The DEENIN Underscarf with Tie-Back Closure Redefines Hijab Comfort and Style
Within the realm of Muslim women who proudly wear the hijab, achieving the delicate equilibrium between style and utility holds utmost significance. The hijab transcends being merely an article of clothing; it embodies faith, identity, and individual expression. Recognizing the diverse needs and asp
2 views • 2 slides
Comprehensive Guide to FERC Order 676j Managed Encumbrance Process
This comprehensive guide provides step-by-step instructions on managing encumbrances under FERC Order 676j. Learn about creating new encumbrances, untagged pseudo-ties using PTP or NITS TSR, and accessing dynamic notifications within the system. Detailed images and clear explanations make this guide
1 views • 25 slides
Understanding Alkaloids: Sources, Names, and Classification
Alkaloids, organic nitrogenous compounds of plant origin, are physiologically active and can contain elements like carbon, hydrogen, nitrogen, oxygen, sulfur, and more. They are found in various plant families such as Leguminosae, Papaveraceae, and Solanaceae. Alkaloids can be sourced from plants, a
3 views • 21 slides
Understanding Tannins: Properties, Classification, and Medicinal Uses
Tannins are secondary metabolite products with astringent properties, high molecular weight, and various solubility and taste characteristics. They can be classified into true tannins and pseudo-tannins based on the Goldbeater skin test, as well as hydrolysable and condensed tannins based on chemica
6 views • 13 slides
Pseudo-Scientific Ideas About Race and Eugenics in the USA and Australia
The eugenics movement in the USA, under leaders like Charles Davenport, promoted the separation of "inferior" races to prevent genetic contamination of the "superior" groups. Laws like the Virginia Racial Integrity Act enforced racial segregation and punished interracial marriages. This era saw the
1 views • 20 slides
MIPS CPU Design Using Verilog and Instruction Set Architecture Overview
Explore the world of MIPS CPU design using Verilog with a deep dive into Instruction Set Architecture (ISA), SPIM instruction formats, addressing modes, and more. Learn about the key components such as Program Counter (PC), Instruction Memory (IM), Register Files (RF), Arithmetic Logic Unit (ALU), D
1 views • 29 slides
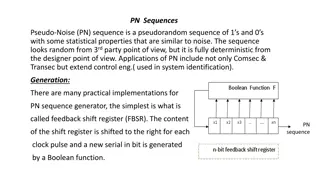
Understanding Pseudo-Noise Sequences and Applications
Pseudo-Noise (PN) sequences are deterministic yet appear random, with applications in various fields such as communication security, control engineering, and system identification. Generated using shift registers, they exhibit statistical properties akin to noise. Linear and nonlinear feedback shift
1 views • 19 slides
Understanding Spread Spectrum Communication Systems
Spread spectrum techniques involve spreading a signal over a wide bandwidth for various reasons, such as secure communication, resistance to interference, noise, and jamming. This summary introduces Direct Sequence Spread Spectrum (DSSS), Frequency Hopping Spread Spectrum (FHSS), Time Hopping, and h
0 views • 25 slides
Understanding Assembler Directives and Symbols in Assembly Language
Assembly language is a low-level programming language used for computers, microprocessors, microcontrollers, and ICs. It consists of instructions and directives (pseudo instructions). Assembler directives are statements that guide the assembler during the assembly process. Categories of directives i
3 views • 39 slides
Patch Bundle Mode Walkthrough for Device Configuration
Explore the Patch Bundle Mode walkthrough consisting of flowcharts and pseudo code examples for controlling a device's patch mode, downloading configurations, and changing device modes. The content provides a detailed guide on using commands to initiate patch burst mode, specify I2C addresses, and t
0 views • 4 slides
Exploring Monte Carlo Simulations and Probabilistic Techniques
Dive into the world of Monte Carlo simulations and probabilistic methods, understanding the basic principles, the Law of Large Numbers, Pseudo-Random Number Generators, and practical Monte Carlo steps. Explore topics like conditional probability, basic geometry, and calculus through engaging exercis
3 views • 10 slides
Overview of Alkaloids: Classification, Sources, and Characteristics
Alkaloids are organic nitrogenous compounds found in plants with physiological activity. They may also contain elements like oxygen, sulfur, chlorine, and phosphorus. Alkaloids can be sourced from plants, animals, bacteria, fungi, or industrial synthesis. Their names can be derived from plant names,
0 views • 19 slides
Frenectomy, Tongue Tie Melbourne | Rosanna Family Dental Clinic
Frenectomy is simple surgical procedure to remove the frenum tissues or tongue, also known as Tongue tie treatment. To know more, call Rosanna Family Dental Clinic in Melbourne on (03) 94591194.\n\n
0 views • 2 slides
Understanding Reasonable Arguments vs. Pseudo-Arguments
The provided content focuses on distinguishing between reasonable arguments and pseudo-arguments through thought-provoking questions such as the ethical treatment of animals, city subsidies for sports venues, and subjective opinions on aesthetics. It also explains the structure of an argument, highl
0 views • 18 slides
Understanding Pseudo Code and Flow Charts for Algorithm Analysis
Explore the concepts of pseudo code and flow charts for analyzing algorithms, problem-solving, and understanding space and time complexity. Learn about basic elements of pseudo code, assigning operations, and writing effective pseudo code statements in a clear and structured manner. Discover the imp
0 views • 26 slides
Algebraic Solutions for Two-Dimensional Adjoint QCD
Two-dimensional adjoint QCD is explored with a basis-function approach aiming to achieve single-particle states over cluttered multi-particle states. The algebraic solution involves t'Hooft-like integral equations and pseudo-cyclicity considerations to address parton number violation and boundary co
0 views • 22 slides
Phonic Screening Checks Bank of Words 2012-2019
Explore real and pseudo words featuring various phonetic patterns such as CVC, CCVC, CVCC, CVVC, CCVCC, VCC, CVVV, CCVVV, CVCV, CCVCV, CCCVCC, CCCVC, CCCVV, and more from Phonic Screening Checks between 2012 and 2019.
0 views • 420 slides
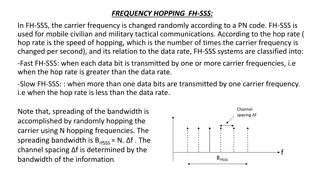
Understanding Frequency Hopping Spread Spectrum Systems
Frequency Hopping Spread Spectrum (FH-SSS) is a technique where the carrier frequency changes randomly using a Pseudo-Noise (PN) code. It is widely used in mobile civilian and military communications for secure and efficient data transmission. FH-SSS systems are classified as Fast or Slow based on t
0 views • 6 slides
Exploring Pseudo-Goodwin Cycles in a Minsky Model
This paper delves into the dynamics of Pseudo-Goodwin cycles within a Minsky model, examining the counter-clockwise movement of output and wage share. It distinguishes between true Goodwin cycles and pseudo variants, highlighting the role of income distribution, debt, and demand in shaping economic
0 views • 27 slides
Understanding Process Games in Systems Programming Lab
Explore the simulation of process games where programs replicate themselves within a limited arena, learning about the players' goals, finding processes through /proc, and the purpose of the pseudo-file system. Discover the significance of /proc in accessing process information and the methods to in
0 views • 27 slides
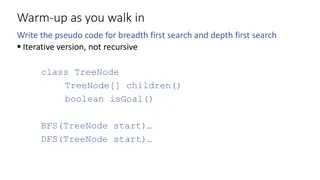
AI Search Algorithms: BFS and DFS Pseudo-code Iterative Version
Explore the iterative versions of Breadth First Search (BFS) and Depth First Search (DFS) with pseudo-code examples implemented for class TreeNode. Understand the concept of TreeNode, children() function, isGoal() method, and apply BFS and DFS starting from TreeNode start.
0 views • 53 slides
Understanding Random Class in Java Programming
The Random class in Java is used to generate pseudo-random numbers. By utilizing methods such as nextInt and nextDouble, you can generate random integers and real numbers within specified ranges. This chapter explores common usage scenarios, such as generating random numbers between specific ranges
2 views • 10 slides
Post-Quantum Security of Hash Functions Explained
Explore the intricacies of post-quantum secure hash functions, their properties, surprises, and implications in quantum settings. Delve into collision resistance, pseudo-random generators, efficient signatures, and more, presented by Dominique Unruh from the University of Tartu.
0 views • 23 slides
Key Learnings from Exams: Algorithm Strategies & Representations
Exploring vital lessons from exams, including algorithm development tips, representation examples, and pseudo-code explanations. Understand the importance of reading questions carefully, creating precise steps, and terminating algorithms effectively. Dive into the world of algorithms, pseudo-code, a
0 views • 44 slides
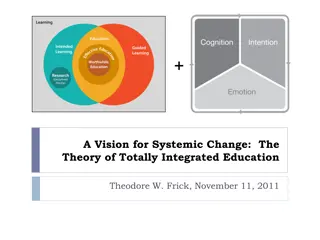
Enhancing Education Through Totally Integrated Approach
Theodore W. Frick's Theory of Totally Integrated Education (TIE) emphasizes aligning student cognition, intention, and emotion with authentic learning tasks to create worthwhile education. TIE focuses on systemic change in education and provides a vision for improving learning outcomes by connecting
0 views • 55 slides
Lessons Learned from On-Orbit Anomaly Research
The On-Orbit Anomaly Research workshop held at the NASA IV&V Facility in 2013 focused on studying post-launch anomalies and enhancing IV&V processes. The presentations highlighted common themes like Pseudo-Software Command Scripts, Software and Hardware Interface issues, Communication Protocols, and
0 views • 55 slides
Pseudodeterministic Algorithms and Their Application in Search Problems
Pseudodeterministic algorithms provide a unique approach to the search problem associated with binary relations, offering an error reduction technique while sacrificing the ability to approximate the average value of a function. By introducing m-pseudodeterministic and pseudo-pseudodeterministic alg
1 views • 6 slides
Court Attire Guidelines for Attorneys and Witnesses: Professional Dress Code
Court attire recommendations for female attorneys and witnesses include wearing professional suits in black, navy, or gray, with clothing items like suit jackets, dresses, pants/skirts, tops, hosiery/trouser socks, and pumps/flats. For male attorneys and witnesses, the attire consists of suits, jack
0 views • 5 slides
Introduction to Psychology: Understanding Behavior and Mental Processes
This material covers key aspects of psychology including the definition of psychology, its scientific nature, comparison with fake sciences, the birth of modern psychology, and different perspectives in psychology such as learning, biological, cognitive, and sociocultural. It delves into the roots o
0 views • 42 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Understanding Tie Lines in Ternary Systems
Ternary systems involve three components where partial miscibility can lead to phase separation. Adding alcohol to a benzene-water mixture can promote miscibility by acting as an intermediary solvent. By breaking cohesive bonds and increasing heat, the system can transition to a single phase. The pr
0 views • 15 slides
Exploring Pseudo-Complex General Relativity for Gravitational Waves
Delve into the concept of pseudo-complex General Relativity (PC-GR) as an alternative theory to Einstein's General Relativity. The study considers algebraic extensions, weak field limits, and the extension of metrics in momentum-energy space. By analyzing predictions and implications, this research
0 views • 21 slides
Pseudo-Tie Business Procedure Tariff Administration, August 2017
Pseudo-tie business procedure tariff administration from August 2017 outlines the purpose, implementation, and types of pseudo-ties in the energy industry. It covers dynamic transfers, pseudo-tie procedures, and various stakeholder involvements. The document details the process of implementing pseud
0 views • 11 slides
Understanding Pseudo-Tie Entry in Electric Industry Registry
Explore the requirements and measures of NERC Standard INT-004-3.1 for dynamic transfers in the electric industry. Learn about data fields required for pseudo-tie entry and approval methodology in the Electric Industry Registry. Discover the publishing schedule for EIR entries and the approval proce
0 views • 6 slides
Proposal for Modeling Cross-Tie Resources for Northern Grid Analysis
The TransCanyon proposal outlines the Cross-Tie Transmission Project, a 213-mile, 1500 MW, 500 kV HVAC line aiming to strengthen electrical interconnections and facilitate power transfers between different regions. The NorthernGrid proposal involves modeling base cases to study resource dispatch, fo
0 views • 6 slides
Ordering of Pseudo Dispatch Instructions for QBOA
This document outlines the specific order in which Pseudo Dispatch Instructions (DIs) are to be arranged for QBOA in scenarios where multiple instructions are issued simultaneously. The order prioritizes certain instructions to maintain consistency and alignment with system implementation rules.
0 views • 11 slides
Understanding Blood Vessel Leakiness Control Mechanisms
Blood vessel leakiness, a common feature in diseases like inflammation, metastasis, and viral hemorrhagic infections, is controlled by factors such as Angiopoietins and the Tie-2 pathway. Activation of Tie-2 leads to increased vessel diameter, allowing the transfer of white blood cells, while deacti
0 views • 16 slides
Understanding Social Network Dynamics: Tie Strength, Triadic Closure, and Human Relationships
Explore the concepts of tie strength in social networks, the strong vs. weak ties distinction, Dunbar's number theory on stable relationships, the role of common friends in friendship formation, and the reasons behind triadic closure in network dynamics. Discover how human relationships are influenc
0 views • 38 slides
Understanding Pseudo Code: A Beginner's Guide to Organizing Programs
Pseudo code is a helpful way to organize your program logic before actual coding. It provides a structured outline from inputs to outputs, focusing on step-by-step guidelines that are not language-specific. This guide covers the basics of pseudo code, including general guidelines, steps to pseudo co
0 views • 29 slides
Handling Label Noise in Semi-Supervised Temporal Action Localization
The Abstract Semi-Supervised Temporal Action Localization (SS-TAL) framework aims to enhance the generalization capability of action detectors using large-scale unlabeled videos. Despite recent progress, a significant challenge persists due to noisy pseudo-labels hindering efficient learning from ab
0 views • 30 slides