indian nationalism through feminist ethnography, delving into themes of family, silence, self-staging, and shifting identities. The analysis emphasizes the significance of women's agency in shaping their identities and resisting societal norms, highlig
0 views • 5 slides
Trigonometry Review and Essential Concepts Explained
Refresh your knowledge of trigonometry with a thorough review of key concepts such as SOH-CAH-TOA, trigonometric identities, Pythagorean theorem, and more. Understand the significance of standard position, terminal side of angles, unit circle intersections, quadrant signs, and the law of cosines. Ex
0 views • 8 slides
Exploring Digital Diasporas: Audience Dynamics and Cultural Identities
In this comprehensive study, Professor Janet Wilson delves into the evolving landscape of mediatised digital diasporas, examining audience behaviors, consumption patterns, and production practices. The research sheds light on the intersection of technology, migration, and media, offering insights in
0 views • 12 slides
Reflections on the Interconnectedness of Identities in a Finnish College Setting
The text explores the intricacies of identities and belonging in a Finnish college, touching on themes of cultural diversity, social dynamics, and personal introspection. Through the interactions between characters like Ashraf and the students, the narrative delves into the complexities of self-perc
0 views • 10 slides
Psychic Finds Lost Vehicles
Tonya Somers a Psychic finds lost or stolen vehicle for you. Lupe was able to find the lost vehicle from where it was revealed in readings by Tonya. It was found in the condition as mentioned. \n \/\/ \/i-found-my-stolen-car-right-where-you-said-it-w
1 views • 6 slides