Comprehensive Guide to Contraception and Birth Control Methods
Safe sex practices are crucial for preventing unplanned pregnancies and sexually transmitted infections (STIs). This guide discusses various contraception methods including barrier methods like male and female condoms, hormonal contraceptives such as oral pills, and their effectiveness rates. Cost,
0 views • 23 slides
Extension Teaching Methods
Extension teaching methods play a crucial role in facilitating communication and knowledge transfer between rural communities and extension workers. These methods aim to engage, stimulate, and guide learners through the process of acquiring new skills and knowledge. Centurion University in India emp
4 views • 8 slides
Understanding Veal: Types, Characteristics, Grading, and Cooking Methods
Veal is a tender meat sourced from young calves aged 6-7 months. It has a light color, fine texture, and smooth taste. Learn about different types of veal such as Bob Veal and Special-Fed Veal, as well as the grading system for veal carcasses. Discover the various cuts of veal and explore recommende
1 views • 9 slides
Understanding Heat Transfer and Cooking Methods
Explore the various methods of heat transfer and cooking techniques, including moist-heat and dry-heat methods. Learn about the objectives of heating foods, types of heat transfer such as conduction and convection, and how different methods affect the texture, flavor, and nutritional content of food
0 views • 21 slides
Comprehensive Guide to Natural Family Planning Methods
Family planning methods offer individuals control over their fertility through various contraception options, including natural methods like Basal Body Temperature (BBT), Rhythm method, Cervical Mucus/Ovulation method, and Sympto-thermal method. These techniques help in determining the fertile windo
5 views • 39 slides
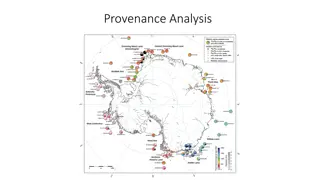
Understanding Sediment Provenance in Geology
Sediment provenance in geology involves reconstructing the origin of sediments through compositional analyses to determine erosion history and geographical origins. It helps characterize the journey of sediments from source to sink, providing insights into tectonic and paleoclimatic histories. Prove
1 views • 11 slides
Designing Trustworthy Virtual Labs: Considerations and Reflections
Explore the characteristics and features crucial for designing trustworthy virtual labs, including transparency, provenance, and social aspects. Delve into the importance of trust in digital collaborations and co-productions. Reflect on balancing competing interests and the need for a nuanced approa
0 views • 7 slides
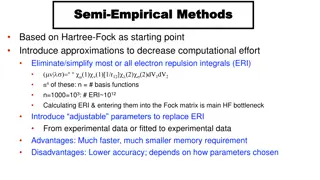
Overview of Semi-Empirical Methods Based on Hartree-Fock
Semi-empirical methods derived from Hartree-Fock theory aim to reduce computational effort by approximating or eliminating electron repulsion integrals. Strategies include introducing adjustable parameters to replace ERI calculations and utilizing zero differential overlap methods like CNDO, INDO, N
1 views • 11 slides
EUROfusion Data Management Project Summary
EUROfusion data management project led by P. Strand at Chalmers outlines a comprehensive data management plan with four scenarios of increasing ambition, from making metadata available to open access for non-embargoed data. The plan includes strategies for interoperability, data accessibility, enhan
0 views • 11 slides
How to Check a Simulation Study: Methods and Considerations
Simulation studies are often used to evaluate statistical methods and study power, but they can sometimes produce misleading results. This work discusses strategies to assess and improve the quality of simulation studies, drawing on experiences and considerations outlined in relevant literature. A s
0 views • 31 slides
Understanding Contraception: Methods, Importance, and Considerations
Contraception refers to methods used to prevent unwanted pregnancies, regulate pregnancy timing, and spacing between pregnancies. It is essential for women's reproductive health and can include barrier methods, hormonal methods, emergency contraception, and intrauterine devices. These methods are sa
1 views • 28 slides
Understanding Sentiment Classification Methods
Sentiment classification can be done through supervised or unsupervised methods. Unsupervised methods utilize lexical resources and heuristics, while supervised methods rely on labeled examples for training. VADER is a popular tool for sentiment analysis using curated lexicons and rules. The classif
7 views • 17 slides
Comprehensive Overview of Numerical Linear Algebra Methods for Solving Linear Systems
Explore numerical linear algebra techniques for solving linear systems of equations, including direct and iterative methods. Delve into topics like Gaussian elimination, LU factorization, band solvers, sparse solvers, iterative techniques, and more. Gain insights into basic iterative methods, error
6 views • 12 slides
The Importance of Research Methods in Building Knowledge and Answering Questions
Research methods play a pivotal role in shaping how we construct knowledge, address research inquiries, and determine the questions we can explore. Practices in research are evolving with open-science initiatives, data sharing, and innovative methods across interdisciplinary fields. Objectives have
0 views • 21 slides
Optimization Methods: Understanding Gradient Descent and Second Order Techniques
This content delves into the concepts of gradient descent and second-order methods in optimization. Gradient descent is a first-order method utilizing the first-order Taylor expansion, while second-order methods consider the first three terms of the multivariate Taylor series. Second-order methods l
0 views • 44 slides
Introduction to Numerical Methods: A Comprehensive Overview
Numerical methods play a crucial role in solving mathematical problems efficiently through arithmetic operations. This lecture by Dr. Nur Uddin covers the fundamental concepts of numerical methods, emphasizing their importance in engineering problem-solving with the use of modern digital computers.
1 views • 17 slides
Understanding Methods of Social Work
Methods of social work encompass various approaches aimed at enhancing social functioning and addressing problems in individuals and communities. These methods are categorized into primary and secondary methods, each serving different purposes in the field. Primary methods involve direct interaction
0 views • 20 slides
Provenance Analysis of Algorithms - Understanding Data Dependencies
Exploring the concept of provenance analysis in algorithms to understand how output items depend on input items. This analysis goes beyond traditional activity logs, focusing on structured collections of items and exploring various applications for causal and quantitative analysis. The critical test
1 views • 16 slides
Terra Architecture and Design Overview
Terra is a platform driven by the Data Biosphere vision to enable an ecosystem of interoperable components across organizations. It utilizes GA4GH standards and serves various roles such as Biomedical Researchers, Custom Apps & Portals, and Data Developers. The architecture is being restructured to
0 views • 8 slides
Understanding Moving Averages and Exponential Smoothing Methods
Forecasting methods like moving averages and exponential smoothing are essential for analyzing time series data. Averaging methods involve equally weighted observations, while exponential smoothing methods assign unequal weights that decay exponentially. Both methods can be useful for forecasting in
0 views • 18 slides
Efficient Methods and Considerations for Solid Waste Disposal
Efficient methods for solid waste disposal include sanitary landfilling, which involves compacting waste and covering it with soil daily. Advantages of this method include economic viability and flexibility in waste disposal. However, challenges such as limited suitable land availability and potenti
0 views • 10 slides
Overview of Open Provenance Model Tutorial Session 3
Explore Session 3 of the Open Provenance Model Tutorial, covering topics like the XML Schema for OPM, OWL ontology, OPM Layered Architecture, XML Binding, RDF Binding, and more. Dive into OPM Layered Model, XML Binding, OPM Graph, OPM Process, and OPM Artifact to understand specialized domains and e
0 views • 22 slides
Types of Birth Control Methods and Their Effectiveness
Explore the different types of birth control available, including abstinence, hormonal methods, barrier methods, and permanent methods. Learn about the effectiveness rates, how they work, and their pros and cons to make an informed decision about contraception. From hormonal options like pills, patc
0 views • 23 slides
Convex Optimization: Interior Point Methods Formulation
This chapter on interior point methods in convex optimization explores the formulation of inequality-constrained optimization problems using barrier methods and generalized inequalities. It covers primal-dual interior point methods and discusses issues such as exponential complexity and determining
0 views • 24 slides
Understanding Open Provenance Model (OPM) in Session 2
Dive into Session 2 of the Open Provenance Model tutorial to grasp the abstract model of OPM, its inferences, and efforts to imbue it with semantics. Explore OPM requirements, non-requirements, domain specialization, and its core layers. Discover how OPM allows for precise exchange of provenance inf
0 views • 51 slides
Understanding Cooking Methods and Their Impact on Food
Cooking is not just about preparing food; it involves various methods that affect taste, texture, and nutrients. Different heat transfer methods play a crucial role in how food cooks, and understanding dry heat, moist heat, and combination cooking methods can help achieve desired results. From saut�
0 views • 23 slides
EPA Compliance Basics: Tank Leak Detection and Monitoring Methods
Learn about EPA requirements for tank leak detection, release detection methods, and compliance methods for monitoring tank systems. Understand the importance of implementing effective leak detection systems to prevent contamination and comply with federal regulations, including Automatic Tank Gaugi
0 views • 18 slides
Understanding Sedimentary Rock Characteristics: Provenance and Weathering
Explore the significance of provenance analysis in interpreting the origin of sedimentary rocks based on lithological characteristics. Learn about mechanical and chemical weathering processes, compositional and textural maturity, mineral stability during weathering, and how rock particles indicate t
0 views • 12 slides
Solving Systems of Equations: New Methods and Applications
The content discusses various methods for solving systems of equations, including substitution and elimination methods. It presents real-world problems involving money, sales figures, and fishing competitions to demonstrate the application of these methods. Readers will learn how to apply these tech
0 views • 10 slides
Italian Illustrated Editions and Provenance Research Projects
Research projects at Cambridge University Library focused on Italian illustrated editions, bibliophilia, book trade, and provenance information of incunabula. Work involved updating records, organizing provenance data, and collaborating on cultural web portal projects supported by Sapienza Universit
0 views • 7 slides
Enhancing Provenance Research for Reproducibility and Performance
Explore the development of provenance research at the Pacific Northwest National Laboratory, focusing on goals, methodologies, and plans for incorporating time-series metrics to increase scalability and performance. Collaboration with ACME IPPD Panorama is highlighted, showcasing advancements in cap
0 views • 6 slides
Procedural Decomposition and Static Methods in Programming
Understanding procedural decomposition and static methods is essential in programming to reduce redundancy, organize code effectively, and manage complexity. Procedural decomposition involves dividing a problem into methods, while static methods help in code reuse and managing complexity. By designi
0 views • 18 slides
Understanding Distributed Ledger Technology Concepts
Distributed Ledger Technology (DLT) involves core concepts like assets, ledgers, transactions, states, conditions, and inferences. It also includes distributed ledgers, cryptographic hash functions, construction of a blockchain, consensus mechanisms like proof of work, and examples of applications s
0 views • 27 slides
The FAIR Principles for Data Management and Stewardship
Embrace the FAIR principles - Findable, Accessible, Interoperable, Re-usable - for effective scientific data management and stewardship. Learn how annotations enhance data FAIRness and the key attributes of each principle. Dive into the high-level guiding principles that ensure data is globally uniq
0 views • 25 slides
Instrument Development in Mixed Methods Framework by Vanessa Scherman
Mixed methods research presented by Vanessa Scherman from the University of South Africa explores the development of instruments within a mixed methods framework. The content covers an overview of mixed methods, methodological norms, instrumental development, and closing the loop. It discusses the i
0 views • 40 slides
Interoperability for Provenance-aware Databases Using PROV and JSON
This research paper discusses the challenges in tracking database provenance and proposes a system, GProM, that computes provenance for database operations. It highlights the importance of exchanging provenance information between systems and the limitations of current relational database systems in
0 views • 28 slides
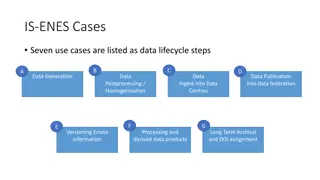
Challenges in Developing a Coherent Provenance Architecture
In the IS-ENES Cases, challenges arise in establishing a formal model for provenance architecture across various data lifecycle steps. The need for a coherent approach is emphasized to manage provenance information artifacts effectively. These challenges demand the creation of a structured framework
0 views • 11 slides
Evaluating Sources on Female Rule in the 1550s
This analysis focuses on assessing the reliability and usefulness of historical sources discussing the issue of female rule in the 1550s. It evaluates the content, provenance, and context of the sources to determine their relevance for historians studying the topic. The sources provide insights into
0 views • 8 slides
Managing Research Data Repositories for OCR-D
Research data repositories play a crucial role in the OCR-D framework, storing and managing data from document analysis processes. These repositories, like the Ground Truth (GT) repository, support FAIR principles by organizing findable, accessible, and retrievable data with metadata and provenance
0 views • 11 slides
Understanding Food Provenance and Consumer Awareness
Exploring the importance of food provenance, this article delves into how consumers can learn about the origins of their food and why traceability is crucial. Discover the significance of labels, consumer power, and the impact of imports and exports on the food industry. Gain insights into where our
0 views • 10 slides