Navigating the Palo Alto PCSFE Certification:- Insights and Preparation
Begin Your Journey Here: https:\/\/bit.ly\/48vsKY9 - Dive deep into the PCSFE certification with our comprehensive guide to acing the Palo Alto Networks Certified Software Firewall Engineer exam. This resource is your one-stop destination for everything you need to know about the PCSFE exam, includi
4 views • 19 slides
How to Fix QuickBooks Error 12152?
How to Fix QuickBooks Error 12152?\nQuickBooks Error 12152 can be frustrating for users, disrupting workflow and causing delays in financial management. However, resolving this issue is manageable with a few steps. Firstly, ensure your internet connection is stable. Next, update QuickBooks to the la
2 views • 5 slides
Network Security Firewall Market Projected to Hit $16.2 Billion by 2030
The Network Security Firewall Market is projected to experience significant growth, with forecasts estimating it to reach $16.2 billion by 2030, growing at a compound annual growth rate (CAGR) of 19.7%\u200b (Meticulous Research)\u200b\u200b (Allied Market Research)\u200b.\n
0 views • 4 slides
Resolving the “QuickBooks Unable to Connect to Remote Server” Issue
Resolving the \u201cQuickBooks Unable to Connect to Remote Server\u201d Issue\n\nStruggling with the \"QuickBooks Unable to Connect to Remote Server\" issue can disrupt your workflow. However, resolving this problem is crucial to ensure seamless access to your financial data. To tackle this issue ef
1 views • 4 slides
How to Fix Quickbooks Error 80070057?
How to Fix Quickbooks Error 80070057?\nQuickBooks Error 80070057 can disrupt financial management. It occurs due to file extension issues or data damage. Symptoms include inability to open files and error code display. Causes involve incorrect file extensions or firewall settings. Diagnostic tools l
1 views • 5 slides
What to Do When QuickBooks POS Client Cannot Connect to Server_ A Comprehensive Guide
Struggling with QuickBooks POS client connectivity issues? Our comprehensive guide offers detailed steps to resolve problems when QuickBooks POS client cannot connect to the server. Learn how to check network connections, configure firewall settings, and verify server configurations to restore seaml
1 views • 3 slides
QuickBooks Multi-User Mode Not Working
QuickBooks in multi-user mode not working can cause significant disruptions in business operations. This issue prevents multiple users from accessing the company file simultaneously, leading to delays and reduced productivity. Common causes include network setup problems, firewall restrictions, or c
3 views • 4 slides
How to Fix QuickBooks Error Code 12031?
How to Fix QuickBooks Error Code 12031?\nQuickBooks Error Code 12031 disrupts operations due to internet connection issues or firewall settings. Troubleshoot by checking your internet connection, updating QuickBooks, configuring firewall settings, and adjusting Internet Explorer settings. Utilize Qu
0 views • 6 slides
The QuickBooks Error H202: How to Fix It?
The QuickBooks Error H202: How to Fix It?\nQuickBooks Error H202 occurs when QuickBooks can't connect to the server in multi-user mode. To fix this, start by checking your network connectivity and verifying that QuickBooks services are running. Use the QuickBooks Database Server Manager to scan your
3 views • 6 slides
Troubleshooting “QuickBooks Already Has a Company File Open” Error
Troubleshooting \u201cQuickBooks Already Has a Company File Open\u201d Error\nEncountering the \"QuickBooks Already Has a Company File Open\" error? This common issue disrupts your workflow but can be fixed. Start by checking for multiple instances of QuickBooks and restarting your computer. Ensure
1 views • 6 slides
How to Resolve QuickBooks Payroll Error Code 15223_ A Comprehensive Guide
Struggling with QuickBooks Payroll Error Code 15223? This guide provides a step-by-step approach to resolve it efficiently. Start by ensuring your QuickBooks software is updated to the latest version. Check your Internet Explorer settings, ensuring both SSL 2.0 and SSL 3.0 are enabled. Clear tempora
1 views • 5 slides
Network Security Firewall Market Expected to Expand to $16.2 Billion by 2030
According to latest analysis by Meticulous Research\u00ae, the global network security firewall market is poised to expand at a significant rate, reaching an estimated value of $16.2 billion by 2030.\n
0 views • 4 slides
Fixing the QBDBMGRN Error_ A Comprehensive Guide
The QuickBooks QBDBMGRN error is a common issue that users encounter when the QuickBooks Database Server Manager (QBDBSM) can't connect to the company file, hindering multi-user access. This error often arises after an update or due to firewall restrictions blocking communication. It can also occur
3 views • 5 slides
How to Resolve QuickBooks Update Error 12007
QuickBooks Update Error 12007? This error typically occurs due to misconfigured system files, internet connectivity issues, or problems with your firewall and security settings. When QuickBooks is unable to access the internet, it can't download updates, leading to Error 12007. To resolve this issue
0 views • 5 slides
How to Resolve QuickBooks Update Error 12007
QuickBooks Update Error 12007? This error typically occurs due to misconfigured system files, internet connectivity issues, or problems with your firewall and security settings. When QuickBooks is unable to access the internet, it can't download updates, leading to Error 12007. To resolve this issue
0 views • 5 slides
Important Updates: IT Directors Meeting July 2022 & Technology Migration
In the IT Directors Meeting July 2022, key updates were shared, including the migration of Cambium Assessment to Amazon Web Services (AWS) and changes in platform support for ChromeOS, Windows, and macOS. The meeting emphasized the need for updating firewall allowlists and proxy settings. Additional
0 views • 12 slides
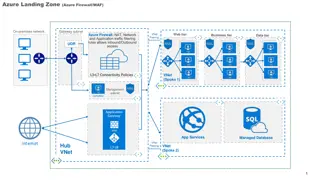
Azure Network Architecture Deployment Overview
An in-depth look at Azure network architectures, including landing zone configurations with Azure Firewall and WAF, deployment to primary Azure regions, hub and spoke models, network virtual appliances (NVAs), VPN tunnels, DMZ setups, and more. This comprehensive guide covers various network compone
3 views • 7 slides
Network Security Firewall Market
According to Meticulous Research\u00ae, the network security firewall market is projected to reach $16.2 billion by 2030, experiencing a robust CAGR of 19.7% from 2023 to 2030.
0 views • 4 slides
Understanding Forum, Firewall, and Fights in Foreign Courts
This legal overview delves into the jurisdiction and governing laws of Cayman Islands trusts, the enforcement of foreign judgments, and the application of firewall provisions to determine trust matters. It discusses the common law position, the implications of Section 90 of the Trusts Act, and elabo
0 views • 28 slides
Important Updates for Trustees - STEP Cayman Islands Branch Presentation
Walkers Bermuda, in association with Kevin Taylor, presented on legislative changes, interesting Cayman cases, CIMA guidance, and more for trustees at the STEP Cayman Islands Branch in May 2019. Topics included trust law amendments, private trust company regulations, and significant legal cases impa
1 views • 23 slides
Empowering Health Decisions and Care through OHDSI Community Collaboration
OHDSI's mission revolves around improving health by empowering a community to generate evidence that enhances health decisions and care. The journey to real-world evidence involves leveraging patient-level data in source systems and establishing reliable evidence. The OHDSI community is dedicated to
0 views • 5 slides
Evolution of Firewall-as-a-Service in OpenStack
The evolution of Firewall-as-a-Service (FWaaS) in OpenStack from version 1 to version 2 has seen significant improvements and refinements. The history of FWaaS, its refactor before the Tokyo summit, and the implementation of FWaaS v2 have all contributed to a more robust and feature-rich firewall se
1 views • 25 slides
Understanding DNS Firewall Architecture at Virginia Tech
Virginia Tech implements Response Policy Zone (RPZ) as a mechanism in the DNS system to protect clients from malicious domains. The RPZ allows recursive resolvers to customize responses for specific zones, enhancing security against malware callbacks. Working with campus partners, the RPZ database a
0 views • 11 slides
Setting Up Two-Factor Authentication for HRMS Access
Learn how to enhance HR system security by setting up two-factor authentication for off-campus access. This tutorial covers the importance of two-factor authentication, using your phone as a second layer of security, initial setup procedures through Wyoweb, requesting permission for HR self-service
0 views • 9 slides
Protecting Your Work Environment from Hacking Threats
Safeguarding your work environment from hacking is crucial to prevent potential losses. Addressing human errors, hacker infiltration, targeted phishing, and extortion are key steps to enhance security. Implementing measures like device security, two-factor authentication, firewall protection, and em
0 views • 8 slides
Re-evaluating Measurement Algorithms in Software Domain
This content explores the importance of measurement algorithms in software, focusing on network function virtualization (NFVs) and software switches. It discusses the critical role of measurement in decision-making for firewall, load balancing, and intrusion detection systems in managing NFVs. The n
0 views • 22 slides
Understanding PCI DSS Compliance in Nebraska
Learn about Payment Card Industry Data Security Standard (PCI DSS), its definitions, Nebraska's setup for ensuring cardholder data security, entities involved, requirements for compliance, and the roles of the PCI Security Standards Council. Discover the importance of maintaining firewall configurat
0 views • 19 slides
Protecting Your Business from Cybersecurity Threats
In today's digital landscape, the risk of cyber attacks is higher than ever. Hackers offer malicious services for a low cost, increasing the threat of ransomware, phishing, and spam attacks. With statistics showing the rise in ransomware incidents, it's crucial for organizations to prioritize securi
0 views • 24 slides
Step-by-Step Guide to Using secure.colostate.edu NetConnect
Accessing secure.colostate.edu NetConnect is crucial for connecting securely to Colostate's network. Follow these steps: Use your web browser to login, allow Juniper Network installation, access Secure.Colostate.edu, connect behind the firewall, and utilize Pangea for file access. Obtain the Pangea
0 views • 8 slides
Top 10 Security Features Your Website Needs in 2024
By implementing these top 10 security features, you can ensure that your website is prepared to face the challenges of 2024. Whether you need SSL certificates, firewall protection, or DDoS mitigation, it's essential to work with a trusted web develop
0 views • 6 slides
Top 10 Security Features Your Website Needs in 2024
By implementing these top 10 security features, you can ensure that your website is prepared to face the challenges of 2024. Whether you need SSL certificates, firewall protection, or DDoS mitigation, it's essential to work with a trusted web develop
0 views • 6 slides
Proactive Network Protection Through DNS Security Insights
Exploring proactive network protection methods using DNS, security challenges, botnet threats, firewall management, malware controls, and DNS-based malware control. Discussions on DNS security vulnerabilities, DNSSEC, threat intelligence, machine learning, and best practices like RPZ for DNS protect
0 views • 29 slides
Essential Tips for Computer Security
Protecting your computer is crucial in today's digital world. Follow these steps to enhance your computer's security: 1. Utilize a firewall to block hackers. 2. Install and update anti-malware software. 3. Create strong, unique passwords. By implementing these measures, you can safeguard your system
0 views • 4 slides
Evolution of the Internet: A Visual Journey Through Web Technologies
Explore the rich history of the internet through key technologies such as HyperText System, Gopher, Lynx, Mosaic, Netscape, Web Servers, Client-Server model, Web Hosting, Domain Name Registration, DNS Records, HTML, Firewall, HTML5 & JavaScript, and more. From early browsers to modern coding languag
0 views • 34 slides
Understanding IPv6 ISP Performance: A Detailed Analysis by Geoff Huston
This comprehensive study explores the reliability and speed of IPv6 connections, highlighting factors affecting connection failures. It compares datasets from 2011 and 2015/2016, revealing insights on Teredo, 6to4, and unicast address failures. The findings underscore the importance of addressing is
0 views • 37 slides
Effective DGA Family Classification using Hybrid Inspection Technique on P4 Switches
Attackers utilize Domain Generation Algorithms (DGAs) as dynamic communication methods in malware like botnets and ransomware to evade firewall controls. This study presents a novel approach that combines shallow and deep packet inspection on P4 Programmable Switches for efficient classification of
0 views • 19 slides
State Machine Abstraction for Dynamic Network Actions in SDN
State machines are proposed as a new switch primitive in Software-Defined Networking (SDN) to facilitate dynamic actions at switches. This approach eliminates the need for a priori knowledge, reduces delays, and enables local state-based policies such as stateful firewall, FTP monitoring, and large
0 views • 6 slides
Network Security Firewall Market
Expected to grow to $19.8 billion by 2031, the Network Security Firewall Market is projected to expand at a CAGR of 20.6% from 2024, supported by the momentum of digital transformation and cybersecurity trends.\n
0 views • 4 slides
Network Security Firewall Market
The Network Security Firewall Market, benefiting from digital innovation and increasing cybersecurity focus, is projected to grow to $19.8 billion by 2031, at a CAGR of 20.6% beginning in 2024.\n
0 views • 4 slides
Importance of Logging and Auditing in Cybersecurity
Discussing the significance of logging and auditing in cybersecurity, emphasizing the need for both a priori and a posteriori techniques to prevent security violations. Logging helps record events for system analysis, while auditing involves analyzing log records to provide understandable system inf
0 views • 32 slides