Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
1 views • 37 slides
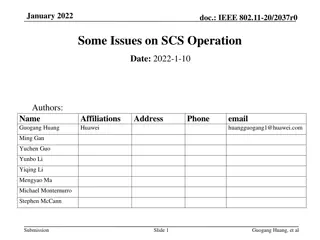
Issues with SCS Operation in IEEE 802.11be Standard
The document discusses technical issues related to the SCS (Spatial Channel Sharing) operation in the IEEE 802.11be standard. It highlights inconsistencies in the standard regarding parameterized QoS requirements, mixing of traffic streams with different QoS needs, and challenges in prioritizing SCS
0 views • 15 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Victorian Public Sector Nurses and Midwives Enterprise Agreement 2020-2024 Overview
The agreement covers translation of employees to a revised grading structure while maintaining salary, with streams including Clinical, Advanced Practice, Research, Quality, Governance, Community, and Nurse/Midwife Management. The change involves adjusting bed capacity and categorizing roles to 8A,
0 views • 31 slides
Jet Streams in Geography: A Comprehensive Overview
Jet streams are strong, high-altitude air currents that flow in a narrow belt in the upper troposphere, influencing weather patterns and aviation. Discovered during World War II, jet streams have distinct properties, types, and an index cycle that affects atmospheric circulation globally.
2 views • 11 slides
Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Waste Management Priorities in Solomon Islands
The presentation by Debra Kereseka at the PACWASTEPLUS Steering Committee Meeting highlighted key waste management priorities in the Solomon Islands. Topics covered include the management of different waste streams, challenges faced, and clarifications for the project management unit. Priorities inc
0 views • 7 slides
Data Flows and Network Challenges in Particle Physics Infrastructure
This overview delves into the data flows and network challenges faced in particle physics infrastructure, focusing on the JUNO project. It discusses the process of data reception, storage, and replication across various data centers, highlighting the bidirectional nature of data flows. Additionally,
0 views • 24 slides
Network Security: Hijacking, Denial of Service, and IDS
This content delves into the concepts of spying and hijacking in network security, covering topics such as eavesdropping on packets, injecting packets into streams, denial of service attacks, and defense mechanisms like firewalls and IDS. It explores low-level attacks and defenses, including ARP cac
1 views • 81 slides
Integrating IoT Data Streams into Business Analytics Software for Enhanced Insights
Are you prepared to elevate raw data to become your ultimate strategic advantage? Immerse yourself in the realm of IoT integration through our newest blog, revealing how effortlessly merging IoT data streams with business analytics software can trans
1 views • 7 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Advanced Techniques for Heavy Hitters Detection in Insertion Streams
Beating CountSketch algorithms, like those presented by David P. Woodruff and team, offer innovative solutions for identifying heavy hitters in insertion streams with minimal space complexity. Guarantees such as L1 and L2 outputs and the CountSketch approach are explored to achieve efficient heavy h
0 views • 18 slides
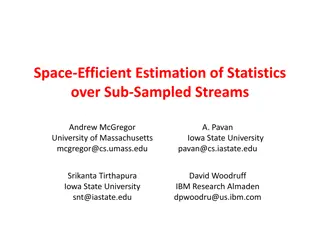
Space-Efficient Estimation of Statistics Over Sub-Sampled Streams
This research focuses on efficiently estimating statistics over sub-sampled streams, particularly in the context of IP packet streams for traffic monitoring. Various types of sampling methods are explored, such as Bernoulli sampling, to compute key metrics like frequency moments, number of distinct
0 views • 22 slides
Introduction to Network Analysis Using .NET
This presentation introduces the concept of network analysis using .NET in the humanities classroom. It provides a template for teaching and adapting network analysis tools for educational purposes. The guide explains the relevance of networks in processing and visualizing data, emphasizing the coll
0 views • 20 slides
The Fundamentals of Synoptic Meteorology at Mustansiriya University
Dive into the course of Synoptic Meteorology offered at Mustansiriya University with topics covering atmospheric motion scales, weather maps, air masses, fronts, and jet streams. Learn how to analyze and interpret weather data through the study of high and low-pressure systems, jet streams, and more
0 views • 17 slides
Monitoring Streams: A New Class of Data Management Applications
Explore the challenges in implementing monitoring applications within traditional database management systems and the introduction of the Aurora prototype system designed to enhance support for monitoring applications by handling continuous data streams efficiently. The paper delves into the motivat
0 views • 57 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
C++ Streams and I/O Operations
C++ streams play a crucial role in handling input/output operations by linking logical devices to physical ones. They provide a uniform interface for programmers to work with various devices efficiently. This article covers the basics of C++ streams, input/output streams, common functionalities like
0 views • 17 slides
LD-Sketch: Distributed Sketching Design for Anomaly Detection in Network Data Streams
LD-Sketch is a novel distributed sketching design for accurate and scalable anomaly detection in network data streams, addressing challenges such as tracking heavy keys in real-time across a vast key space. By combining high accuracy, speed, and low space complexity, LD-Sketch enables efficient heav
0 views • 25 slides
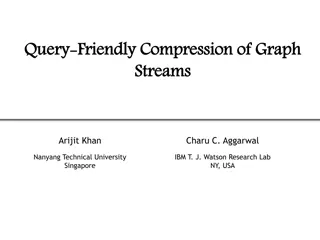
Challenges in Querying Graph Streams for Friendly Compression
Graph streams pose challenges in querying due to trade-offs among space, accuracy, and efficiency. The need to balance space and accuracy while maintaining throughput presents obstacles in constructing summaries and incorporating incremental updates. Additional challenges include query expressibilit
0 views • 28 slides
PDS4 Core Concepts
Delve into the intricate world of PDS4 Core Concepts, exploring data formats, arrays, tables, interleaving, parsing byte streams, encoding byte streams, and the meticulous structuring of documents, data geometry, and calibration within the PDS4 framework. Discover the principles governing the storag
0 views • 50 slides
Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
2 views • 31 slides
Analysis of MIMO for IMMW Transmission in IEEE 802.11-24
Proposal discusses the suitability of MIMO for IMMW transmission under different scenarios. The analysis focuses on the number of spatial streams based on channel rank and quality, recommending dual-polarization for LOS paths supporting 2 spatial streams and spatial separation for larger devices sup
0 views • 16 slides
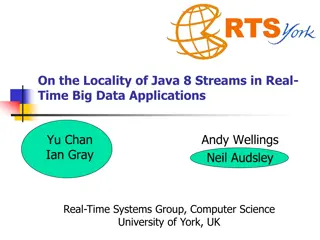
Locality of Java 8 Streams in Real-Time Big Data Applications
The study explores the impact of ccNUMA and locality on Java 8 Streams, focusing on their complexity and implementation in real-time Big Data applications. It discusses the Java support for server computers in clusters, the use of streams for programming models, and considerations for extending stre
0 views • 22 slides
WebRTC: Features, History, and Main APIs
WebRTC, a technology enabling real-time communication over the web, aims to facilitate acquiring audio and video streams, communicating data, and integrating RTC with other services. Originating in corporate environments with expensive licenses, WebRTC was championed by Google and standardized by IE
0 views • 21 slides
SpreadSketch: Invertible Superspreader Detection in Network Data Streams
SpreadSketch introduces a fast and invertible sketch for detecting superspreaders in network data streams. It offers high processing speed, compact memory usage, and network-wide visibility of superspreaders. The sketch is theoretically analyzed for accuracy, space, and time complexity, showing supe
0 views • 31 slides
Parallel Processing in Computer Organization
Computers can be classified based on data and instruction streams, forming various types of structures. Parallel processing levels can be defined based on instruction and data stream categorization, proposed by Michael Flynn in 1972. The instruction cycle consists of steps needed for executing instr
0 views • 44 slides
Maximizing Throughput in IEEE 802.11 Networks Through Unequal Modulation Strategies
The documents discuss the benefits of using unequal modulation over spatial streams in IEEE 802.11 networks to enhance throughput. Unequal modulation allows for adapting modulation schemes based on Signal-to-Noise Ratio (SNR) conditions, optimizing MIMO gains and coding rates for each spatial stream
0 views • 10 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Overview of Parallel Processing Architectures
This comprehensive overview delves into the taxonomy of parallel processor architectures, including SISD, SIMD, MISD, and MIMD configurations. It explores the characteristics of each architecture type, such as single vs. multiple instruction streams and data streams. The images provided visually rep
0 views • 76 slides
Vehicle Rental Oz Data Analysis for Business Optimization
Vehicle Rental Oz, a large vehicle rental company with over 500 stores in Australia, aims to enhance business performance through detailed data analysis. By focusing on historical rental and sales data, revenue streams, and promotion revenue analysis, the company plans to optimize resource utilizati
0 views • 17 slides
New Algorithms for Heavy Hitters in Data Streams
This article discusses new algorithms for heavy hitters in data streams, addressing the challenge of identifying items with high occurrence frequency efficiently. It covers topics such as streaming models, guarantees for heavy hitters, optimal algorithms for different parameters, and the Misra-Gries
0 views • 37 slides
Flynn's Taxonomy: Classification of Computer Architectures
Michael Flynn's 1966 classification divides computer architectures into SISD, SIMD, MISD, and MIMD based on the number of instruction streams and data streams. SISD corresponds to traditional single-processor systems, SIMD involves multiple processors handling different data streams, MISD has multip
0 views • 10 slides
Publicly Verifiable Grouped Aggregation Queries on Outsourced Data Streams
Explore the challenges and solutions for publicly verifiable grouped aggregation queries on outsourced data streams, focusing on security, verification, and cloud computing. The research discusses how to handle large amounts of data using small memory components and emphasizes the importance of data
0 views • 34 slides
Neighbourhood Sampling for Local Properties on Graph Streams
The research explores neighbourhood sampling for local properties on graph streams, focusing on counting subgraphs within 1-neighbourhood of a vertex. It addresses the Triangle Counting Problem and explains the significance of counting triangles in various contexts such as social network analysis an
0 views • 29 slides
Introduction to Files and Streams in Programming
Understanding files and streams is essential in programming for storing and processing data. Files provide a permanent way to store information, and streams help in reading and writing data sequentially or in parts. Learn about different types of files, such as text and binary files, and how to work
0 views • 31 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides