Emergency Response Proposed Rule - Worker Safety and Health Conference
The Emergency Response Proposed Rule aims to update regulations for worker safety and health, expanding coverage to include technical search and rescue and emergency medical service entities. The rule proposes replacing the existing Fire Brigades standard with an Emergency Response standard. Federal
2 views • 23 slides
Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
5 views • 31 slides
Pascal's Rule in NMR Spectroscopy ( n+1 )
Pascal's Rule in NMR spectroscopy, also known as the (N+1) rule, is an empirical rule used to predict the multiplicity and splitting pattern of peaks in 1H and 13C NMR spectra. It states that if a nucleus is coupled to N number of equivalent nuclei, the multiplicity of the peak is N+1. The rule help
1 views • 30 slides
TSA Updates on Security Training Rule for OTRB Companies
In the recent updates by TSA, the Security Training Rule for over-the-road bus (OTRB) companies has been highlighted. The rule mandates TSA-approved security training for employees in security-sensitive roles, emphasizing key requirements and elements of security training. Urban areas covered by the
1 views • 18 slides
Exploring 'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Compliance Guide for Rule 205: Emission Offsets & Mobile Source Credits
Rule 205 outlines the process for generating emission offsets through voluntary mobile source emission reduction credits in Maricopa County. The rule-making process, state implementation plan submission, and permit conditions related to Rule 205 are discussed. The preparation for compliance includes
0 views • 7 slides
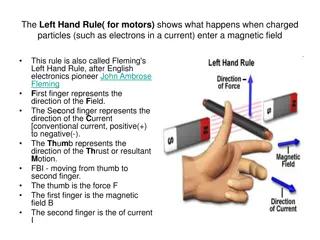
Understanding Fleming's Left Hand Rule and Electric Motors
Fleming's Left Hand Rule, also known as the Left Hand Rule for Motors, explains the interaction between charged particles and magnetic fields. Electric motors utilize this principle to convert electrical energy into mechanical energy through the interaction of magnetic fields and current-carrying co
2 views • 6 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Understanding the Rule of Law and Legal Systems in Wales and England
The content discusses the nature of law, the Welsh and English legal systems, and the Rule of Law doctrine. It includes observations from the 2019 AS Law Unit 1 examination, emphasizing the importance of adhering to rubrics and answering questions clearly. Candidates faced challenges with timing and
0 views • 14 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Phase 2 Comprehensive Rule Update Legislative Rule Package Overview
Seven subdivision bills were adopted during the 2023 session, covering various topics such as independent reviewers, cut and fill systems, connection to public sewer systems, and more. The public comment period and hearing are scheduled, with the draft rule to respond to comments by August 25. A bil
3 views • 17 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
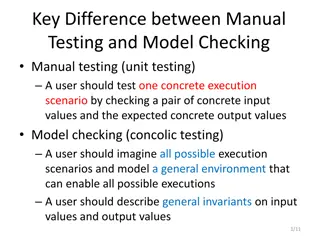
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
2 views • 4 slides
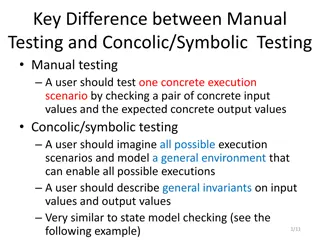
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Michigan Revised Lead and Copper Rule Implementation Experience
The Michigan Department of Environment, Great Lakes, and Energy shares insights on the implementation of the Michigan Revised Lead and Copper Rule. Key topics include rule revisions, data outcomes, challenges, and development drivers. The rule aims to reduce lead levels, update sampling protocols, a
0 views • 26 slides
EPA Rule 40 CFR Part 63 Subpart HHHHHH Overview
EPA Rule 40 CFR Part 63 Subpart HHHHHH, also known as The Refinisher Rule, sets standards for hazardous air pollutants in paint stripping and surface coatings operations. The rule aims to control emissions of target hazardous air pollutants in collision centers and surrounding areas. It outlines req
0 views • 20 slides
Understanding the Mailbox Rule in Contract Law
The Mailbox Rule, a common law principle, stipulates that acceptance of an offer is valid when dispatched, providing certainty in contract formation. This rule is illustrated through scenarios involving delays in mail delivery and parties' need for assurance in contractual agreements. The examples h
0 views • 14 slides
Evolution of Theory and Knowledge Refinement in Machine Learning
Early work in the 1990s focused on combining machine learning and knowledge engineering to refine theories and enhance learning from limited data. Techniques included using human-engineered knowledge in rule bases, symbolic theory refinement, and probabilistic methods. Various rule refinement method
0 views • 12 slides
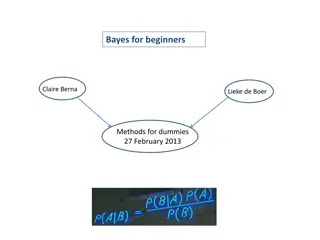
Understanding Bayes Rule and Its Historical Significance
Bayes Rule, a fundamental theorem in statistics, helps in updating probabilities based on new information. This rule involves reallocating credibility between possible states given prior knowledge and new data. The theorem was posthumously published by Thomas Bayes and has had a profound impact on s
0 views • 34 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Exploring Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
History and Implementation of Military Munitions Rule
The history and implementation of the Military Munitions Rule, including its origins in regulations like RCRA and FFCA, the involvement of key stakeholders, identification of issues in rulemaking, and ensuring safe transportation and storage of hazardous waste. The process involved extensive consult
0 views • 26 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
Understanding the Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
Introduction to Bayes' Rule: Understanding Probabilistic Inference
An overview of Bayes' rule, a fundamental concept in probabilistic inference, is presented in this text. It explains how to calculate conditional probabilities, likelihoods, priors, and posterior probabilities using Bayes' rule through examples like determining the likelihood of rain based on a wet
0 views • 21 slides
Understanding the New VA Pension Benefit Rule of October 11, 2018
VA Task Force members presented key changes in the VA pension benefit rule, focusing on net worth limits, transfer rules, exclusions, look-back periods, and penalties. The rule aims to uphold program integrity and align with GAO recommendations, impacting eligibility criteria for applicants. Key sec
11 views • 55 slides
Inferential Statistics Solutions for Challenging Problems in Section B
The provided statistical problems in Section B involve calculating the expected number of shoppers spending specific durations at a furniture shop and reasons for not checking the weight of each packet when filling corn flakes. Solutions include determining the shoppers expected to spend more than 4
0 views • 25 slides
U.S. EPA's Proposed Cross-State Air Pollution Rule Update for 2008 Ozone NAAQS
The U.S. Environmental Protection Agency (EPA) issued the Cross-State Air Pollution Rule (CSAPR) in 2011, aiming to improve air quality by reducing power plant emissions across state lines. Challenges and subsequent revisions led to the proposed CSAPR Update Rule in 2015, targeting interstate air po
0 views • 27 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Implications of ABA Model Rule 8.4(g) on Professional Conduct
The American Bar Association's Model Rule 8.4(g) addresses professional misconduct in legal practice related to discrimination and harassment based on various factors. The rule has been adopted by some states, sparking discussions on its implications and challenges within the legal community. Explor
0 views • 67 slides
Conflict Checking Process in Heraldry: Armory 104 Overview
Delve into the intricacies of conflict checking using the ordinary in heraldry with Armory 104. Explore prerequisites, review key concepts, understand where SCA-registered armory is located, and learn the process of identifying and analyzing charge groups to ensure uniqueness in designs. Avoid commo
0 views • 28 slides
Ethics & Constitutional Limits on Attorney Expression Webinar
Join the live 90-minute webinar on Ethics: Model Rule 8.4(g) and Constitutional Limits on Regulating Attorney Expression of Unpopular Positions featuring expert faculty members. Explore regulations governing lawyer speech and the requirements for lawyer communication in various contexts. Learn about
0 views • 57 slides
Upholding the Rule of Law for Sustainable Economic Growth in Europe
Democracy and the rule of law are essential for sustained economic growth in Europe. The rule of law ensures stable and impartial enforcement of rules such as property rights and contract law, key for market economies. Upholding the rule of law is crucial for combating corruption and maintaining a f
0 views • 6 slides
Bayes’ Rule
Bayes Rule, a fundamental concept in statistics, explores how prior beliefs are updated based on new evidence. This rule, named after Thomas Bayes, has had a profound impact on statistical inference and has been further developed by mathematicians like Laplace. Exploring the probabilistic reasoning
0 views • 34 slides
Subtyping and Type Checking in Programming Language Design
In the realm of programming language design, subtyping and type checking play crucial roles. This content delves into how syntax-directed rule systems evolve when dealing with subtyping, presenting the challenges and the solutions through a recursive algorithm approach. The discussion includes the t
0 views • 40 slides
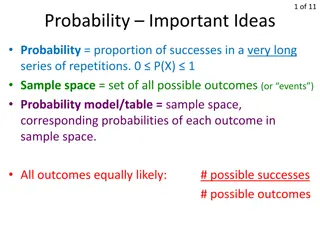
Understanding Probability: Key Concepts and Rules
Probability is the proportion of successes in a long series of repetitions. Important ideas include the 0-1 Rule, the 100% Rule, the Complement Rule, the Addition Rule, and the Multiplication Rule. These rules govern the calculation of probabilities in various scenarios. Learn the fundamental princi
0 views • 16 slides