Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
Shopify Traffic Filtering Service in Europe
Utilize advanced Shopify traffic filtering service in Europe for tailored European markets, which guarantees safe and focused online traffic management. This strong solution will secure your site from harmful activity and improve its performance. It is made to comply with local data protection laws
0 views • 5 slides
Ensuring Compliance with Prevent Duty in Higher Education
Statutory guidance emphasizes the importance of integrating the Prevent duty into ICT policies in Higher Education. Key points include the need for Acceptable Use Policies (AUPs) to reference the Prevent duty, effective communication of AUPs, and the consideration of web filtering. While filtering i
1 views • 13 slides
Understanding Network Interference and Censorship in Social Media
Discover the insights into detecting network interference, censorship, and social media manipulation through a collection of case studies, research papers, and real-world examples discussed in a Spring 2018 lecture. Topics include the goals of PAM 2011 paper, the Green Dam and Blue Dam projects, the
1 views • 27 slides
Understanding Different Types of Recommender Systems
Recommender systems play a crucial role in providing personalized recommendations to users. This article delves into various types of recommender systems including Collaborative Filtering, Content-Based, Knowledge-Based, and Group Recommender Systems. Collaborative Filtering involves making predicti
0 views • 7 slides
Exploring Proteomics Data Analysis Workflows in Perseus
This content provides a detailed walkthrough of utilizing Perseus interface/functions for analyzing label-free and SILAC datasets in the field of proteomics. It covers loading, filtering, visualization, log transformation, rearrangement of columns, and advanced analysis techniques such as scatter pl
2 views • 4 slides
Collaborative Filtering in Data Mining: Techniques and Methods
Collaborative filtering is a key aspect of data mining, focusing on producing recommendations based on user-item interactions. This technique does not require external information about items or users, instead relying on patterns of ratings or usage. Two main approaches are the neighborhood method a
0 views • 23 slides
Ethics in IT-Configured Societies: Google's Controversy and Plagiarism Detection
In Chapter 3 of 'Ethics in IT-Configured Societies', various scenarios are explored such as Google's filtering practices in China and France, the ethical implications of filtering hate speech and political speech, questioning the need to know if a respondent is human or computer in instant messaging
0 views • 31 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Enhancing Email Security with DMARC: A Comprehensive Approach
Explore the vital components of DMARC, a robust spam filtering and phishing protection methodology, as presented by Ben Serebin. Discover how DMARC integrates SPF and DKIM to safeguard email authenticity and ensure a secure communication environment. Uncover the challenges, prerequisites, and implem
0 views • 13 slides
Collective Spammer Detection in Evolving Social Networks
Exploring the growth of spam in social networks, this study highlights the challenges posed by spammers and the need for collective detection mechanisms. With insights on spam trends, interaction methods, and user profiles, it sheds light on the evolving landscape of social network spam.
0 views • 65 slides
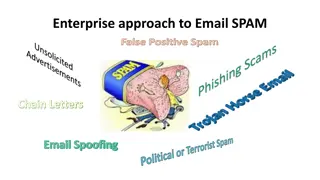
Understanding Enterprise Email Spam Prevention Techniques
Learn about the key strategies used by enterprises to combat email spam, including spam filters, SPF records, DMARC, DKIM, whitelisting, and SCL ratings. Discover how these tools work together to protect against spam, spoofing, and phishing attempts.
0 views • 8 slides
Understanding Text Classification in Information Retrieval
This content delves into the concept of text classification in information retrieval, focusing on training classifiers to categorize documents into predefined classes. It discusses the formal definitions, training processes, application testing, topic classification, and provides examples of text cl
0 views • 57 slides
Analysis of Spam Activity on Popular Social Networks
This research paper presents an in-depth analysis of spam activity on major social networking platforms such as Facebook, MySpace, and Twitter. The study includes data collection, analysis of spam bots, identification of spam campaigns, and analysis of results. It reveals insights into user behavior
2 views • 38 slides
Personalized Spam Filtering for Gray Mail Analysis
This work delves into the concept of gray mail - messages that some users want while others don't. It explores the challenges posed by gray mail and presents a large-scale personalization algorithm to address these issues. The study leverages data from Hotmail Feedback Loop, focusing on user prefere
3 views • 22 slides
Adversarial Learning in ML: Combatting Internet Abuse & Spam
Explore the realm of adversarial learning in ML through combating internet abuse and spam. Delve into the motivations of abusers, closed-loop approaches, risks of training on test data, and tactics used by spammers. Understand the challenges and strategies involved in filtering out malicious content
0 views • 13 slides
Distance-Based Suspicion Score for Audit Selection
Nuriddin Tojiboyev presented a method for audit selection based on distance measures, risk filtering, and exception sorting. The approach involves selecting representative samples from a population of records, using risk-based filtering to prioritize records for review. Various filters and exception
0 views • 19 slides
Understanding BGP Protocol and Configuration for Routing Policy Filtering
Explore the terminology, reasons, and methods behind routing policy filtering in the context of BGP protocol configuration. Learn how to control traffic routing preferences, filter routes based on AS or prefix, and use regular expressions for complex filtering rules. Discover the importance of AS-Pa
0 views • 29 slides
Understanding Enterprise Network Security and Firewalls
Exploring key aspects of enterprise network security, this presentation delves into topics such as perimeter control, host-based security, intrusion detection, and various types of firewalls. It highlights filtering rulesets, requirements for outbound traffic, and the importance of dynamic packet fi
0 views • 19 slides
High-Resolution 3D Seafloor Topography Enhancement Using Kalman Filtering
Proposing a Kalman Filter approach to refine seafloor topography estimation by integrating various geophysical data types. The method allows for producing regional bathymetry with higher resolution, truncating unnecessary observations, and reducing the matrix dimensions in the inverse problem. Inclu
0 views • 9 slides
Understanding Shuttling and Filtering of Multiple Ion Species in Segmented Linear Trap
This content delves into the intricate processes of shuttling and filtering multiple ion species within a segmented linear trap. It explores techniques such as RF filtering, DC potentials, mass filtering, and trap depths in the context of ion manipulation. Discussions also touch on ion crystal phase
0 views • 13 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Collaborative Bayesian Filtering in Online Recommendation Systems
COBAFI: COLLABORATIVE BAYESIAN FILTERING is a model developed by Alex Beutel and collaborators to predict user preferences in online recommendation systems. The model aims to fit user ratings data, understand user behavior, and detect spam. It utilizes Bayesian probabilistic matrix factorization and
0 views • 49 slides
Fast High-Dimensional Filtering and Inference in Fully-Connected CRF
This work discusses fast high-dimensional filtering techniques in Fully-Connected Conditional Random Fields (CRF) through methods like Gaussian filtering, bilateral filtering, and the use of permutohedral lattice. It explores efficient inference in CRFs with Gaussian edge potentials and accelerated
0 views • 25 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides
Understanding Mixtures and Separation Methods
A mixture is a combination of ingredients that can be separated by various methods like sieving, filtering, and evaporation. Magnets are also used to separate magnetic objects. Sieving separates solid particles by size, while filtering separates tiny particles from liquids. Evaporation is used for s
0 views • 14 slides
Understanding Classification in Data Mining
Classification in data mining involves assigning objects to predefined classes based on a training dataset with known class memberships. It is a supervised learning task where a model is learned to map attribute sets to class labels for accurate classification of unseen data. The process involves tr
0 views • 26 slides
Insights from Mars and Earth for Predictability with Ensemble Kalman Filtering
A collaborative effort between Penn State University and various teams explores the predictability of Martian and Earth weather phenomena using ensemble Kalman filtering. A comparison of key characteristics between Earth and Mars is provided, shedding light on their variable atmospheres and climates
0 views • 31 slides
Email Best Practices for Postfix and Dovecot Setup
In this guide, Kevin Chege discusses best practices for configuring email servers with Postfix and Dovecot. Topics covered include setting up SPF records, reverse records, using anti-spam and anti-virus software, implementing greylisting, and ensuring well-formatted messages to reduce spam. Learn ho
0 views • 38 slides
Determining Email Spam using Statistical Analysis and Machine Learning
The discussion revolves around classifying spam from ham emails by analyzing word frequencies. Various techniques such as Logistic Regression, Linear Discriminant Analysis, and 10-fold Cross-Validation are employed to achieve this goal. Statistical analysis and machine learning models like LDA and L
0 views • 8 slides
Real-Time Digital Signal Processing Lab: Matched Filtering and Digital Pulse Amplitude Modulation
Explore the concepts of transmitting one bit at a time, matched filtering, PAM systems, intersymbol interference, communication performance, and prevention of intersymbol interference in a two-level digital PAM system. The presentation covers topics like bit error probability, symbol error probabili
0 views • 32 slides
Passive DNS And The Halting Problem by Joe St. Sauver, Ph.D.
Exploring the interplay between Passive DNS and the Halting Problem, this document presents insights shared by Dr. Joe St. Sauver at B|Sides Vancouver, BC in March 2015. The detailed presentation covers various aspects such as the dynamic format of the session, unique slide style, author's backgroun
0 views • 84 slides
Tutorial Webinar #19: Ion Mobility Spectrum Filtering in Skyline
Welcome to Tutorial Webinar #19 focusing on Ion Mobility Spectrum Filtering in Skyline software. Join experts Brendan MacLean, Erin Baker, and Nat Brace to enhance your understanding and usage of Skyline for mass spectrometry. Learn about agenda, upcoming events, and how to submit questions. Don't m
0 views • 8 slides
Understanding Finite Impulse Response Filtering in Digital Signal Processing
Explore the concepts of Finite Impulse Response (FIR) filtering in digital signal processing, including filter specifications for low-pass, high-pass, band-pass, and band-stop filters. Learn about frequency normalization, specifications for different filter types, and the transfer function of FIR fi
0 views • 26 slides
Decontamination and Reuse of N95 Filtering Facepiece Respirators
This presentation discusses the decontamination and reuse of N95 filtering facepiece respirators, addressing the need for solutions in sanitizing technologies like ultraviolet light and chlorine dioxide. Various methods under consideration, such as heat and hydrogen peroxide, are explored alongside
0 views • 16 slides
Overview of the Urinary System: Functions, Structure, and Importance
The urinary system plays a crucial role in maintaining water and salt balance, regulating pH levels, and excreting waste products like urea and uric acid. Comprising of organs such as the kidneys, ureters, urinary bladder, and urethra, this system ensures the removal of metabolic waste from the body
0 views • 34 slides
Updates on ABS and Anti-Spam Efforts in Japan
The content discusses the challenges faced by the ABS committee, the need for new members due to changing dynamics, and the apology for lack of communication. It also highlights significant changes in Japan regarding Anti-Spam regulations, forming an Anti-Spam council to combat abuse. The post empha
0 views • 5 slides
Introduction to NLMS Adaptive Filtering in Matlab
Explore NLMS adaptive filtering, a powerful method for signal processing applications, particularly in acoustic echo cancellation. Learn about the NLMS algorithm, its comparison with the LMS algorithm, and the key parameters involved in tuning for optimal performance. Dive into practical experiments
0 views • 9 slides
Creating Custom Time Frame Formulas for Reporting and Filtering
Learn how to create custom formula fields to calculate time periods such as calendar years, fiscal years, quarters, months, weeks, and days for reporting and filtering purposes. Understand offset calculations to determine the date's proximity to the current time period and implement to-date calculat
0 views • 19 slides
Exploring the Power of Filtering in Signal Processing
Delve into the world of signal processing and filtering as a means of separating desired information from noise. Explore the role of digital filters in processing images and signals. Discover how filtering can achieve noise cancellation in headphones, clean up noisy images, and understand the import
0 views • 29 slides