Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
Understanding Computer Organization and Architecture
A computer system is a programmable digital electronics device that processes data as per program instructions to provide meaningful output. It comprises hardware and software components, with hardware being the physical parts and software essential for driving the hardware. Computer organization fo
14 views • 71 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
Decoupled SMO Architecture Overview
Develop flows showing interaction between SMO modules in the context of open-source architecture using OSC, ONAP, and other code. The objective is to align open-source work with O-RAN trends, improve synergy, reduce duplication, and provide feedback to O-RAN discussions. Related work includes Decoup
4 views • 27 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
14 views • 2 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
Overview of RF Architecture and Waveform Assumptions for NR V2X Intra-Band Operation
In the electronic meeting of 3GPP TSG-RAN-WG4, discussions were held on the RF architecture and waveform assumptions for NR V2X intra-band operation in band n79. Various options and recommendations were presented regarding RF architecture, antenna architecture, and waveform definitions for efficient
1 views • 7 slides
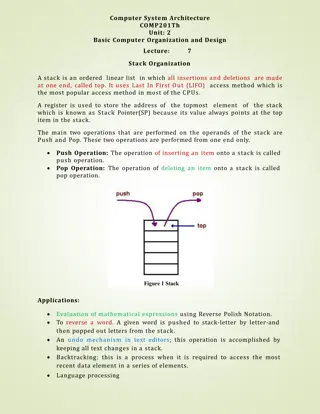
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Understanding Computer Architecture and Organization
Computer architecture and organization are fundamental aspects of computing systems. Computer architecture focuses on the functional design and implementation of various computer parts, while computer organization deals with how operational attributes come together to realize the architectural speci
3 views • 40 slides
Full Stack Skills for Digital Era Technology Architect
Specialized in full stack web & app development, with expertise in back-end technologies, cloud fundamentals, and security protocols. Proficient in programming languages like Java, NodeJS, Python, and frameworks like ReactJS and Angular. Emphasizes continuous learning, agility, and adaptability in t
2 views • 7 slides
Common Software Architecture Anti-Patterns
Anti-patterns in software architecture are commonly occurring solutions to problems that lead to negative consequences. These arise due to insufficient knowledge or experience, misuse of design patterns, and lack of attention to evolving project architecture. Examples include Jumble, Stovepipe, Spag
1 views • 7 slides
Open Source PMCI Stack Implementation for Add-In Card Manageability by Sumanth Bhat
Sumanth Bhat, a BMC Firmware Engineer at Intel, presented an initiative on open-source PMCI stack implementation for managing add-in cards. The agenda covered an overview of platform architecture with Add-In Card management, existing mechanisms, PMCI architecture overview, and external interfaces li
3 views • 18 slides
PowerPC Architecture Overview and Evolution
PowerPC is a RISC instruction set architecture developed by IBM in collaboration with Apple and Motorola in the early 1990s. It is based on IBM's POWER architecture, offering both 32-bit and 64-bit processors popular in embedded systems. The architecture emphasizes a reduced set of pipelined instruc
2 views • 13 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
Understanding Client-Server Architecture
Client-server architecture is a computing model where a central server hosts and manages resources and services for client computers over a network. There are different types of clients and servers, each with unique characteristics and roles. This architecture offers various advantages and disadvant
3 views • 15 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Digital Architecture for Supporting UNICEF's High-Impact Interventions
In an ideal scenario, the digital architecture for children would encompass systems such as Enterprise Architecture, Functional Architecture, and Solution Architecture to support UNICEF's high-impact interventions. It would involve integrated platforms for Health Information Exchange, Supply Chain M
1 views • 19 slides
Progress of Network Architecture Work in FG IMT-2020
In the Network Architecture Group led by Namseok Ko, significant progress has been made in defining the IMT-2020 architecture. The work has involved gap analysis, draft recommendations, and setting framework and requirements. Phase 1 focused on identifying 19 architectural gaps, such as demands for
1 views • 11 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Proposed Way Forward for Service-Oriented Architecture (SOA) in Space Missions
Proposed establishment of a Working Group by the CESG to develop a Service-Oriented Architecture (SOA) framework for space mission operations within the CCSDS. The focus includes identifying services, use cases, architecture definitions, and business cases to enhance CCSDS-wide interoperability and
0 views • 7 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Introduction to Y86 Instruction Set Architecture
Y86 Instruction Set Architecture is a simplified pseudo-language based on x86 (IA-32) architecture. It involves implementing the Fetch-Decode-Execute cycle, where instructions are fetched from memory, decoded, and executed. The Y86 ISA offers a simpler set of instructions and formats compared to x86
0 views • 25 slides
Enhancing Healthcare Data Sharing with Service-Oriented Architectures
This paper explores how Service-Oriented Architectures (SOA) can be integrated with the HL7 Clinical Document Architecture to facilitate the sharing of Summary Care Records between healthcare information systems. It highlights the benefits of a federated architecture based on SOA and coding standard
0 views • 51 slides
Exploring Modern Architecture Trends: Expressionism and Bauhaus Movement
Delve into the world of modern architecture trends, focusing on Expressionist architecture in Europe during the early 20th century and the influential Bauhaus movement in Germany. Expressionist architecture emphasized emotional effects through distorted forms inspired by nature, while the Bauhaus sc
0 views • 10 slides
Overview of 5G System Architecture and User Plane Functionality
This content showcases various aspects of 5G system architecture, including system handover, non-roaming architecture, service-based architecture, and user plane functionality. It delves into the control plane functions, user plane functions, and core network endpoints of the 5G network. The images
0 views • 49 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Understanding Memory Hierarchy and Different Computer Architecture Styles
Delve into the concepts of memory hierarchy, cache optimizations, RISC architecture, and other architecture styles in embedded computer architecture. Learn about Accumulator and Stack architectures, their characteristics, advantages, and example code implementations. Explore the differences between
0 views • 52 slides
Understanding Advanced Computer Architecture in Parallel Computing
Covering topics like Instruction-Set Architecture (ISA), 5-stage pipeline, and Pipelined instructions, this course delves into the intricacies of advanced computer architecture, with a focus on achieving high performance by optimizing data flow to execution units. The course provides insights into t
0 views • 12 slides
Understanding General Register Organization in Computer Architecture
In computer architecture, a common bus system is used to efficiently connect a large number of registers in the CPU. This enables communication between registers for data transfers and various microoperations. The setup includes multiple registers connected through a common bus, multiplexers for for
0 views • 40 slides