NIH Data Management and Sharing Policy Overview
This content provides a detailed overview of the NIH Data Management and Sharing Policy, focusing on the importance of sharing scientific data, the scope of the policy, reasons for data sharing, application of the policy, and differences between Data Management Plans and Resource Sharing Plans. It a
2 views • 25 slides
Understanding the Economic and Health Impacts of Groundwater Nitrate Contamination in Nebraska
The economic and health costs of groundwater nitrate contamination in Nebraska highlight the challenges of ensuring safe drinking water. Despite largely safe levels, proactive strategies are essential due to rising nitrate levels and costly maintenance efforts. The compliance record shows progress i
0 views • 18 slides
Understanding the Importance of Data Sharing in Scientific Research
Data sharing plays a crucial role in scientific research to uphold transparency, reproducibility, and legitimacy. Skepticism of science due to fraud, publication bias, and challenges underscores the necessity for sharing confidential data. Professional associations, funding agencies, and journals ad
2 views • 39 slides
Bluetooth SIG September 2023 Update on Spectrum Sharing Plans
Bluetooth SIG provided an update on their actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. They aim to collaborate with the Wi-Fi industry to enable equitable sharing for Bluetooth, particularly focusing on the 6 GHz band. The overall plan includes forming
4 views • 8 slides
Supreme Court Raps SBI For Not Sharing Complete Data On Electoral Bonds
Supreme Court Raps SBI For Not Sharing \"Complete Data\" On Electoral Bonds\n\nThe Supreme Court today came down hard on the State Bank of India for not sharing the complete data on electoral bonds, a scheme that allowed individuals and businesses to donate anonymously to political parties. The cour
2 views • 4 slides
Early Detection and Proactive DPTL Activity Operating Procedures
Coordinated multi-disciplinary team efforts are crucial in preparing patients for discharge promptly to avoid prolonged hospital stays. Early detection and proactive DPTL activity focus on identifying potential discharge obstacles as soon as patients arrive in the emergency department. Various commo
5 views • 13 slides
Update on Bluetooth SIG's Spectrum Sharing Plans
This update discusses Bluetooth SIG's actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. It highlights the goals, the overall plan, recent actions, and collaboration with the Wi-Fi industry to enable equitable sharing of these bands. The detailed plan involve
0 views • 9 slides
Update on Bluetooth SIG's Plans for Spectrum Sharing in January 2024
Bluetooth SIG presents an update on their actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. Recognizing the need for future growth, they aim to collaborate with the Wi-Fi industry to develop optimal sharing mechanisms in the 6 GHz band. Their plan includes c
0 views • 11 slides
The Importance of Proactive IT Support in a Dynamic Business Environment
Don't wait for IT issues to cripple your business. Proactive IT support prevents problems, improves efficiency, and keeps your company agile. Learn how!
0 views • 5 slides
What Are The Benefits Of Proactive IT Support Versus Reactive It Support?
Stop IT headaches! Discover how proactive IT support prevents problems & saves you money compared to reactive fixes.
1 views • 5 slides
Protection of Extended TXOP Sharing in IEEE 802.11-23/1846r0
Reusing EHT's Triggered TXOP Sharing framework for extended TXOP sharing is discussed in this document, focusing on enabling sharing APs to distribute their obtained TXOP among other BSS(s). The document explores issues related to TXOP sharing for UHR STAs when a sharing AP allocates a portion of it
0 views • 12 slides
Understanding Market Sharing Cartel in Oligopolistic Markets
Market sharing cartels in oligopolistic markets involve firms entering agreements to share the market while retaining some autonomy in their operations. Two main methods are non-price competition and quota systems. Non-price competition involves firms agreeing on a common price to maintain profits w
0 views • 8 slides
Information Sharing Schemes and MARAM for Community Housing Organizations
These slides provide insights on information sharing schemes and the MARAM framework designed for community housing organizations to promote the wellbeing and safety of children, assess family violence risks, and enhance collaboration across service sectors. The Child Information Sharing Scheme (CIS
2 views • 15 slides
Enhancing Collaboration with User Stories Sharing Platform
Brief overview of a Jumpstart project involving a Sharing Platform prototype designed to address pain points related to transparency in sharing customer stories and feedback. User research insights and persona like Jane Smith, an Offering Manager, are highlighted to emphasize the need for an efficie
0 views • 26 slides
CNF-FSS and Its Applications: PKC 2022 March 08
Explore the Background, Applications, and Summary of CNF-FSS, focusing on Function Secret Sharing, Distributed Point Function, CNF Key-Sharing, and more. Learn about the efficiency of multiparty sharing and 1-out-of-3 CNF-FSS constructions for certain classes of functions. Discover how CNF Key-Shari
1 views • 33 slides
UVA Procedure for Managing Cost Sharing
The UVA Procedure for Managing Cost Sharing guides the handling of cost sharing at both proposal and award stages, ensuring compliance with sponsor requirements. It covers mandatory and voluntary cost sharing, tracking mechanisms, and third-party in-kind contributions, detailing the processes involv
0 views • 15 slides
Proactive Publication Strategies for Effective Public Communication
Proactive publication involves preemptively releasing information to shape public opinion and avoid reactive responses. Leveraging the internet for publishing is essential due to high accessibility and growing user numbers. The practice encompasses 15 categories of information dissemination, promoti
0 views • 14 slides
Coordinated AP Time/Frequency Sharing in IEEE 802.11be
The document discusses the concept of Coordinated AP (CAP) Time/Frequency Sharing within a Transmit Opportunity (TXOP) in the IEEE 802.11be standard. It explains the procedures of Frequency and Time resource sharing, highlighting the benefits such as latency improvement and throughput fairness. Deta
0 views • 16 slides
Understanding Market Sharing Cartels in Oligopolistic Markets
Perfect collusion in oligopolistic markets often involves market-sharing cartels, where member firms agree to share the market while allowing some degree of freedom in their decisions. This can be done through non-price competition or quota agreements. Non-price competition cartels involve setting a
8 views • 8 slides
Transforming Compliance and Culture in Housing Management
Change in culture is essential for proactive management in the housing sector, shifting from reactive to proactive approaches. Key recommendations include fostering a zero-tolerance culture, focusing on building maintenance, taking proactive responsibility, and empowering staff. The sector has respo
0 views • 7 slides
Enhancing Diversity and Productivity Through Job Sharing in the Insurance Sector
Advertising roles as open to flexible working, including job sharing, is crucial for attracting diverse talent and reducing the gender seniority gap in the insurance industry. Job sharing benefits both employees and employers, increasing productivity and well-being. Evidence suggests that job sharin
0 views • 9 slides
Reflections on Sharing: The Rhythm of Life Advent Journey
Explore the theme of sharing through a series of images and reflections. Discover the joy of sharing your gifts with others and embrace the practice of giving back each day. Join in today's challenge to spread kindness and love through simple acts. Say a prayer for guidance in learning the art of sh
0 views • 8 slides
Enhancing Information Sharing in Australian Meat Supply Chains
This research delves into the value of information and information sharing within the beef and sheep meat supply chains in Australia. It explores the benefits of improved decision-making, reduced costs, and enhanced supply chain performance through strategic information sharing. The study also ident
1 views • 21 slides
Exploring Secure Cooperative Sharing of Resources in Web Applications
This series of visual representations delves into the concept of secure cooperative sharing of JavaScript, browser capabilities, and physical resources in web applications. The images and descriptions cover topics such as web application security, browser functionality, and the principles of sharing
0 views • 22 slides
Unlocking the Benefits of Job Sharing: Insights and Strategies
Discover the advantages of job sharing through insights from Beth Chaudhary, Head of Smart Energy Policy at BEIS. Learn why job sharing works, the key elements of a successful job share partnership, and real-world examples of smart and flexible job sharing practices in various organizations. Explore
0 views • 7 slides
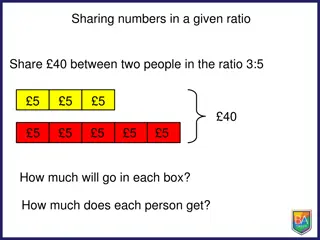
Ratio Sharing Practice Problems with Solutions
Solve various ratio sharing problems such as sharing numbers and sweets in given ratios between two people, finding equivalent ratios, and creating your own ratio sharing scenarios. Understand how to distribute quantities based on ratios and calculate each person's share accurately.
0 views • 9 slides
Determinants of Unlawful File Sharing: Insights and Implications
This comprehensive review delves into the determinants of unlawful file sharing behavior, exploring factors such as proximity to actual behavior, financial and legal considerations, and the impact on sales. It discusses the reasons behind illegal file sharing, including the influence of laws, pricin
0 views • 15 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Advanced Techniques in Secret Sharing Schemes
Explore the advancements in polynomial secret-sharing schemes and their applications in cryptography. Discover how polynomial schemes provide efficient solutions for sharing secrets among multiple parties while maintaining security. Learn about the construction of polynomial conditional disclosure p
0 views • 16 slides
Enhancing Information Sharing: DISC and PISA Benefits
DISC (Dorset Information Sharing Charter) and PISA (Personal Information Sharing Agreement) facilitate improved information sharing among healthcare organizations in Dorset. DISC establishes robust principles for managing data flow and promoting best practices in information governance, while PISA t
0 views • 8 slides
DiSC Dorset Information Sharing Charter Overview
The DiSC Dorset Information Sharing Charter, initiated by the Better Together programme, aims to improve information sharing for patients, residents, and service users in Dorset. It ensures a collaborative approach with an overarching governance and quality assurance structure. With over 100 members
0 views • 7 slides
Proactive Leadership and Quality Management Insights
Gain valuable insights into proactive leadership and quality management through visual representations and thought-provoking messages. Explore the concepts of being proactive, personal responsibility, and the power of choice in shaping your path to success. Learn to differentiate between reactive an
0 views • 20 slides
Secrets on Public Blockchain: Security and Efficiency
Exploring the challenges of maintaining secrecy on a public blockchain, this study emphasizes the importance of proactive secret-sharing protocols to safeguard sensitive information from adversaries while ensuring efficiency and scalability. The research delves into the complexities of keeping secre
0 views • 22 slides
IEEE 802 Spectrum Planning: Proactive Approach for Improved Spectrum Management
Exploring the need for proactive spectrum planning in IEEE 802 to better manage the complex process of meeting spectrum needs efficiently and effectively. Delving into the challenges of spectrum allocation, sharing, and optimization to ensure that standards have the RF spectrum necessary for their r
0 views • 9 slides
FlashPass: Proactive Congestion Control for Shallow-buffered WAN
FlashPass presents a proactive congestion control solution for shallow-buffered WAN, aiming to enhance network performance and achieve zero queueing, particularly in Enterprise WAN environments. The paper discusses the challenges of shallow-buffered WAN, the shortcomings of reactive congestion contr
0 views • 25 slides
Ministry Sharing Information Session Overview
Explore the benefits and options of Ministry Sharing, a collaborative approach for sharing resources and personnel among congregations. Discover how Ministry Sharing can enhance affordability, stability, and the range of resources available for pastoral care, sacraments, and meetings. Consider vario
0 views • 17 slides
Local Network and File Sharing Workshop Overview
Exploring the concepts of local area networks (LANs), intranets, and practical aspects of sharing files and printers on a network. The workshop delves into the structure of the University of Alkafeel network, including hotspot settings and ad hoc network configurations. Learn about USB printer shari
0 views • 30 slides
Impact of Remittances on International Risk Sharing
Higher remittances in Emerging Market/Developing Economies (EMDEs) between 1990-2018 positively impact risk sharing between consumption and income growth, unlike other types of capital flows. Remittances contribute significantly to enhancing risk-sharing effects, offering about 15% of risk sharing i
0 views • 12 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Password-Protected Secret Sharing for Enhanced Data Security
Exploring the concept of password-protected secret sharing, this content delves into Shamir's Secret Sharing, ElGamal Public Key Encryption, and the importance of securing sensitive information with robust schemes. It highlights the challenges of offline attacks, properties of secret sharing, and th
0 views • 22 slides