H3C GB0-601 Exam Preparation: What You Need to Know
Begin your preparation journey here--- https:\/\/bit.ly\/4c6E4N5 \ud83d\ude80. Access all the essential details to ace the H3C Certified Network Engineer for Server (H3CNE-Server) exam. Gather all the necessary information, including tutorials, practice tests, books, study materials, exam questions,
5 views • 19 slides
Dominate SK0-005 Ace CompTIA Server Certification Exam
Elevate your IT career with the SK0-005 CompTIA Server Certification Exam. Master server administration and earn industry recognition for your expertise.\n\/\/ \/pdf\/SK0-005\/
0 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
DeepMainMast Tutorial: Protein Structure Modeling on Web Server and Google Colab
Explore DeepMainMast for protein structure modeling on web servers like EM Server, Google Colab, or through source code. Gain insights into computational time limits, hardware parameters, model availability, installation process, and integrated protocols. Register on the web server for access and ut
4 views • 14 slides
Resolving the “QuickBooks Unable to Connect to Remote Server” Issue
Resolving the \u201cQuickBooks Unable to Connect to Remote Server\u201d Issue\n\nStruggling with the \"QuickBooks Unable to Connect to Remote Server\" issue can disrupt your workflow. However, resolving this problem is crucial to ensure seamless access to your financial data. To tackle this issue ef
1 views • 4 slides
What's the Best Server for My Small Business?
Need the best server for your small business? VRS Technologies LLC offers top-notch Server Rental in Dubai. Call 0555182748 today.\n\nVisit: \/\/ \/computer-rentals\/reliable-server-maintenance-and-rental-in-dubai\/
2 views • 2 slides
What to Do When QuickBooks POS Client Cannot Connect to Server_ A Comprehensive Guide
Struggling with QuickBooks POS client connectivity issues? Our comprehensive guide offers detailed steps to resolve problems when QuickBooks POS client cannot connect to the server. Learn how to check network connections, configure firewall settings, and verify server configurations to restore seaml
1 views • 3 slides
430548-001 HPE NC373m PCI-E Dual Port Multifunction Gigabit Server Adapter
New | HPE 430548-001 | NC373m PCI-E Dual Port Multifunction Gigabit Server Adapter | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\nProduct Link: \/\/ \/430548-001-hpe-nc373m-pci-e-dual-port-multifunction-gigabit-server-adapter\/
0 views • 1 slides
HPE 662530-001 Proliant DL380P Gen8 and Gen9 Server Motherboard
Refurbished | HPE 662530-001 | Proliant DL380P Gen8 and Gen9 Server Motherboard | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\nProduct Link: \/\/ \/hpe-662530-001-proliant-dl380p-gen8-and-gen9-server-motherboard\/
0 views • 1 slides
What’s the Right Server Choice for a Small Business?
Ensure your small business runs smoothly with the right server choice from VRS Technologies LLC. Our Server Rental Dubai services offer flexible and cost-effective solutions tailored to your specific requirements. Reach out to us at 0555182748.
1 views • 7 slides
How Can Flexible Server Rentals Meet All Your Requirements?
Find out how flexible server rentals can support your business requirements. Download the guide from VRS Technologies LLC. Reach out to us at 0555182748 for expert Server Rental Dubai solutions.
1 views • 2 slides
868704-B21 HPE DL380 GEN10 24 BAY SFF CTO SERVER CHASSIS
Refurbished | HPE 868704-B21 | DL380 GEN10 24 BAY SFF CTO SERVER CHASSIS | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\n\/\/ \/868704-b21-hpe-dl380-gen10-24-bay-sff-cto-server-chassis\/
0 views • 1 slides
Guide to MySQL Operations on Turing Server
This guide provides step-by-step instructions on working with MySQL on Turing server at turing.csce.uark.edu. It includes logging in via SSH, connecting to the server, changing MySQL passwords, and performing operations on tables. Learn how to create tables, change passwords, and more with detailed
2 views • 21 slides
Issues and Algorithms in Server Software Design
The content discusses fundamental issues in server software design such as connectionless vs. connection-oriented access, stateless vs. stateful applications, and iterative vs. concurrent server implementations. Various server algorithms like iterative and concurrent servers are explained with their
2 views • 44 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Understanding Client-Server Architecture
Client-server architecture is a computing model where a central server hosts and manages resources and services for client computers over a network. There are different types of clients and servers, each with unique characteristics and roles. This architecture offers various advantages and disadvant
3 views • 15 slides
Networked Server Verification Using Interaction Trees
This paper explores the process of specifying, testing, and verifying a networked server from C to interaction trees. It discusses the main contributions, including verifying a networked C program using VST and running in CertiKOS. The paper also delves into swap server specifications, observable be
0 views • 19 slides
How Can You Avoid Server Downtime with Server Rentals?
Server downtime can be costly, but in this PPT we explain the steps to avoid these risks. Our Server Rental Dubai services include top-quality servers and ongoing maintenance to keep your systems running smoothly. Contact VRS Technologies LLC today a
5 views • 2 slides
A Comprehensive Guide to Dedicated Server Hosting
Dedicated server hosting is the pinnacle of web hosting solutions, offering unmatched performance, security, and control. This guide will help you understand the fundamentals of dedicated server hosting, explore its advantages, and provide insights o
0 views • 7 slides
Why Linux is the Best Choice for Dedicated Server Hosting
Why Linux is the Best Choice for Dedicated Server Hosting\nWhen it comes to dedicated server hosting, choosing the right operating system is crucial for performance, security, and scalability. Among the available options, Linux stands out as the pref
0 views • 10 slides
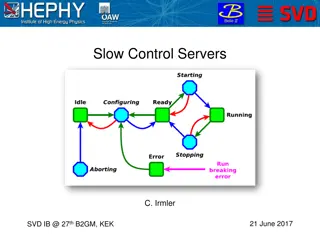
Slow Control Servers and Network Configuration for SVD Management
The documentation discusses the setup and requirements for slow control servers, network configuration, FADC server status, ENV server status, and general SC server status for SVD management. It outlines the need for backup servers, minimum server requirements, server specifications, procurement det
0 views • 11 slides
Understanding Modern Performance in SQL Server
Explore the evolution of performance in SQL Server with insights from Joe Chang, a seasoned SQL Server consultant. Delve into topics like query optimization, execution plans, CPU and memory advancements, storage technologies, and the significance of performance in today's data environment. Discover
0 views • 40 slides
Server-Side Technologies and Security Vulnerabilities in Mobile Services
This content delves into server-side technologies such as SQL, SOAP, JSON, and ReST used in mobile services, highlighting vulnerabilities that expose sensitive data. It emphasizes the importance of general web service security guidelines and discusses attacks against XML-based web services, outlinin
0 views • 52 slides
DSpace Installation Requirements and Steps by Francesco Bergamaschi
DSPACEDSPACE INSTALLATION INSTALLATION Requirements People Network Hardware Software and TIME! Francesco Bergamaschi U.O. Management Control Universit di Parma. The installation process involves installing the server operating system, preparing the server with prerequisite software for DSpace, and f
0 views • 8 slides
Enhancing Server State Detection in OpenStack for Immediate Host Fault Reporting
This blueprint proposes the development of a new API in Nova to promptly update the server state in OpenStack when a host fault occurs. The intention is to ensure reliability and real-time updates of server and host states for Telco-grade VIM, allowing users to take necessary actions swiftly in case
0 views • 5 slides
Understanding ASP.NET Server Controls and Their Importance
ASP.NET server controls play a crucial role in web development by allowing developers to create dynamic and interactive elements on a web page. These controls provide a way to encapsulate functionality, manage UI elements, and handle events efficiently on the server side. Learn about different types
0 views • 43 slides
Understanding Client-Server Communication with Flask in Python
Explore the basics of implementing a client-server architecture using Flask in Python. Learn how to set up a server, create APIs, and interact with a client application. The process involves handling API calls, directing requests, and returning data to the client through the server.
0 views • 10 slides
Understanding Client-Server Paradigm in Distributed Systems
Client-server paradigm in distributed systems involves structuring systems as collaborating processes where clients request services from servers. The model follows a request/reply protocol, with servers providing centralized control of shared resources. Advantages include security and simplicity, w
1 views • 30 slides
Memory Resource Management in VMware ESX Server Overview
This presentation discusses the background of memory resource management in VMware ESX Server, focusing on server consolidation, memory abstractions, and memory reclamation techniques. It covers topics such as page sharing, memory allocation policies, and related work in the field. The use of VMware
0 views • 26 slides
Networking Solutions for Server Virtualization Challenges
This presentation discusses the challenges server virtualization technologies bring to data center networks. It demonstrates a standards-based approach to enhance the experience and economics in a virtualized environment. Topics include market drivers, limitations of legacy networks, simplification
0 views • 33 slides
Building a Secure Access & SQL Server Solution with Anders Ebro
Anders Ebro, a Principal consultant with Exacto A/S, shares insights on building a secure access and SQL server solution. With a background in SQL development and experience in managing sensitive data, Anders emphasizes the importance of security aspects such as limiting access to sensitive data, ro
0 views • 20 slides
Insight into Azure Server Subscriptions for CSP - September 2018
Explore the nuances of Server Subscriptions for Azure in CSP, including options for Windows Server and SQL Server virtual machines, Azure Hybrid Benefit, Reserved Instances, and more. Discover how customers can optimize prices based on workload types and licensing scenarios, all outlined in a compre
0 views • 37 slides
Optimal Power Allocation in Server Farms: A Study on Efficiency and Performance
This research study delves into the optimal allocation of power in server farms to enhance performance and efficiency. It explores the impact of power on server speed, response time, and workload distribution. The results aim to provide insights on minimizing mean response time and improving overall
0 views • 24 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Understanding DFS in Dyalog File Server
DFS (Dyalog File Server) is a client/server system that replaces direct access to component files. It offers features like monitoring, backup, and user authentication. DFS enhances security and performance compared to traditional file access methods like DCF. Learn about its architecture, features,
0 views • 35 slides
Stepping Stone Detection at the Server Side: Real-Time Algorithm
An innovative real-time algorithm is introduced to detect the use of a proxy as a stepping stone from the server's perspective. The solution addresses the limitations of existing methods by focusing on TCP connection initiation. Previous research and vulnerabilities related to proxy servers and step
0 views • 37 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Private Information Retrieval in Large-Scale Data Repositories
Private Information Retrieval (PIR) is a protocol that allows clients to retrieve data privately without revealing the query or returned data to the server or anyone spying on the network. Encrypting data on the server is not a solution due to security concerns related to server ownership. This adva
0 views • 31 slides
Exploring High IOPS Applications and Server Configurations
Dive into the world of high IOPS applications, memory buffer configurations, and file server setups with a series of detailed images showcasing various server environments and code memory management. Discover the importance of optimizing IOPS for efficient data processing and explore advanced server
0 views • 16 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides