Metropolitan NY-NJ Storm Surge Working Group: Resilience Conference 2024
The Metropolitan NY-NJ Storm Surge Working Group focuses on protecting the region against catastrophic flooding from ocean storm surges and rising sea levels. Key topics include storm surge barriers, flood protection proposals, and sea level rise projections. The group emphasizes a regional approach
0 views • 39 slides
Stochastic Storm Transposition in HEC-HMS: Modern Techniques and Applications
Explore the innovative methods and practical applications of Stochastic Storm Transposition (SST) in the context of HEC-HMS. Delve into the history, fundamentals, simulation procedures, and benefits of using SST for watershed-averaged precipitation frequency analysis. Learn about the non-parametric
3 views • 41 slides
Rising Above the Wreckage: Unparalleled Storm Restoration Expertise
In the aftermath of a storm, uncertainty looms large, but so does our unwavering resolve to restore normalcy. As your trusted Storm Restoration Company, we navigate the debris with precision and proficiency. With a suite of restoration services tailored to your needs, we reclaim what was lost, reinf
11 views • 5 slides
Navigating the Depths Storm Sewer Inspection Camera Insights in Walnut Creek
Cloggone Plumbing and Drain, a leading provider of professional plumbing and drain services in Walnut Creek, California, is proud to share its expertise in storm sewer inspection camera technology. This powerful tool, storm sewer inspection camera in Walnut Creek, allows us to delve deep into the un
2 views • 6 slides
Storm Shelters In Mississippi | Gnprollc.com
Gnprollc.com offers the best storm shelters in Mississippi, designed to provide maximum protection and peace of mind. Our shelters are built with the highest quality materials to ensure your safety and security during any storm.\n\n\/\/ \/storm-shelt
3 views • 1 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
Challenges and Future of EU Environmental Law Enforcement
Challenges in enforcing EU environmental law include flawed transposition by Member States, insufficient application, and lack of resources. The implementation deficit hampers effective enforcement, requiring better legislative mechanisms. Transposition of directives is crucial but complex due to va
0 views • 22 slides
Panel Stochastic Frontier Models with Endogeneity in Stata
Introducing xtsfkk, a new Stata command for fitting panel stochastic frontier models with endogeneity, offering better control for endogenous variables in the frontier and/or the inefficiency term in longitudinal settings compared to standard estimators. Learn about the significance of stochastic fr
0 views • 13 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Generalization of Empirical Risk Minimization in Stochastic Convex Optimization by Vitaly Feldman
This study delves into the generalization of Empirical Risk Minimization (ERM) in stochastic convex optimization, focusing on minimizing true objective functions while considering generalization errors. It explores the application of ERM in machine learning and statistics, particularly in supervised
0 views • 11 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Establishing a Storm Water Enterprise Fund in Groton: A Solution for Regulatory Compliance
Town Meeting warrants article proposes the establishment of a Storm Water Enterprise Fund to meet new storm water mandates in Groton, Massachusetts. The fund aims to support compliance with EPA's Phase 2 Storm Water Program, addressing issues related to water quality standards, pollution reduction,
0 views • 13 slides
Storm Water Management Program Overview - May 15th, 2014 Committee Meeting
This program overview from the Committee Meeting on May 15th, 2014 in New Braunfels covers the MS4 program, HCP, storm water permit updates, TPDES regulations, SWMP, permit requirements, and program implementation details including public education, illicit discharge detection, construction site run
1 views • 19 slides
Analysis of "Storm on the Island" by Seamus Heaney
Storm on the Island" by Seamus Heaney is a poem about waiting out a storm on a remote island. The narrator describes the fear and desperation felt as nature rages outside their sturdy home. Heaney's use of language devices, structure, and form effectively convey the power and uncontrollable force of
0 views • 9 slides
Exploring Dust Storm Effects at Syrtis and Jezero
This research delves into the impact of dust storms at Syrtis and Jezero, focusing on the grid configurations, dust lifting phases, and storm evolution. Through detailed analysis of different phases, such as dust lifting and decaying, the study sheds light on the self-organizing nature of dust storm
5 views • 17 slides
Understanding the Greater Elkhart County Stormwater Partnership
The Greater Elkhart County Stormwater Partnership plays a vital role in managing stormwater in the region. Through initiatives such as the Municipal Separate Storm Sewer System (MS4) and Storm Water Quality Management Plans (SWQMP), they address key control measures to prevent pollution and ensure w
0 views • 18 slides
NCDC User Engagement Services Branch Storm Data Briefing
This briefing presents information on storm data and the Storm Events Database provided by NCDC User Engagement Services Branch. It includes details on data contacts, data overview, data flow, and access to the Storm Events Database. The dataset covers a chronological listing of various weather phen
0 views • 7 slides
Maximizing Bacteria Removal from Storm Water through Filteration Research
This term paper report focuses on the removal of bacteria from storm water using different filteration methods. The study reviews research on sand media filters and explores the efficiency of bio sand filters in removing pathogens such as E. coli, Cryptosporidium, and Salmonella. Key findings highli
7 views • 8 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Stochastic Coastal Regional Uncertainty Modelling II (SCRUM2) Overview
SCRUM2 project aims to enhance CMEMS through regional/coastal ocean-biogeochemical uncertainty modelling, ensemble consistency verification, probabilistic forecasting, and data assimilation. The research team plans to contribute significant advancements in ensemble techniques and reliability assessm
0 views • 28 slides
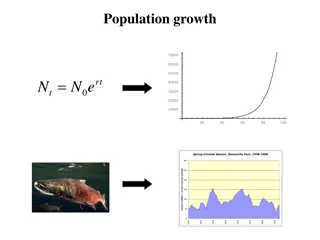
Understanding Population Growth Models and Stochastic Effects
Explore the simplest model of population growth and the assumptions it relies on. Delve into the challenges of real-world scenarios, such as stochastic effects caused by demographic and environmental variations in birth and death rates. Learn how these factors impact predictions and models.
0 views • 35 slides
Prairie Storm Coaches/Managers Meeting Agenda
Welcome to the Prairie Storm Coaches/Managers meeting focusing on various topics such as travel, tournaments, team management, medical reporting, financials, coaching requirements, and more. It covers essential information and guidelines for managing PSMHA teams effectively. From organizing team mee
0 views • 18 slides
Overview of Data Protection Law Transposition in Swaziland
Presentation on the transposition of data protection law in Swaziland, discussing the background, national assessment, purpose of the law, objectives of the SADC model law, and the approach to drafting the Data Protection Bill. This includes establishing a Data Protection Authority, harmonizing appr
0 views • 21 slides
Exploring Denotative Meaning and Translation Issues in Arabic Language
The article delves into denotative meaning, semantic repetition, synonym/near-synonym repetition, grammatical transposition, and semantic distancing techniques in Arabic language translation. It discusses how Arabic utilizes various forms of repetition and transposition that differ from English, sho
0 views • 15 slides
Multiserver Stochastic Scheduling Analysis
This presentation delves into the analysis and optimality of multiserver stochastic scheduling, focusing on the theory of large-scale computing systems, queueing theory, and prior work on single-server and multiserver scheduling. It explores optimizing response time and resource efficiency in modern
0 views • 38 slides
Approximation Algorithms for Stochastic Optimization: An Overview
This piece discusses approximation algorithms for stochastic optimization problems, focusing on modeling uncertainty in inputs, adapting to stochastic predictions, and exploring different optimization themes. It covers topics such as weakening the adversary in online stochastic optimization, two-sta
0 views • 33 slides
Crack the Code: A Journey into Transposition Ciphers
Mathematicians play a crucial role in industries like telecommunications and internet companies by condensing data and ensuring error detection. Transposition ciphers, like the Scytale used by Romans, offer a challenging way to encrypt messages. Test your skills with code-breaking challenges and exp
0 views • 4 slides
Optimal Sustainable Control of Forest Sector with Stochastic Dynamic Programming and Markov Chains
Stochastic dynamic programming with Markov chains is used for optimal control of the forest sector, focusing on continuous cover forestry. This approach optimizes forest industry production, harvest levels, and logistic solutions based on market conditions. The method involves solving quadratic prog
0 views • 27 slides
Integrating Stochastic Weather Generator with Climate Change Projections for Water Resource Analysis
Exploring the use of a stochastic weather generator combined with downscaled General Circulation Models for climate change analysis in the California Department of Water Resources. The presentation outlines the motivation, weather-regime based generator description, scenario generation, and a case s
0 views • 20 slides
Investigating Dust Storm Frequency and Extreme Drought Relationship in Arid Regions of Iran
This research by Reza Modarres and Poria Mohit Isfahani from Isfahan University of Technology explores the temporal changes in dust storm frequency in arid regions of Iran, examining how drought impacts the frequency in changing environments and the relation between extreme droughts and dust storm o
0 views • 14 slides
Understanding Stochastic Differential Equations and Numerical Integration
Explore the concepts of Brownian motion, integration of stochastic differential equations, and derivations by Einstein and Langevin. Learn about the assumptions, forces, and numerical integration methods in the context of stochastic processes. Discover the key results and equations that characterize
0 views • 6 slides
Analysis of Web Accessibility Directive Implementation by the European Disability Forum
The European Disability Forum conducted a survey on the transposition and implementation of the Web Accessibility Directive, focusing on awareness, feedback mechanisms, and examples. Results revealed challenges in transposition, dissatisfaction with outcomes, and barriers in website accessibility im
0 views • 15 slides
Introduction to Generalized Stochastic Petri Nets (GSPN) in Manufacturing Systems
Explore Generalized Stochastic Petri Nets (GSPN) to model manufacturing systems and evaluate steady-state performances. Learn about stochastic Petri nets, inhibitors, priorities, and their applications through examples. Delve into models of unreliable machines, productions systems with priorities, a
0 views • 44 slides
Integrating Physical and Social Science for Effective Storm Surge Communication
The integration of physical and social sciences is crucial for effectively communicating complex storm surge threats. Collaborative efforts involve various stakeholders like the National Weather Service, NOAA, emergency managers, social scientists, media, and private sector representatives. Strategi
0 views • 10 slides
Hurricane Matthew: After Action Report Overview
Hurricane Matthew, a Category 5 storm, impacted the Bahamas and came close to Palm Coast, causing significant rainfall and storm surges. Despite not making landfall in Palm Coast, the area experienced strong winds and moderate storm surges. The city's response included proactive preparations, strate
0 views • 18 slides
Exploring Stochastic Algorithms: Monte Carlo and Las Vegas Variations
Stochastic algorithms, including Monte Carlo and Las Vegas variations, leverage randomness to tackle complex tasks efficiently. While Monte Carlo algorithms prioritize speed with some margin of error, Las Vegas algorithms guarantee accuracy but with variable runtime. They play a vital role in primal
0 views • 13 slides
Optimal Early Drought Detection Using Stochastic Process
Explore an optimal stopping approach for early drought detection, focusing on setting trigger levels based on precipitation measures. The goal is to determine the best time to send humanitarian aid by maximizing expected rewards and minimizing expected costs through suitable gain/risk functions. Tas
0 views • 4 slides
Optimizing User Behavior in Viral Marketing Using Stochastic Control
Explore the world of viral marketing and user behavior optimization through stochastic optimal control in the realm of human-centered machine learning. Discover strategies to maximize user activity in social networks by steering behaviors and understanding endogenous and exogenous events. Dive into
0 views • 15 slides
Understanding Tradeoff between Sample and Space Complexity in Stochastic Streams
Explore the relationship between sample and space complexity in stochastic streams to estimate distribution properties and solve various problems. The research delves into the tradeoff between the number of samples required to solve a problem and the space needed for the algorithm, covering topics s
0 views • 23 slides
Efficient Training of Dense Linear Models on FPGA with Low-Precision Data
Training dense linear models on FPGA with low-precision data offers increased hardware efficiency while maintaining statistical efficiency. This approach leverages stochastic rounding and multivariate trade-offs to optimize performance in machine learning tasks, particularly using Stochastic Gradien
0 views • 26 slides