Lecture- 5. Extension systems in India
Explore the evolution and impact of agricultural extension systems in India, including initiatives like the National Agricultural Technology Project (NATP), Agriculture Technology Management Agency (ATMA), and the National Mission on Agriculture Extension and Technology (NMAET). These programs aim t
0 views • 10 slides
Maximizing Learning Efficiency with Technology
Explore how to effectively utilize technology for learning and revision, avoiding distractions and harnessing tools like GCSE Pod for digital organization. Discover the benefits and drawbacks of technology use, tips for optimizing built-in device features, time management strategies, and platforms l
1 views • 19 slides
NIGERIA/CHINA JUNCAO TECHNOLOGY CENTER
The Nigeria-China Juncao Technology Center explores the applications of Juncao technology and its contribution to achieving sustainable agriculture and the Sustainable Development Goals in Africa. Despite Nigeria's significant agricultural sector, challenges persist such as a widening agricultural t
0 views • 17 slides
Department of Education, Science, Technology, and Innovation - Overview and Priorities
The Department of Education, Science, Technology, and Innovation (ESTI) under the African Union Commission focuses on developing policies and programs for the growth and development of Africa. With a mandate to align with AU Agenda 2063 and global sustainable development goals, ESTI emphasizes educa
3 views • 13 slides
Intellectual Property Rights and Technology Business Management Courses
Explore post-graduate and certificate courses on Intellectual Property Rights and Technology Business Management offered by renowned professors and industry experts. Learn about patents, technology transfer, creativity, and innovation. Various pricing options available for corporate, students, facul
1 views • 7 slides
Exploring CBDC Technology at the Forum - July 26, 2023
Delve into the world of Central Bank Digital Currency (CBDC) technology through discussions, agenda items, and next steps outlined during the CBDC Technology Forum held on July 26, 2023. The event highlighted key areas such as design phase intentions, new member introductions, sub-group workings, an
2 views • 17 slides
San Diego Police Department Smart Streetlights Technology Update
San Diego Police Department initiated a Smart Streetlights technology upgrade in 2016 but faced concerns leading to a project suspension. The project included sensors and data collection for public use. The proposed technology refresh aligns with Surveillance Ordinance guidelines, integrating video
2 views • 18 slides
NASA Space Technology Research Grants Program Overview
The NASA Space Technology Research Grants Program, managed by Dr. Matt Deans, encompasses various initiatives such as Early Stage Innovation, Technology Maturation, and Technology Demonstration. It aims to support innovative research and partnerships in space technology, fostering collaboration with
14 views • 9 slides
Travel Technology Solution
Travelopro is an advanced travel technology company delivering complete end-to-end travel technology solutions and online travel ERP for travel businesses to compete in the ever-evolving digital world. Our travel technology solutions are developed to manage client business achievement and prosperity
2 views • 13 slides
Enhancing Lives with Assistive Technology
Assistive Technology empowers individuals with disabilities by providing tools and solutions for mobility, communication, and daily tasks. This technology, defined as items or systems that improve functional capabilities, helps redefine disability, increase resilience, and enable individuals to enga
1 views • 27 slides
Exploring the Impact of Technology on Culture and Behavior
Dive into how technology is shaping our culture and behavior through the absorption of technology into our daily lives. Explore the intertwining relationship between technology and culture with examples of how we interact with technology and its effects on our routines and social connections.
0 views • 18 slides
Technology Assurance Sandbox: Promoting Innovation and Assurances
The Malta Digital Innovation Authority offers a Technology Assurance Sandbox for technology developers. This sandbox aims to provide a safe environment for innovative technology solutions and align them with international standards. Certification is voluntary and ensures quality, user, and investor
0 views • 12 slides
Legal Overview and Powers of MDIA for Innovative Technology Arrangements
This legal overview delves into the powers of Malta Digital Innovation Authority (MDIA) to roll out Technology Arrangements and Innovative Technology services, ensuring legal compliance, drafting guidelines, and covering all forms of innovative technology. The objective is to clean out inconsistenci
0 views • 11 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Technology Considerations for Remote and Virtual Hearings Implementation
This content discusses the technology considerations for implementing remote and virtual hearings in courtrooms. It covers aspects such as courtroom technology framework, technology considerations matrix, and AV devices placement and requirements. The framework includes acoustic treatments, audio/vi
0 views • 7 slides
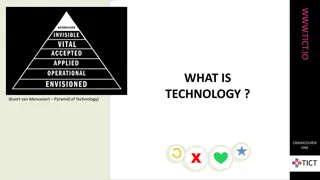
Exploring the Impact of Technology on Society Through Various Perspectives
Delve into the complex relationship between technology and humanity as discussed by experts like Koert van Mensvoort and Rens van der Vorst in the CrashCourse series on www.tict.io. Explore how technology shapes civilization, ethics, and the world, raising questions on whether it truly makes the wor
0 views • 9 slides
Understanding Core Concepts of Technology Unit 2
Explore the core concepts of technology, the relationship among technologies, and their connection to other fields of study. Delve into the impact of various technologies like medical, agricultural, and information technology. Understand the designed world created by human modifications to meet need
0 views • 18 slides
Understanding Assistive Technology and Technology-Enabled Care Services
This content highlights the role of Assistive Technology (AT) and Technology-Enabled Care Services (TECS) in supporting individuals, particularly those with dementia and falls. It discusses the importance of AT, the history of AT implementation in NYCC, and how Technology-Enabled Care can aid in add
0 views • 13 slides
The Excitement of Technology Plan Update and Professional Development Goals
The technology plan update involves optimizing technology use at the College through professional development resources. Various goals and objectives are outlined for 2014-2015, including enhancing training opportunities for faculty and staff, assessing technology training needs, and establishing a
0 views • 9 slides
Qualcomm: A Leading Innovator in Mobile Technology
Qualcomm, a pioneer in mobile technology, has a rich history of innovations in CDMA technology and chipset development. From founding in 1985 to present success with Snapdragon processors, Qualcomm's key to success lies in powerful mobile chipsets and CDMA technology. Explore Qualcomm's journey from
0 views • 11 slides
Understanding Snort: A Comprehensive Overview
Snort is an open-source network intrusion detection system (NIDS) widely utilized in the industry. It employs a rule-based language combining various inspection methods to detect malicious activities like denial of service attacks and port scans. The components, architecture, and detection engine of
0 views • 25 slides
Mastering Intrusion Detection with Snort: A Comprehensive Guide
Dive into the world of network security with Snort, the powerful intrusion detection system. Learn how to analyze network traffic in real time, create custom configuration files, and defend against zero-day attacks. Explore Snort's versatility, portability, and configurability, and discover advanced
0 views • 5 slides
Enhancing Network Security with Software-Defined Snort and OpenFlow
Explore the implementation of Snort, Barnyard, and PulledPork within a Software-Defined Network framework using OpenFlow technology. Learn how these tools enhance network security through intrusion detection engines, rule management, and network traffic control mechanisms. Dive into the architecture
0 views • 15 slides
Understanding IDS and IPS for Network Security
Enhance the security of your network with IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) by monitoring traffic, inspecting data packets, and detecting malicious activities based on known signatures. Learn about different types like HIDS and NIDS, their functions, and tools us
0 views • 7 slides
Enhancing Network Security Using Snort Virtual Network Function with DPI Service
Deep Packet Inspection (DPI) as a service is explored in this work, aiming to improve performance, innovation, and security in network operations. By extracting DPI from middleboxes and offering it as a shared service, the paper suggests benefits such as optimized packet scanning, enhanced functiona
0 views • 55 slides
Malware Dynamic Analysis Part 6 Overview
This content provides insights into Malware Dynamic Analysis Part 6 by Veronica Kovah. It covers actionable outputs like Yara and Snort, utilizing the open-source tool Yara to identify and classify malicious files based on patterns. The Yara signatures discussed include rules, identifiers, and condi
0 views • 25 slides
Hands-On Snort Testing and Rule Creation for Infrastructure Security
Dive into the world of Snort, a powerful intrusion detection system, through a practical course project in infrastructure security. This project, part of SEC290 Fundamentals of Infrastructure Security, focuses on testing Snort rules by capturing XMAS and TCP packets, as well as creating rules to det
0 views • 6 slides
Comprehensive Guide to Traffic Analysis Using Snort and Tcpdump
This detailed guide provides step-by-step instructions on traffic analysis using Snort and Tcpdump tools. It covers topics such as installing Android Studio, copying Tcpdump files to rooted devices, rooting your device, setting up the server IP address, and running server and client codes for analys
0 views • 7 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Deciphering Combinatorial Games Through Mathematical Analysis
Discover the intricacies of combinatorial games by analyzing strategies for winning and understanding the dynamics of distance games on graphs. Learn about known distance games like COL, SNORT, and NODEKAYLES, and explore techniques such as strategy stealing and mirroring to determine optimal gamepl
0 views • 22 slides
Network Monitoring Workshop - Incident Response Overview
This workshop covers various aspects of incident response, including tools and techniques such as network taps, protocol analysis with Wireshark, data summarization with Bro/Zeek, alerting with Snort/Suricata, and more. Sessions delve into topics like TLS inspection, wireless network monitoring, and
0 views • 17 slides
Exploring the i-VISA Model for Technology Leadership in Smarter School Development
Dr. Chang, I-Hua, Chairperson of Taiwan Technology Leadership and Instructional Technology Development Association, introduces the i-VISA Model, consisting of Interpersonal and communication skills, Vision, planning and management, Infrastructure and technology support, Staff development and trainin
0 views • 27 slides
Impact of Technology on Health - Lecture Insights
Technology has a significant impact on our health, with some repercussions being negative. This lecture discusses various health issues related to technology, including psychological disorders, physical health concerns, distractions caused by digital devices, instant gratification expectations, narc
0 views • 16 slides
Navigating Technology in Counselling: A Professional Perspective
Embracing technology in counseling is not just inevitable but essential for growth. This article by Dr. Paul A. Jerry explores the integration of technology in professional practices, mapping reactions through established theories, and addressing ethical considerations. It emphasizes the need for co
0 views • 12 slides
Spring 2022 District Test and Technology Coordinator Training Overview
Explore the comprehensive training materials for the Spring 2022 District Test and Technology Coordinator Training, covering technology setup, system requirements, changes to technology bulletins, and detailed insights into TestNav for the 2021-2022 school year. Get ready to identify testing devices
0 views • 74 slides
Understanding Factors Influencing Dairy Farmers' Grass Measuring Technology Adoption
This study examines why dairy farmers who initially embraced grass measuring technology later discontinued its use. Through interviews and focus groups, reasons for discontinuation are compared with those who continue to use the technology. Recommendations include providing more support and resource
0 views • 9 slides
Educational Technology at IIT Bombay: Enhancing Thinking Skills
Technology Enhanced Learning of Thinking Skills (TELoTS) is a joint initiative at the Indian Institute of Technology Bombay focusing on innovative educational strategies, including peer discussions, adaptive tutoring systems, virtual reality, and analytics. The program emphasizes research, consultan
0 views • 28 slides
Technology Industry Collaboration Initiative: A Suggestive Model for San Jose State University
This initiative led by Prof. Samuel C. Obi and Dr. Fatemeh Davoudi aims to explore opportunities in Silicon Valley manufacturing and computer/electronics industries to support San Jose State University's Industrial Technology programs. The study focuses on maintaining collaborative relationships wit
0 views • 6 slides
Explore Assistive Technology for Enhanced Learning and Living
Assistive technology encompasses innovative tools that greatly benefit individuals with disabilities in various aspects of life. From enhancing learning to managing tasks and promoting wellness, assistive technology plays a vital role in improving the quality of life for people with disabilities. Di
0 views • 17 slides
SWOSU Technology Optimization Plan
This plan outlines strategic initiatives aimed at optimizing technology to meet the educational and administrative needs of SWOSU. Key focus areas include upgrading identified computers, enhancing technology staffing and support, improving data mining and learning analytics, ensuring satisfaction wi
0 views • 15 slides