Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Enhancing Wi-Fi Relay Networks for Improved Coverage and Reliability
This document discusses the need to enhance relay frameworks in Wi-Fi networks to improve coverage, reliability, and performance of stations in different ranges. It highlights the challenges of S1G-based relays, proposes enhancements to the relay framework, and introduces new types of relay framewor
1 views • 12 slides
Understanding Relay, Optoisolator, and Stepper Motor Interfacing with 8051 Microcontroller
Explore the fundamentals of relays, optoisolators, and stepper motors along with their interfacing with the 8051 microcontroller. Learn about relay characteristics, operation, optoisolator linking, and stepper motor control through programming examples in Assembly and C.
21 views • 28 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Understanding the 5V Relay Module and Its Applications
A 5V relay module is an electrically activated switch commonly used in switching circuits for home automation projects, controlling heavy loads, safety circuits, and automotive electronics. This small relay board works with a 5V signal and can handle up to 10A of current for both AC and DC loads. It
1 views • 7 slides
Comprehensive Guide to Transformer Buchholz Relay by Prof. V. G. Patel
Understanding the significance of Buchholz relay in protecting transformers from incipient faults that can develop into serious issues. Developed by Max Buchholz in 1921, this gas-operated device detects faults such as core insulation failure, short-circuited core laminations, and loss of oil due to
3 views • 14 slides
Considerations for Relay Operation in Next Generation Wi-Fi Networks
In this document, considerations and use cases for relay operation in next generation Wi-Fi networks are discussed. The authors provide insights into the improvements in reliability and throughput, focusing on the benefits of relay features in various scenarios such as smart home devices and automot
0 views • 11 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Fun Team Relay Games for Physical Education
Engage in exciting and interactive team relay games like Locomotor Relay, Long Jump Relay, Crab Walk Relay, Over/Under Relay, and V-Sit Relay. These activities promote teamwork, coordination, and physical fitness in a fun and engaging way. Set up cones, form teams, and enjoy these dynamic relay chal
0 views • 6 slides
Enhancing Communication: The Role of Relay Services for Individuals with Hearing or Speech Disabilities
Explore the importance of telephone communication for individuals with hearing or speech disabilities, and how relay services facilitate communication through text transcription. Learn about the speed of transcription, VCO services, and the basic method of communication that is often taken for grant
0 views • 18 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Evolution of Relay Services for Deaf and Hard of Hearing Individuals
The history of relay services for the deaf and hard of hearing dates back to the 1960s in the USA. Three pioneering deaf men played a significant role in establishing the first successful deaf telephone network, leading to the development of relay services as we know them today. This evolution enabl
0 views • 29 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
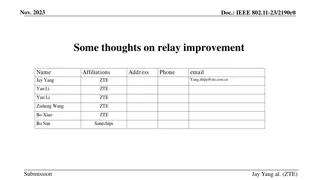
Relay Communications for Ultra High Reliability in IEEE 802.11-22/1908r1
Investigating relay communications to enhance Rate-vs-Range (RvR) performance for Ultra High Reliability (UHR) in IEEE 802.11-22/1908r1. The content explores relay design objectives, goodput analysis, existing relay solutions like WiFi extenders, and the challenges in implementing relay technology t
3 views • 16 slides
Understanding Electrical Relays and Contactors
An electrical relay is a magnetic switch that utilizes electromagnetism to control contacts. Relays consist of a coil and contacts insulated from each other, with different types like normally open (NO) and normally closed (NC) contacts. Contactors, a specialized type of relay, handle heavy power lo
2 views • 43 slides
Understanding Electrical Relays and Contactors
An electrical relay is a magnetic switch that uses electromagnetism to control contacts. Relays can have various contacts and functions, with coils insulated from contacts. They include normally open (NO) and normally closed (NC) contacts for different operations. Contactors are specialized relays f
0 views • 62 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Understanding Wide Area Networking Using Frame Relay Cloud
The field of networking is advancing rapidly, with technologies like cloud computing relying on robust wide area networking. This presentation explores the use of Frame Relay Cloud in improving the security and configuration complexities faced in interconnecting wide area networks. It discusses the
0 views • 16 slides
Enhancing Internet Telephony Quality Through Predictive Relay Selection
Examining the quality of Internet telephony in relation to network performance, this research explores the use of Managed Overlay to improve call quality for services like Skype. Analysis of 430 million Skype calls reveals that a significant portion experience poor network performance, emphasizing t
1 views • 26 slides
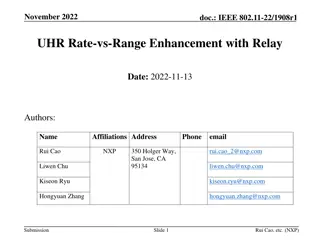
IEEE 802.11-23/1899r0 Relay Operation for 11bn - Presentation Summary
In this presentation, the IEEE 802.11-23/1899r0 document discusses relay operations to improve Rate-vs-Range (RvR) performance for UHR. Various potential solutions for implementing a relay protocol in UHR are explored, focusing on enhancing multi-hop channel access delay, end-to-end QoS, and simplif
0 views • 10 slides
Considerations for Relay Operation in Next-Gen Wi-Fi Networks
This presentation discusses the considerations and features for relay development in next-generation Wi-Fi networks, focusing on improving coverage in dead zones, enhancing throughput, and reducing energy consumption. It explores concepts like multi-traffic multiplexing in relay transmission and pow
0 views • 9 slides
Understanding Relay Logic and Circuits
Explore the world of relay logic and circuits with detailed explanations, images, and practical examples. Learn about basic relays, labeling, simple relay logic circuits, sump pump relay circuit, NAND burglar alarm, and various relay logic gates (AND, OR, NAND, NOR). Dive into the functioning of rel
0 views • 17 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
IEEE 802.11-24/0386r0 Lower MAC Relay Protocol Details
Detailed discussion on supporting the relay protocol in IEEE 802.11bn, covering relay addressing, end-to-end BA, relay TXOP protection, beacon forwarding, security processing, non-UHR STA support, sounding procedure, A-MPDU aggregation, de-aggregation, and more. The relay operation involves relay de
0 views • 16 slides
Exploring Various Relay and Sensor Projects
In this content, we dive into different projects involving relays and sensors. From controlling a relay with Arduino to using light sensors and joysticks for interactive applications, these projects offer a hands-on approach to understanding and experimenting with electronic components. Additionally
0 views • 11 slides
Exploring Distance Bounding: Facts, Hopes, and Perspectives
Delve into the world of distance bounding with Maria Cristina Onete as she discusses the secure authentication, relay attacks, distance-bounding protocols, properties, and attacks. Learn about the challenges and implementations of mobile distance bounding, mafia and terrorist fraud resistance, and h
0 views • 34 slides
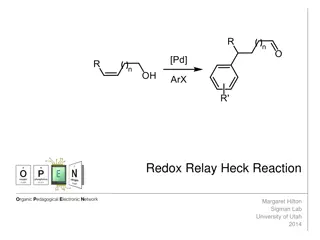
Understanding the Redox-Relay Heck Reaction in Organic Synthesis
The Redox-Relay Heck Reaction is a powerful tool in organic synthesis that allows for the functionalization of olefins with aryl groups. Developed by Sigman and colleagues, this reaction involves a palladium-catalyzed relay controlled by a thermodynamic sink, leading to the formation of aldehydes or
0 views • 6 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Energy Efficient Relay Antenna Selection for AF MIMO Two-Way Relay Channels
The study explores energy-efficient relay antenna selection for AF MIMO two-way relay channels, aiming to optimize energy efficiency while maintaining performance. It discusses the advantages and disadvantages of two-way MIMO relay systems, emphasizing higher spectral efficiency, improved reliabilit
0 views • 17 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Understanding DDoS Attacks: Simulation, Analysis & Defense
Delve into the world of Distributed Denial of Service (DDoS) attacks with this comprehensive study covering the architecture, advantages, bot installation phases, attack methods, defenses, and simulation. Learn about the detrimental impact of DDoS attacks on servers, their multi-tiered structure, an
0 views • 20 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides