Language Teaching Techniques: GTM, Direct Method & Audio-Lingual Method
Explore the Grammar-Translation Method, Direct Method, and Audio-Lingual Method in language teaching. Understand principles, objectives, and methodologies with insights into language learning approaches. Enhance teaching skills and foster effective communication in language education.
3 views • 82 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
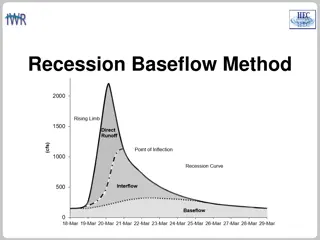
Understanding the Recession Baseflow Method in Hydrology
Recession Baseflow Method is a technique used in hydrology to model hydrographs' recession curve. This method involves parameters like Initial Discharge, Recession Constant, and Threshold for baseflow. By analyzing different recession constants and threshold types such as Ratio to Peak, one can effe
0 views • 8 slides
Understanding the Scientific Method: A Logical Framework for Problem-Solving
The Scientific Method is a systematic approach used to solve problems and seek answers in a logical step-by-step manner. By following key steps such as stating the problem, researching, forming a hypothesis, testing, analyzing data, and drawing conclusions, this method helps clarify uncertainties an
1 views • 18 slides
Introduction to Six Thinking Hats Method for Effective Group Decision Making
Explore the Six Thinking Hats method, a powerful tool for facilitating group discussions and decision-making processes. This method encourages participants to approach problems from various perspectives represented by different colored 'hats'. By simplifying thinking and fostering constructive dialo
1 views • 24 slides
Understanding Corn Growth Stages: Leaf Staging Methods and Considerations
Various leaf staging methods, including the Leaf Collar Method and Droopy Leaf Method, are used to identify corn plant growth stages. The Leaf Collar Method involves counting leaves with visible collars, while the Droopy Leaf Method considers leaves at least 40-50% exposed from the whorl. Factors li
0 views • 9 slides
Understanding Different Emasculation Techniques in Plant Breeding
Learn about the significance of emasculation in plant breeding to prevent self-pollination and facilitate controlled pollination. Explore various methods such as hand emasculation, forced open method, clipping method, emasculation with hot/cold water, alcohol, suction method, chemical emasculation,
2 views • 10 slides
Simple Average Method in Cost Accounting
Simple Average Method, introduced by M. Vijayasekaram, is a technique used for inventory valuation and delivery cost calculation. It involves calculating the average unit cost by multiplying the total unit costs with the number of receiving instances. This method simplifies calculations and reduces
2 views • 5 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
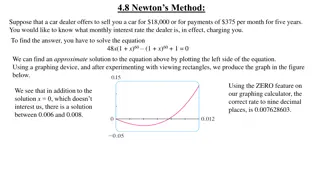
Understanding Newton's Method for Solving Equations
Newton's Method, also known as the Newton-Raphson method, is a powerful tool for approximating roots of equations. By iteratively improving initial guesses using tangent lines, this method converges towards accurate solutions. This method plays a crucial role in modern calculators and computers for
0 views • 12 slides
Understanding the Conjugate Beam Method in Structural Analysis
The Conjugate Beam Method is a powerful technique in structural engineering, derived from moment-area theorems and statical procedures. By applying an equivalent load magnitude to the beam, the method allows for the analysis of deflections and rotations in a more straightforward manner. This article
1 views • 11 slides
Understanding Roots of Equations in Engineering: Methods and Techniques
Roots of equations are values of x where f(x) = 0. This chapter explores various techniques to find roots, such as graphical methods, bisection method, false position method, fixed-point iteration, Newton-Raphson method, and secant method. Graphical techniques provide rough estimates, while numerica
0 views • 13 slides
Binary Basic Block Similarity Metric Method in Cross-Instruction Set Architecture
The similarity metric method for binary basic blocks is crucial in various applications like malware classification, vulnerability detection, and authorship analysis. This method involves two steps: sub-ldr operations and similarity score calculation. Different methods, both manual and automatic, ha
0 views • 20 slides
Exploring the Audio-Lingual Method in Language Teaching
The Audio-Lingual Method is an oral-based approach that focuses on drilling students in grammatical sentence patterns through behavioral psychology principles. This method, also known as the Michigan Method, emphasizes habit formation and uses techniques like dialogues, repetition drills, and role-p
1 views • 16 slides
Understanding the Kinetics of Fast Reactions in Chemistry
Kinetic methods involve measuring analytical signals under dynamic conditions to study fast reactions in chemistry. This study explores the various methods used, such as Flow Method and Stopped Flow Method, to determine reaction rates accurately. Advantages of the Stopped Flow Method over Continuous
0 views • 18 slides
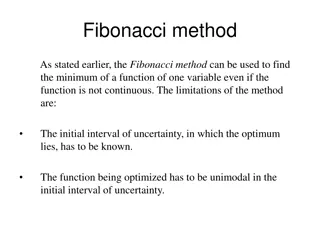
Understanding the Fibonacci Method for Function Optimization
The Fibonacci method offers a systematic approach to finding the minimum of a function even if it's not continuous. By utilizing a sequence of Fibonacci numbers, this method helps in narrowing down the interval of uncertainty to determine the optimal solution through a series of experiments. Despite
1 views • 19 slides
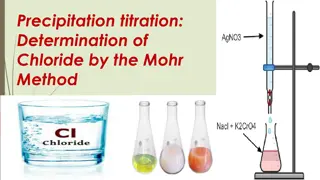
Determination of Chloride by Mohr Method
Precipitation titration is a volumetric method used for determining chloride ions. Mohr's method involves reacting alkaline or alkaline earth chlorides with silver nitrate in the presence of a potassium chromate indicator. The endpoint of the titration is signaled by the appearance of red silver chr
0 views • 9 slides
Determination of Dipole Moment in Chemistry
The determination of dipole moment in chemistry involves methods such as the Temperature Method (Vapour Density Method) and Refractivity Method. These methods rely on measuring various parameters like dielectric constants and polarizations at different temperatures to calculate the dipole moment of
1 views • 15 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Accounting Entries in Hire Purchase System for Credit Purchase with Interest Method
In the Credit Purchase with Interest Method of Hire Purchase System, assets acquired on hire purchase basis are treated as acquired on outright credit basis with interest. This method involves initial entries for recording the asset acquisition, down payments, interest on outstanding balance, instal
0 views • 10 slides
Understanding Singular Value Decomposition and the Conjugate Gradient Method
Singular Value Decomposition (SVD) is a powerful method that decomposes a matrix into orthogonal matrices and diagonal matrices. It helps in understanding the range, rank, nullity, and goal of matrix transformations. The method involves decomposing a matrix into basis vectors that span its range, id
0 views • 21 slides
Understanding Scatter Diagram Method for Correlation Analysis
Scatter Diagram Method is a simple and effective way to study the correlation between two variables. By plotting data points on a graph, it helps determine the degree of correlation between the variables. Perfect positive and negative correlations, as well as high and low degrees of correlation, can
0 views • 11 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Effective Method to Protect Web Servers Against Breach Attacks
Abdusamatov Somon presents an effective method called HTB to protect web servers against breach attacks, focusing on secure computation and mitigation. The research addresses side-channel attacks based on compression and the CRIME BREACH issue, providing insights into implementing the breach attack
1 views • 13 slides
Measurement of Flow Velocity on Frozen and Non-Frozen Slopes of Black Soil Using Leading Edge Method
This study presented a detailed methodology for measuring flow velocity on frozen and non-frozen slopes of black soil, focusing on the Leading Edge method. The significance of shallow water flow velocity in soil erosion processes was emphasized. Various methods for measuring flow velocity were compa
0 views • 23 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Enhancing Animal Telemetry Data Systems for Secure Collaboration
Wide spectrum of animal telemetry data collection protocols and platforms require enhanced data stewardship options for secure sharing before public release. The need for a more granular understanding of available data and structured systems integration is crucial. Initial workflow involves providin
0 views • 4 slides
Secure Method of Information Exchange: Overview of Hub Concept & Prototype
This document presents an overview of the Hub Concept & Prototype for Secure Method of Information Exchange (SMIE) developed in April 2013 by New Zealand and the USA. It discusses drivers, ePhyto transmission options, Direct NPPO to NPPO ePhyto exchange, Hub/Cloud communication, security mechanisms,
0 views • 20 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Understanding Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Exploring Secure Care Services in Scotland
Delve into the world of secure care services in Scotland, focusing on achievements, challenges, and opportunities in providing youth justice. Learn about trends in secure care, reduction in costs, reasons for referrals, and evidence-based programs like DBT in Glasgow. Gain insights from industry lea
0 views • 77 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Foundations of Cryptography: Secure Multiparty Computation
Explore the foundations of cryptography with insights into secure multiparty computation, including the Secure 2PC from OT Theorem and the Two-Party Impossibility Theorem. Delve into the impossibility of 2-Party Secure MPC, claims, and exercises on extending to statistical security. Learn about redu
0 views • 39 slides
Exploration of Cryptography and Secure Communication Methods
Delve into the concepts of cryptography, data hiding, and secure communication methods such as Diffie-Hellman key exchange. Discover how Bob safely sends a ring to Alice, the use of Caesar cipher method, and the importance of mathematical principles in ensuring secure communication protocols. Learn
0 views • 22 slides
Implementing VPN for Secure Corporate Communication
A Virtual Private Network (VPN) offers a secure method for corporations with multiple sites to transfer data over the Internet while maintaining confidentiality. By encrypting data and using tunneling techniques, VPN software ensures that communications remain private, making it a cost-effective and
0 views • 10 slides
Understanding the Shoe Lace Method for Finding Polygon Areas
The Shoe Lace Method is a mathematical process used to determine the area of any polygon by employing coordinate geometry. By following specific steps, including organizing coordinates, multiplying diagonally, and adding columns in a certain manner, the method allows for a straightforward calculatio
0 views • 8 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides