Exploring Power Dynamics in Mentoring and Coaching Relationships
This session delves into strategies for fostering effective mentoring and coaching relationships, emphasizing the importance of considering power dynamics, goal-setting, and fostering independence in proteges. Mentoring relationships are seen as socially constructed power dynamics that can advantage
5 views • 21 slides
Microsoft Dynamics 365 Online Training - Ax Technical D365
Dynamics 365 Online Training - Visual Path offers the Best D365 Ax Technical Online Training conducted by real-time experts.Our Dynamics 365 Online Training is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\n
5 views • 10 slides
Ax Technical D365 - Microsoft Dynamics 365 Online Training
Dynamics 365 Online Training - Visual Path offers the Best D365 Ax Technical Online Training conducted by real-time experts.Our Dynamics 365 Online Training is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\n
4 views • 3 slides
Dynamics 365 Online Training - Microsoft Dynamics AX Training
Dynamics 365 Online Training - Visual Path offers the Best D365 Ax Technical Online Training conducted by real-time experts.Our Dynamics 365 Online Training is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\n
4 views • 3 slides
Dynamics 365 Online Training - Microsoft Dynamics AX Training
Microsoft Dynamics AX Training - Visualpath offers the best Dynamics 365 Online Training delivered by experienced industry experts. Our training courses are delivered globally, with daily recordings and presentations available for later review. To book a free demo session, please call us at 91-9989
3 views • 4 slides
Exploring Quantum Black Holes: Dual Dynamics and Brane Evaporation
Exploring the dual dynamics of quantum black holes reveals new perspectives on black hole evaporation. By placing black holes on branes, we can study their classical picture in higher dimensions. This approach provides insights that were previously unattainable, leading to a better understanding of
1 views • 28 slides
Understanding Floods: Major Hazards and Disasters in Environmental Geography and Disaster Management
Floods, a common natural disaster, are often caused by factors like intense rainfall, river overflow, and human activities. Regions in India, such as Assam and Bihar, face significant loss due to recurrent floods. Factors like skewed rainfall patterns and transnational rivers contribute to the flood
0 views • 15 slides
Understanding Primary Clarifiers in Wastewater Treatment
Primary clarifiers are crucial components designed to remove particles with specific settling rates from wastewater. They come in rectangular and circular designs, each with typical dimensions and performance data for BOD and TSS removal. Understanding the design parameters like detention time, over
0 views • 15 slides
IEEE 802.11-20/1238r5 August 2020 Preamble Design Open Issues
In these slides, designs for U-SIG content & overflow and EHT-SIG design are proposed. The focus is on punctured channel indication design with the aim of conveying puncturing patterns efficiently while keeping signaling overhead low. The proposal includes a 6-bit field for puncturing information, a
1 views • 41 slides
Understanding the FLAGS Register in Assembly Language
An exploration of the FLAGS register in assembly language, highlighting the key status flags such as Carry Flag (CF), Parity Flag (PF), Auxiliary Carry Flag (AF), Zero Flag (ZF), Sign Flag (SF), and Overflow Flag (OF). These flags play a crucial role in reflecting the outcome of operations within th
0 views • 24 slides
Understanding Flag Registers in Microprocessor 8086
This content discusses the flag registers in the Microprocessor 8086, covering conditional flags such as Carry Flag (CF), Auxiliary Flag (AF), Parity Flag (PF), Zero Flag (ZF), Sign Flag (SF), and Overflow Flag (OF), as well as control flags including Trap Flag (TP), Interrupt Flag (IF), and Directi
1 views • 23 slides
IEEE 802.11-20/0029r3 Preamble Structure and SIG Contents Overview
The document dated January 2020 discusses the preamble structure and SIG contents, focusing on EHT-SIG in IEEE 802.11-20/0029r3 amendment. It covers the introduction of U-SIG, EHT-SIG format, EHT.PPDU types, and EHT-SIG design for MU PPDU. The discussion includes the necessity of accommodating overf
3 views • 22 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
IEEE 802.11-20/1238r1 Preamble Design Open Issues
Proposed designs addressing preamble design issues in IEEE 802.11-20/1238r1 include U-SIG content and overflow for Unified SU/MU PPDU, EHT-SIG design, and punctured channel indication. The focus is on conveying puncturing patterns efficiently while minimizing signaling overhead. The design features
5 views • 32 slides
Overview of 8086 Assembly Language Arithmetic Operations
The 8086 assembly language provides instructions for arithmetic operations such as addition, subtraction, and comparison. These operations are essential for manipulating data in memory and registers. The instructions support various operand types, including registers, memory locations, and immediate
0 views • 24 slides
Understanding Floods: Types, Causes, and Impacts
Floods are a natural hazard resulting from various factors like heavy rainfall, river bank overflow, or dam failure. They lead to land submergence and occur worldwide, causing significant economic losses. This article explores different types of floods, including precipitation and non-precipitation
1 views • 14 slides
Understanding Arithmetic Operations for Computers
The chapter delves into the fundamentals of arithmetic for computers, covering operations on integers, dealing with overflow, handling floating-point real numbers, and more. It explores addition, subtraction, multiplication, and division in detail, showcasing examples and techniques for efficient co
4 views • 18 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Microsoft Dynamics AX Training | Dynamics 365 Online Training
Dynamics 365 Online Training - Visual Path offers D365 Ax Technical Online Training conducted by real-time experts. Our Dynamics 365 Online Training is available in Hyderabad and is provided globally. For more info Contact us at 91-9989971070.\nVisi
5 views • 9 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Buffer Overflow: Understanding, Defenses, and Detection
Dive into the world of buffer overflow attacks with insights on understanding the concept, implementing defenses, and detecting stack smashing using techniques like canary values. Discover how to protect against vulnerabilities and grasp the significance of elements such as EIP, ASLR, DEP, and NX bi
0 views • 10 slides
Understanding Memory Layout in Computer Systems at Carnegie Mellon
Explore the memory layout in computer systems through the lens of Carnegie Mellon University's advanced topics in machine-level programming. Learn about buffer overflow vulnerability protection, memory allocation examples, x86-64 Linux memory layout, and addressing schemes. Dive into practical examp
2 views • 47 slides
Evolutionary Dynamics in Signaling Games and Strategies
Explore the intricate dynamics of signaling games and evolutionary strategies like Lewis signaling games, Hamilton Maynard Smith theories, and replicator dynamics. Witness the evolution of signaling strategies through simulations and understand the role of replicator dynamics in population interacti
1 views • 50 slides
Understanding Heap Overflow Attacks
A heap is a collection of variable-size memory chunks managed by the program. Heap overflow attacks occur when malicious actors corrupt heap memory, potentially allowing them to overwrite data and execute arbitrary code. This poses a significant security risk. The process involves manipulating heap
2 views • 19 slides
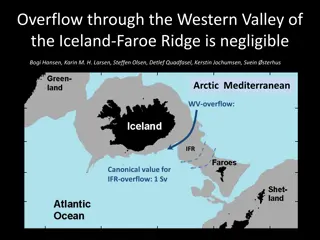
Insights on Overflow through the Western Valley of the Iceland-Faroe Ridge
Research by Bogi Hansen, Karin M. H. Larsen, Steffen Olsen, Detlef Quadfasel, Kerstin Jochumsen, and Svein Østerhus delves into the negligible overflow through the Western Valley of the Iceland-Faroe Ridge. Various field experiments and data analyses demonstrate minimal flow through the Western Val
0 views • 12 slides
Role of Sugar Industry in Circular Economy - Case Study on Spray Pond Overflow Treatment
The two-day summit organized by Mahatma Phule Krushi Vidhyapeet Krushi Mahavidhyalaya, Pune, in collaboration with various organizations, focused on the significant role of sugar and allied industries in promoting circular economy and sustainability. The event highlighted the necessity of treating s
0 views • 15 slides
Understanding Buffer Overflow in Computer Programming
This content delves into the intricacies of buffer overflow vulnerabilities in computer programming, showcasing real-world examples such as the Internet Worm and IM War incidents. It covers topics like stack buffer overflow exploits, Unix function implementations prone to buffer overflow, and the re
0 views • 35 slides
Dynamics 365 Licensing Summary and Transition Offers
Microsoft Dynamics 365 offers Enterprise and Business editions, unifying CRM, ERP, and financial applications. New customers can benefit from special transition offers when moving from Oracle, SAP, or Salesforce. Existing CRM Online and On-Premises customers have options to transition to Dynamics 36
0 views • 24 slides
Understanding Group Dynamics in Social Psychology
Group dynamics, as pioneered by Kurt Lewin, explores the intricate processes and influences within groups. It delves into group purpose, communication patterns, power dynamics, and member roles. The concept emphasizes how social forces impact group interactions and outcomes. From physical and non-ph
0 views • 51 slides
Smart Bathtub Vulnerabilities and Remote Control Risks
Explore the risks associated with a remote-controlled bathtub controlled via a smartphone app, including vulnerabilities in controlling water flow, water level sensing, and potential overflow scenarios. Learn how attackers could manipulate signals wirelessly and the likelihood of causing the bathtub
0 views • 38 slides
Understanding Buffer Overflow in C and C++ Programs
Buffer overflow is a common vulnerability in C and C++ programs where the allocated memory buffer is overwritten, causing unpredictable behavior. This vulnerability allows attackers to exploit the program by injecting malicious code. The lack of automatic bounds checking in these languages makes it
0 views • 6 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Understanding Conservation Principles in Fluid Dynamics and Classical Mechanics
Conservation principles play a significant role in fluid dynamics and classical mechanics. In fluid dynamics, conservation of mass, momentum, and energy are crucial for understanding fluid behavior. Classical mechanics, on the other hand, relies on Newton's laws to describe motion and energy conserv
0 views • 46 slides
Understanding Dynamics, Simulation, and Control in Klamp't
This document delves into the dynamics, simulation, and control aspects in Klamp't, covering key concepts, toolkit components, robot modeling, planning, 3D mathematics, and more. It explains how to perform forward/inverse dynamics, simulate rigid body physics, and emulate sensors. The content also d
0 views • 29 slides
Understanding Dependent and Relative Motion in Dynamics
Dependent Motion and Relative Motion are fundamental concepts in Dynamics, providing the foundation for future analysis. Dependent Motion involves constraints like ropes or cables, while Relative Motion considers observers in motion. Dynamics involves applying a limited set of equations in diverse w
0 views • 18 slides
MicroSoft Dynamics Ax Course | MicroSoft Dynamics Ax Training
\nVisualpath offers the best Microsoft Dynamics AX Technical Training worldwide. This Microsoft AX Training covers key technical aspects, providing hands-on experience with tools, development environments, and business logic essential for Dynamics AX
1 views • 11 slides