Building a Macrostructural Standalone Model for North Macedonia: Model Overview and Features
This project focuses on building a macrostructural standalone model for the economy of North Macedonia. The model layout includes a system overview, theory, functional forms, and features of the MFMSA_MKD. It covers various aspects such as the National Income Account, Fiscal Account, External Accoun
2 views • 23 slides
Analysis of "Valentine" by Carol Ann Duffy: Language, Structure, and Form
In "Valentine" by Carol Ann Duffy, the unconventional form with irregular stanzas and single-word lines creates a disjointed effect, emphasizing the forceful tone. The structure builds on the layers of an onion as a metaphor for love, gradually revealing the poem's meaning. The language uses an exte
3 views • 16 slides
NAMI Family Support Group Model Overview
This content provides an insightful introduction to the NAMI family support group model, emphasizing the importance of having a structured model to guide facilitators and participants in achieving successful support group interactions. It highlights the need for a model to prevent negative group dyn
6 views • 23 slides
Understanding Entity-Relationship Model in Database Systems
This article explores the Entity-Relationship (ER) model in database systems, covering topics like database design, ER model components, entities, attributes, key attributes, composite attributes, and multivalued attributes. The ER model provides a high-level data model to define data elements and r
0 views • 25 slides
Communication Models Overview
The Shannon-Weaver Model is based on the functioning of radio and telephone, with key parts being sender, channel, and receiver. It involves steps like information source, transmitter, channel, receiver, and destination. The model faces technical, semantic, and effectiveness problems. The Linear Mod
0 views • 8 slides
Understanding Security Onion: Network Security Monitoring Tools
Security Onion is a Linux distribution designed for network security monitoring using various tools like Full Packet Capture, Network IDS, Host IDS, and Analysis Tools. It offers capabilities for detecting and responding to security incidents effectively, making it a valuable asset for defensive net
1 views • 17 slides
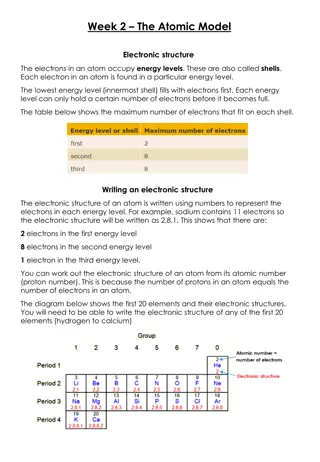
Understanding Atomic Structure: Electrons, Energy Levels, and Historical Models
The atomic model describes how electrons occupy energy levels or shells in an atom. These energy levels have specific capacities for electrons. The electronic structure of an atom is represented by numbers indicating electron distribution. Over time, scientists have developed atomic models based on
0 views • 5 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Understanding the OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
1 views • 41 slides
Regression Diagnostics for Model Evaluation
Regression diagnostics involve analyzing outlying observations, standardized residuals, model errors, and identifying influential cases to assess the quality of a regression model. This process helps in understanding the accuracy of the model predictions and identifying potential issues that may aff
1 views • 12 slides
Internationalization Strategies for European University Alliances: The Onion or The Spider Approach
Discussion on the onion model of internationalization of European University Alliances, focusing on the positioning of CLUSTER within the model, advocating policies in EHEA, forging relationships with CESAER, and expanding partnerships outside the EU. The presentation explores the use of associated
0 views • 6 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Analysis of Onion Routing Security and Adversary-based Metrics
In this comprehensive analysis, the security aspects of Onion Routing are scrutinized along with adversary-based metrics. Various security vulnerabilities such as compromised relays and potential attacks on the first and last routers are examined. Existing metrics like entropy coefficients and proba
0 views • 21 slides
Homemade Caramelised Onion Chutney Recipe
Learn how to make a delicious homemade caramelised onion chutney that's perfect to accompany a variety of dishes. This recipe combines onions, garlic, vinegar, sugar, and spices to create a tangy and sweet chutney that is great for curries, sandwiches, and cheese boards. Follow the simple steps to m
0 views • 8 slides
Understanding Onion Routing for Enhanced Privacy Protection
Explore the concept of onion routing for anonymous internet communication explained through images. Learn how users create circuits and exchange data through multiple routers to enhance privacy and security. Discover the intricate process step by step in a visual format.
0 views • 49 slides
Exploring Natural Dyes in Textile Wet Processing
Natural dyes, sourced from plants, minerals, and animals, have made a resurgence in textile dyeing due to environmental concerns. This online class covers the origin, classification, and characteristics of natural dyes such as Indigo, Indian Madder, Turmeric, Marigold, Henna, Tea, and Onion. Discove
0 views • 18 slides
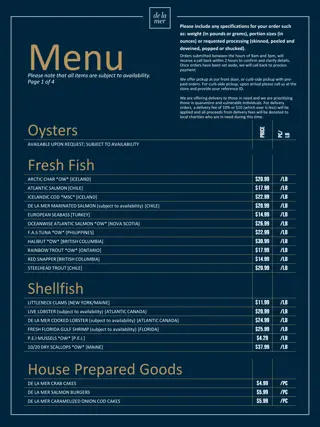
Fresh Seafood and House Prepared Goods Menu
Explore a variety of fresh seafood options such as Arctic Char, Atlantic Salmon, Icelandic Cod, European Seabass, and more. Indulge in shellfish like Littleneck Clams, Live Lobster, and P.E.I. Mussels. Additionally, enjoy house-prepared goods like Crab Cakes, Salmon Burgers, and Caramelized Onion Co
0 views • 4 slides
MFMSA_BIH Model Build Process Overview
This detailed process outlines the steps involved in preparing, building, and debugging a back-end programming model known as MFMSA_BIH. It covers activities such as data preparation, model building, equation estimation, assumption making, model compilation, and front-end adjustment. The iterative p
0 views • 10 slides
Proposal for Radio Controlled Model Aircraft Site Development
To establish a working relationship for the development of a site suitable for radio-controlled model aircraft use, the proposal suggests local land ownership with oversight from a responsible agency. Collins Model Aviators is proposed as the host club, offering site owner liability insurance throug
0 views • 20 slides
Homemade Buffalo Burgers Recipe with Macamore Ingredients
Make delicious homemade buffalo burgers using Macamore ingredients such as buffalo mince, eggs, breadcrumbs, Worcestershire sauce, and more. Follow a simple method to shape and cook the burgers, then garnish with your favorite toppings like ketchup, onion, and lettuce. A tasty meal awaits!
0 views • 6 slides
Delicious Buffalo Burgers Recipe with Irish Twist
A mouthwatering recipe for buffalo burgers with an Irish twist, featuring ingredients like buffalo mince, free-range eggs, Worcestershire sauce, and Wexford cheddar. The method includes shaping the burgers by hand and grilling them on a George Foreman or pan. Customize your burgers with garnishes li
0 views • 6 slides
UBU Performance Oversight Engagement Framework Overview
Providing an overview of the UBU Logic Model within the UBU Performance Oversight Engagement Framework, this session covers topics such as what a logic model is, best practice principles, getting started, components of the logic model, evidence & monitoring components, and next steps. The framework
0 views • 33 slides
Regression Model for Predicting Crew Size of Cruise Ships
A regression model was built to predict the number of crew members on cruise ships using potential predictor variables such as Age, Tonnage, Passenger Density, Cabins, and Length. The model showed high correlations among predictors, with Passengers and Cabins being particularly problematic. The full
0 views • 16 slides
Trust-Based Anonymous Communication Models and Routing Algorithms
This research paper discusses trust-based anonymous communication models and routing algorithms in the context of onion routing, emphasizing the importance of trust in mitigating security risks from adversaries with resources. The paper presents a model of trust and proposes trust-based routing algo
0 views • 65 slides
Exact Byzantine Consensus on Undirected Graphs: Local Broadcast Model
This research focuses on achieving exact Byzantine consensus on undirected graphs under the local broadcast model, where communication is synchronous with known underlying graphs. The model reduces the power of Byzantine nodes and imposes connectivity requirements. The algorithm involves flooding va
0 views • 7 slides
Emotions of Love and Conflicted Feelings: A Literary Analysis
The literary analysis delves into the themes of love and conflicted emotions through the use of oxymoron, simile, and evocative imagery. The words "beloved" and "sweetheart" juxtaposed with "bastard" showcase the thin line between love and hate, while the simile of onion's scent highlights the dual
0 views • 4 slides
Analysis of Carol Ann Duffy's Poem "Valentine" and its Themes
Explore the symbolism and themes in Carol Ann Duffy's poem "Valentine," where the comparison between an onion and love challenges traditional notions of romance. The poet's use of vivid imagery and language devices encourages readers to contemplate the complexities of relationships and the nature of
0 views • 21 slides
The Onion as a Metaphor for Love
The poem "Valentine" explores love through the metaphor of an onion. It challenges traditional romantic symbols by presenting an onion as a gift, symbolizing the complexity and layers of love. The poet delves into the themes of honesty, emotional depth, and the transient nature of relationships. Thr
0 views • 35 slides
Various Types of Stems in Plants - A Visual Guide
Culms, pseudostems, weak stems, and more - explore the diverse forms of plant stems such as jointed culms in bamboos, unbranched aerial shoots in onion and garlic, and creeping stems like runners and stolons. This visual guide showcases the unique characteristics of different plant stems with detail
0 views • 142 slides
Understanding the Tor Network: An In-Depth Overview
The Tor Network, developed in the mid-1990s, is a volunteer-based network that prioritizes privacy and security for Internet users through encryption and random pathways. By utilizing Onion Routing, Tor preserves anonymity but has limitations such as lack of application-level security and plugin usa
0 views • 13 slides
Easter Traditions in Slovenia: Celebrations, Recipes, and More
Easter in Slovenia is celebrated on April 17th with unique traditions like blessing painted eggs and feasting on ham and horse radish. Families attend church, hide Easter eggs, and enjoy time with loved ones. Slovenians color Easter eggs naturally using items like onion peels and spinach. A popular
0 views • 7 slides
Exploring Cellular Structures: Microscopic Examination of Onion Cells
Learn how to prepare a microscope slide with onion cells for observation. Follow step-by-step instructions, including cutting and peeling onion sections, staining cells with iodine, and using a coverslip. Additionally, understand how to calculate magnification in microscopy to determine actual cell
0 views • 7 slides
Traffic Analysis for Measuring Tor from Within
Study by Rob Jansen and team explores traffic analysis techniques to measure Tor from within the network, focusing on website and onion service fingerprinting. The research examines the limitations of entry positions and advantages of middle relays in fingerprinting attacks on Tor. By considering ad
0 views • 25 slides
Investigating the Effects of Salts on Onion Cell Structure
Investigate the impact of various salts on onion cell structure through a well-documented experiment. Assess strengths and weaknesses in theory, experiment setup, results, and conclusion.
0 views • 8 slides
Basva's Farm - A Visual Journey Through Onion Cultivation
Explore Basva's farm through a series of captivating images showcasing the process of onion cultivation, from tilling the soil to weeding and harvesting. Witness the meticulous care and hard work involved in growing onions, highlighting the importance of timely harvesting to prevent wastage.
0 views • 22 slides
Cell Observation Lab for Prokaryotic and Eukaryotic Cells
Explore the differences between prokaryotic and eukaryotic cells through a hands-on lab. Observe, sketch, and label organelles in bacteria (yogurt), protists (pond water), fungi (yeast), and plant cells (onion and anacharis). Learn to differentiate cellular structures and understand the characterist
0 views • 17 slides
Understanding Cultural Perspectives: The Iceberg, Onion, and Tree Models
Culture is multifaceted, encompassing visible elements like music and clothing as well as deeper values and beliefs. By exploring cultural models like the iceberg, onion, and tree, we can grasp the complexity of individuals and societies. Embracing diverse perspectives helps us navigate the intricac
0 views • 8 slides
Principles of Econometrics: Multiple Regression Model Overview
Explore the key concepts of the Multiple Regression Model, including model specification, parameter estimation, hypothesis testing, and goodness-of-fit measurements. Assumptions and properties of the model are discussed, highlighting the relationship between variables and the econometric model. Vari
1 views • 31 slides
Introduction to Light Microscopy: Structure, Function, and Operation
Light microscopy is a vital instrument used for studying small organisms or particles invisible to the naked eye. This lab exercise delves into the history, types, components, and operation of light microscopes, focusing on human cheek cells and onion cells. Explore the magnification and resolution
0 views • 17 slides
Shadow: Scalable and Deterministic Network Experimentation in Cybersecurity
The presentation discusses the concept of deterministic experimentation in cybersecurity, emphasizing the importance of experimental control and scalability in large distributed systems like Tor. It introduces Shadow, a network simulator designed to achieve repeatable and realistic experiments for r
0 views • 15 slides