Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Ask On Data for Efficient Data Wrangling in Data Engineering
In today's data-driven world, organizations rely on robust data engineering pipelines to collect, process, and analyze vast amounts of data efficiently. At the heart of these pipelines lies data wrangling, a critical process that involves cleaning, transforming, and preparing raw data for analysis.
2 views • 2 slides
Data Wrangling like Ask On Data Provides Accurate and Reliable Business Intelligence
In current data world, businesses thrive on their ability to harness and interpret vast amounts of data. This data, however, often comes in raw, unstructured forms, riddled with inconsistencies and errors. To transform this chaotic data into meaningful insights, organizations need robust data wrangl
0 views • 2 slides
Establishing Safety Standards in Non-Movement Areas at Smith Reynolds Airport
This guide outlines the purpose, definitions, rules, and safety measures for operating vehicles in non-movement areas at Smith Reynolds Airport. It emphasizes standardized ground movement practices to ensure the safety of airport patrons, reduce the risk of injury, and maintain a high level of safet
1 views • 12 slides
Understanding Non-Aqueous Solvents: Types and Classification
Inorganic non-aqueous solvents play a crucial role in chemical research and industry. This article by Dr. Princy K.G. delves into the classification of solvents based on protonicity, polarity, and aqueous vs. non-aqueous nature. It explores the types of non-aqueous solvents, such as protonic and non
1 views • 29 slides
Design and Analysis of Engineering Experiments in Practice
Explore the fundamentals of engineering experiments, including blocking and confounding systems for two-level factorials. Learn about replicated and unreplicated designs, the importance of blocking in a replicated design, ANOVA for blocked designs, and considerations for confounding in blocks. Dive
0 views • 15 slides
Approval and Validation Updates for NR MIMO OTA in 3GPP TSG-RAN.WG4 Meeting
The 3GPP TSG-RAN.WG4 Meeting discussed approval for the NR MIMO OTA workplan, addressed FR2 blocking issues, and emphasized the use of polarized antenna models. Updates were made to the power validation procedure and gNB beams usage criteria for FR1 MIMO OTA channel model validation. Collaboration w
1 views • 8 slides
Understanding Data Governance and Data Analytics in Information Management
Data Governance and Data Analytics play crucial roles in transforming data into knowledge and insights for generating positive impacts on various operational systems. They help bring together disparate datasets to glean valuable insights and wisdom to drive informed decision-making. Managing data ma
0 views • 8 slides
Understanding Non-Firm Quantities in Electricity Markets
Non-Firm Quantities in electricity markets involve units with non-firm access not being compensated for their non-firm capacity not getting accommodated on the system. The concept of Firm Access Quantity plays a key role in determining compensation levels for units, with differences in implementatio
0 views • 6 slides
Understanding Non-Compete Agreements: Enforceability and Requirements
Non-compete agreements are commonly used in the United States to protect businesses from competition by former employees. To be enforceable, these agreements must meet certain requirements, including independent consideration, protection of legitimate business interests, and reasonableness in scope,
0 views • 26 slides
Comparison of Trigger-based vs. Non-Trigger-based Sensing Measurement in IEEE 802.11
The document discusses the differences between Trigger-based (TB) and Non-Trigger-based (Non-TB) sensing measurement instances in IEEE 802.11 standards, focusing on who initiates the sensing measurement. TB sensing is initiated by the AP, while Non-TB sensing is initiated by a non-AP STA, enabling o
6 views • 13 slides
Mastering Front Line Blocking Techniques in Football
Learn the strategies and techniques involved in front line blocking for field goal and PAT attempts in football. Understand the importance of FG/PAT blocking, inside and outside block schemes, and specific drills for developing these skills. Explore detailed instructions on single, look off, and rev
0 views • 18 slides
ANEFO Meeting on Player Conduct: Rules and Regulations Summary
Eugene Borgonzi presented key rules and regulations regarding player conduct at the ANEFO Meeting on September 30, 2019. The sections covered include rules on assisting runners, illegal use of hands and holding, illegal blocking, and illegal personal contact. The detailed guidelines prohibit actions
1 views • 16 slides
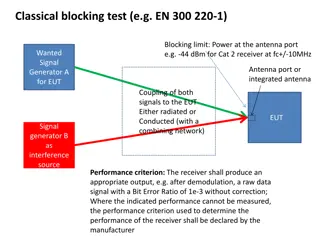
Classical Blocking Test and Receiver Performance Criteria
Classical blocking test procedures such as EN 300.220-1 outline limits on power at the antenna port for receivers, with criteria for achieving desired performance levels without errors. Manufacturers must declare appropriate performance criteria for devices, even if certain performance metrics are n
0 views • 6 slides
Understanding the Non-Blocking Michael Scott Queue
The Non-Blocking Michael Scott Queue, presented by Gurudatta Patil, is a thread-based data structure where threads help each other in managing a queue efficiently. Threads collaborate to add nodes at the tail and remove them from the head, ensuring smooth operation even in a non-empty queue scenario
0 views • 17 slides
Bi-Decomposition of Large Boolean Functions Using Blocking Edge Graphs
Bi-decomposition is a vital technique in logic synthesis for restructuring Boolean networks. This paper discusses the methodology of breaking down large Boolean functions using Blocking Edge Graphs (BEG) to simplify physical design and reduce complexity. The process involves constructing BEG, perfor
1 views • 29 slides
Hide Content from Bots in Shopify
Implement effective content hide content from Bots in Shopify strategies on your store from accessing sensitive information. To protect sensitive data and improve site security, make use of cutting-edge bot identification and blocking strategies. Ass
1 views • 6 slides
Understanding Data Collection and Analysis for Businesses
Explore the impact and role of data utilization in organizations through the investigation of data collection methods, data quality, decision-making processes, reliability of collection methods, factors affecting data quality, and privacy considerations. Two scenarios are presented: data collection
1 views • 24 slides
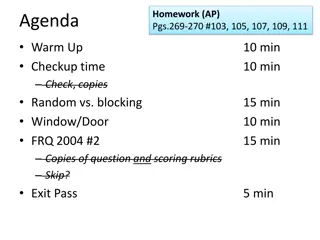
AP Statistics Homework Agenda and Experimental Design Example
In this AP Statistics homework agenda, students work on warm-up questions, checkups, and a controlled experiment design example involving paper airplanes and natural light impact on test scores. The agenda covers various topics such as confounding variables, random vs. blocking, and controlled exper
0 views • 15 slides
Exploring Real-World Concurrency Bugs in Go Programming Language
Golang, a programming language designed for efficient concurrency, utilizes lightweight threads called goroutines. This study delves into 171 Go concurrency bugs from various sources, analyzing root causes and fixing strategies. Highlighted results reveal insights for developers, pointing out that m
0 views • 36 slides
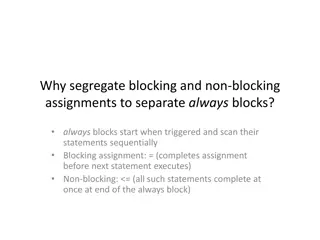
Understanding Blocking and Non-blocking Assignments in Verilog
Explore the intricacies of segregating blocking and non-blocking assignments to separate always blocks in Verilog. Learn about the differences between blocking and non-blocking assignments, their implications on sequential execution, and how to use them effectively in hardware description language p
0 views • 9 slides
Verilog FF Circuit Examples & Assignments Overview
Delve into Verilog FF circuit examples such as Gated D Latch and D Flip-Flop. Understand blocking and non-blocking assignments, their differences, and practical implications. Learn when to use each assignment method in Verilog design for combinational always blocks.
0 views • 17 slides
Chi: A Scalable and Programmable Control Plane for Distributed Stream Processing
Distributed stream processing systems are increasingly crucial for various production use cases, such as real-time dashboards, machine learning, and interactive debugging. The challenges of handling large variability in production ingestion workloads and high-degree data skew in queries are addresse
0 views • 20 slides
Youth Football: Finding the Right Backfield Qualities
Discover the essential qualities to look for in young football players for the backfield position: footwork, body language, toughness, blocking skills, mental resilience, and speed. Learn about common bad behaviors to correct and drills to enhance body language and footwork, as well as the importanc
0 views • 10 slides
Design and Analysis of Experiments in STAT 337 with Ruba Alyafi
Investigate the principles of experimental design, randomization, replication, and blocking in the context of STAT 337 with instructor Ruba Alyafi. Explore topics such as sampling distributions, point estimators, population inference, and more through practical applications and assignments. Dive int
0 views • 40 slides
Contemporary Challenges in Nuclear Disarmament and Non-Proliferation Regime
The international regime for nuclear disarmament and non-proliferation faces challenges from states within and outside the regime, as well as non-state actors. Various approaches are being utilized to address these challenges, including strengthening multilateral institutions, non-treaty-based multi
0 views • 12 slides
Improving Attainment and Progress of Disadvantaged Pupils in Sheffield
Attainment and progress of disadvantaged pupils in Sheffield show an improving trend across key stages, although the gaps between disadvantaged and non-disadvantaged students are not closing fast enough. Data suggests that disadvantaged pupils with low prior attainment are making better progress in
0 views • 29 slides
Efficient Handling of Cache Miss Rate in FPGAs
This study focuses on improving cache miss rate efficiency in FPGAs through the implementation of non-blocking caches and efficient Miss Status Holding Registers (MSHRs). By tracking more outstanding misses and utilizing memory-level parallelism, this approach proves to be more cost-effective than s
0 views • 44 slides
Pre-Operative Considerations for Equine Castration
Selection of a technique, common agents used to anaesthetize horses, scrubbing procedure, and blocking method are essential pre-operative considerations for equine castration. Closed and half-closed techniques decrease post-operative complications, while various agents can be used for sedation. Prop
0 views • 6 slides
Enhancing Flow Cytometry Practices for Accurate Data Analysis
Explore the realm of forensic flow cytometry with emphasis on improving data quality through proper titration and blocking techniques. Learn to identify and address common flow cytometry issues in various experimental cases to ensure reliable and reproducible results. Dive into practical rules and m
0 views • 39 slides
Protein Secondary Structure Prediction: Insights and Methods
Accurate prediction of protein secondary structure is crucial for understanding tertiary structure, predicting protein function, and classification. This prediction involves identifying key elements like alpha helices, beta sheets, turns, and loops. Various methods such as manual assignment by cryst
0 views • 30 slides
Understanding the Hierarchy of Protein Structure
To understand proteins' final shape and function, one must grasp the primary, secondary, tertiary, and quaternary structure levels. Proteins, composed of amino acids, fold into various shapes crucial for their roles such as signaling, catalysis, and structure. The primary structure represents the am
0 views • 28 slides
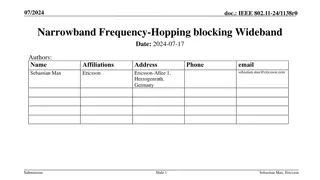
Analyzing Blocking Probability in Wideband Links with Narrowband Frequency Hopping
This document delves into the analysis of the likelihood of wideband link obstructions resulting from multiple active narrowband frequency hopping (NBFH) links. A dynamic Energy Detection Threshold (EDT) approach is suggested for mitigation. The study also explores scenarios involving single and mul
0 views • 18 slides
Prototyping for Forward CSTS Performance Analysis
Evaluation of the CSTS WG prototyping for enhancing forward frame service performance based on NASA reports, proposing frame blocking for increased throughput, and conducting measurements using specific set-up procedures. The objective is to optimize the CSTS FW Forward Specification for improved da
0 views • 21 slides
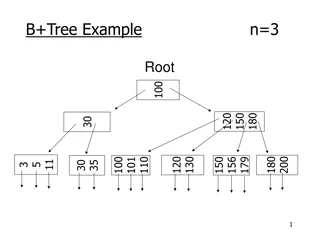
Understanding B+ Tree Data Structure
Explore the B+ tree data structure, its rules, insertion and deletion operations, node structure, and variations like the B-tree. Learn about maintaining balance, node sizes, and pointers in this efficient data structure designed for disk-based storage systems.
0 views • 15 slides
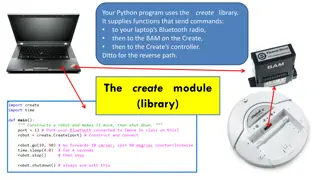
Python Create Library Overview
This Python program uses the Create library to send commands, enabling communication between your laptop's Bluetooth radio, the BAM on the Create robot, and the Create's controller. The library facilitates non-blocking commands for controlling the robot's movements and sensors, with specific instruc
0 views • 9 slides
Understanding CILK: An Efficient Multithreaded Runtime System
CILK is a multithreaded runtime system designed to develop dynamic, asynchronous, and concurrent programs efficiently. It utilizes a work-stealing thread scheduler and relies on a directed acyclic graph (DAG) model for computations. With a focus on optimizing critical paths and total work, CILK enab
0 views • 44 slides
Understanding Lock-Free and Wait-Free Algorithms in Concurrent Data Structures
Illustration of lock-free and wait-free algorithms compared to blocking algorithms, with insights on concurrent object execution, blocking vs. non-blocking algorithms, definitions, comparisons between locks, lock-free, and wait-free approaches, and explanations on making algorithms wait-free. Exampl
0 views • 23 slides
Hide Content from Bots in Shopify
Implement effective content hide content from Bots in Shopify strategies on your store from accessing sensitive information. To protect sensitive data and improve site security, make use of cutting-edge bot identification and blocking strategies. Ass
0 views • 6 slides
Selpercatinib 40 & 80 mg Tablets in India: For RET Fusion-Positive Cancers
Selpercatinib 40 & 80 mg tablets provide targeted treatment for RET fusion-positive cancers, effectively blocking RET mutations in cancers like non-small cell lung and thyroid cancer. Selpercatinib 40 & 80 mg in India, offers a specialized approach f
0 views • 1 slides