Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
2 views • 10 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Understanding Software Engineering: Concepts and Characteristics
Software engineering involves the application of scientific principles and methods to develop efficient, reliable software products. The need for software engineering arises due to factors like large software size, scalability, cost concerns, dynamic nature, and quality management. Good software exh
3 views • 25 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Integrated Vulnerability Assessment and Human Security for Sustainable Livelihoods in the Solomon Islands
The approach to the Solomon Islands Integrated Vulnerability Assessment (SIIVA) and the Integrated Vulnerability and Adaptation Assessment (IVA) are key methodologies to assess climate change risks and prepare nations for adaptation. The objectives include informing national climate change policies,
0 views • 21 slides
Understanding Software Processes and Models
This lecture discusses software processes, models, and activities involved in requirements engineering, software development, testing, and evolution. It covers topics such as process models, computer-aided software engineering (CASE) technology, software specification, design, validation, and evolut
2 views • 25 slides
Economic Vulnerability Premium for SIDS - Webinar Insights
Presentation outlines applying Economic Vulnerability Index (EVI) for an Economic Vulnerability Premium in Small Island Developing States (SIDS) during ADF 13 cycle. Details ADF grants availability, grant allocation framework, performance-based allocation system, and modifications needed for SIDS.
0 views • 14 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Understanding Software Measurement and Metrics in Software Engineering
Software measurement plays a crucial role in assessing the size, quantity, and quality of software products and processes. It involves direct and indirect measurement methods to monitor and improve software quality, predict future outcomes, and manage project budgets and schedules. Software metrics
0 views • 8 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
Software Cost Estimation in Software Engineering
Software cost estimation in software engineering involves predicting the resources required for a software development process. It includes fundamental estimation questions, software cost components, costing and pricing considerations, software pricing factors, and programmer productivity assessment
0 views • 30 slides
ATST Safety Review High-Level Software Overview
This document provides an overview of the high-level software components involved in the ATST Safety Review conducted on 26th January 2011. It includes details on the Telescope Software Control Systems, Observatory Software Control Systems, and Instrument Software Control Systems, along with respons
13 views • 15 slides
Understanding Vulnerability and Capacity Issues in Civil Courts
Exploring vulnerability and capacity issues in civil courts, this content delves into the importance of addressing vulnerabilities of parties and witnesses for ensuring fair participation and quality evidence in legal proceedings. Topics covered include factors contributing to vulnerability, the rol
0 views • 21 slides
Understanding Software Engineering: An Overview by Lecturer Sebastian Coope
Explore the world of software engineering with Lecturer Sebastian Coope in this informative module introduction. Discover the importance of structured and disciplined approaches in making software, the challenges in software development, and the necessity of software engineering in handling complex
5 views • 37 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
1 views • 34 slides
Reimagining Vulnerability: Rethinking the Body and Human Dignity
The notion of vulnerability is explored within the framework of the human body and dignity, challenging traditional concepts of autonomy and independence. Scholars like Martha Nussbaum and Fineman provide insights on the universal nature of vulnerability and advocate for a shift towards recognizing
0 views • 21 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Understanding Risks and Vulnerability in Risk Assessment
This module focuses on understanding risks, vulnerability, and conducting risk assessments in disaster risk management. It covers terminologies such as threats, hazards, vulnerability, and exposure, essential for prioritizing risks and initiating risk reduction measures.
0 views • 24 slides
Insights from NATO Software Engineering Conferences and The Software Crisis of the Seventies
Exploring the challenges faced in software engineering during the 1970s, including issues such as project delays, inefficiencies, and the critical need for reliable, high-quality software. Insights from the NATO Software Engineering Conferences shed light on the struggle to meet increasing modern so
0 views • 46 slides
Gamifying Vulnerability Reporting for Coordinated Disclosure at Microsoft Security Response Center
Christa Anderson, a Senior Security Program Manager at Microsoft's Security Response Center, discusses the importance of gamifying vulnerability report data to encourage coordinated disclosure. The MSRC Top 100, announced at Black Hat USA, plays a crucial role in the public credit strategy by recogn
0 views • 13 slides
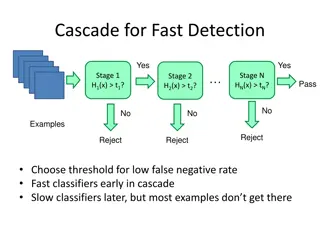
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Rootkit Detection with RAI - Practical Challenges and Solutions
Practical Rootkit Detection with RAI by Christoph Csallner explores the challenges in malware detection, such as slow signature-based deployments and untrustworthy legacy platforms. The threat model presented illustrates how adversaries can manipulate binaries and gain root access. RAI offers a solu
0 views • 14 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Software Bingo_ A Game-Changing Addition to Your Online Casino
Discover how software bingo, bingo game software, professional bingo software, software for bingo, pc bingo games software can enhance your online casino and boost player engagement.\n\nSource>>\/\/ \/bingo-software\n\n
1 views • 4 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
Understanding the Essence of Software Development Process
Software is a vital component in today's technology-driven world. It consists of instructions, data structures, and descriptive information that enable the functioning of computer programs. Unlike hardware manufacturing, software development is an engineering process that undergoes changes and deter
0 views • 74 slides
Understanding Software Engineering Fundamentals
Explore the significance of software in modern economies, the attributes of good software, software engineering principles, software processes, and process models. Learn how software engineers ensure functionality, maintainability, dependability, efficiency, and usability in software development.
0 views • 25 slides
Understanding Software Engineering and Development Processes
Explore the key concepts of software engineering, including misconceptions, legacy software, and development phases. Learn about professional responsibilities, the need for software processes, the ETVX model, and different properties of software processes. Discover the components of software process
1 views • 57 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides