WhatsApp Direct Message
With the greatest \"WhatsApp Direct Message\" app that we've brought to you, which allows users to message random numbers without needing to save them. While this feature may offer convenience for users who frequently communicate with unknown contacts.
8 views • 22 slides
INTEGRITY: A FACTOR FOR EQUALITY THROUGH INCLUSIVE POLICIES
In a global context of growing income inequality, the importance of integrity in fostering equality through inclusive policies is emphasized. The OECD works with Mexico to address issues of inequality, corruption, and declining trust in government, highlighting the need for integrity and competence
0 views • 17 slides
The Truth of Righteousness by Faith Message in Laodicean Context
Understanding the significance of righteousness by faith message is crucial for Christians, especially in today's Laodicean condition. The message emphasizes justification through faith in Christ, leading to obedience to God's commandments and holy living. Encouraging believers to seek righteousness
0 views • 35 slides
Craft the Best WhatsApp Business Greeting Message Guide.
Read about the WhatsApp Business greeting message: tips and best examples to craft the perfect WhatsApp Business greeting message.\n
0 views • 7 slides
An Easy Way to Craft a 2024 Quick Message
\"Creating a quick message that stands out in 2024 requires brevity, relevance, and personalization. Ensure the subject line is concise and grabs the reader's attention. Be sure to keep the message short, focusing on the recipient's needs or interests. Engagement can be enhanced with emojis and visu
1 views • 5 slides
Accessing Electronic Case Documents via mySocialSecurity Message Center
Learn how to access your electronic case documents through the mySocialSecurity Message Center. Follow these steps: sign in to mySocialSecurity, verify your cell phone number, enter the security code, agree to the terms, select messages, open the message, and click to view the PDF document. Retrieve
0 views • 8 slides
Guide to Using the EPR Message Centre for Electronic Patient Records
Learn how to efficiently navigate and utilize the Message Centre in the Electronic Patient Record (EPR) system for managing workflow, signing off letters, reviewing results, and handling notifications. Accessible through Cerner Millennium, the Message Centre allows healthcare providers to electronic
0 views • 45 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
3 views • 41 slides
Comprehensive Guide to Message Evaluation, Testing, and Provisioning System (MVPS)
Explore the Message Evaluation, Testing, and Provisioning System (MVPS) used by the Center for Surveillance, Epidemiology, and Laboratory Services. MVPS streamlines data collection, collaboration, and provision of timely and accurate data, enhancing public health goals. Learn about the Components of
2 views • 13 slides
Understanding Academic Integrity at the University of Manitoba
Explore the essential aspects of academic integrity, including its definition, importance for students, types of dishonesty, and expectations in a class setting. Discover why students should care about academic integrity, the various types of academic misconduct such as plagiarism and cheating, and
0 views • 28 slides
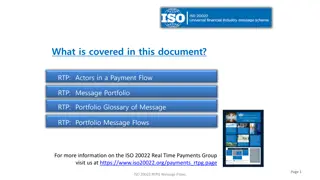
Real-Time Payments: Actors and Message Flows Overview
This document provides an overview of the actors involved in a payment flow and the message portfolio in Real-Time Payments (RTP). It includes details on various actors like Instructing agent, Forwarding agent, Ultimate Debtor, Reimbursement agents, and more. The provided message flows illustrate th
1 views • 12 slides
Understanding Integrity at Ok Tedi: Values and Practices
Ok Tedi's commitment to integrity is reflected in their values and operational practices. The organization emphasizes honesty, good moral principles, and accountability in all aspects of their work. Integrity is demonstrated through speaking the truth, maintaining safety, accurate reporting, and tre
0 views • 6 slides
Understanding Sender, Message, Receiver Correspondence in Communication Process
Communication process involves sender, message, and receiver elements. The sender initiates communication, generates a message, and conveys it to the receiver. The message is encoded, transmitted through a channel, and decoded by the receiver. Noise can hinder the communication process by interferin
1 views • 13 slides
Understanding Integrity Constraints in Relational Database Systems
Integrity constraints play a crucial role in maintaining the accuracy and integrity of data in a database. They include domain constraints, entity integrity, and referential integrity, each serving a specific purpose to ensure data consistency and reliability. Domain constraints ensure values in a c
1 views • 12 slides
Understanding Message Passing in Distributed Systems
Explore the key concepts of message passing in distributed systems, covering inter-process communication, desirable features like simplicity, efficiency, and reliability, different methods for information sharing, and the importance of synchronization and buffering. Dive into the intricacies of enco
0 views • 68 slides
Understanding Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Exploring Public Integrity and Ethics in Civil Service
This module on public integrity and ethics delves into key instruments for strengthening ethical practices in public organizations, challenges faced, analyzing codes of ethics, and managing integrity risks. The agenda includes activities like structured ethical reflection, understanding public value
1 views • 13 slides
Understanding Integrity: A Biblical Perspective
Explore the concept of integrity through the lens of biblical teachings, focusing on examples from the story of Solomon and David. Discover the meaning of integrity in Hebrew and how it relates to being complete, whole, and consistent in actions and words. Learn about subconscious ways integrity can
0 views • 17 slides
The Significance of Integrity and Honesty in Personal Skills
Understanding the meaning of integrity and how it relates to honesty is crucial for individuals to live ethically. This article delves into the importance of honesty and integrity, evaluating one's own level of honesty, and practical scenarios showcasing integrity in action.
0 views • 16 slides
Understanding the Impact of Message Creation on Communication Processes
The process of communication begins with creating a message, which can significantly influence how it is received. Messages, conveyed through words, signs, or sounds, are interpreted by receivers based on the sender's delivery. Littlejohn (2018) emphasizes the importance of how senders initiate comm
1 views • 9 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Implementing Your Budget & Message for Effective Media Partnership
This presentation delves into the crucial aspects of implementing a budget and crafting a message for effective collaboration with media partners. Learn how to strategize your spending across different outlets, work with media sales representatives to maximize audience reach, and identify the best t
0 views • 13 slides
Academic Integrity Policy at UIS - Guidelines and Procedures
The Academic Integrity Council at UIS ensures fair operation of hearing panels, reviews the policy implementation, and educates the community. It aims to protect the integrity of the academic environment and helps students develop integrity. Enforcement and effectiveness rely on faculty and departme
0 views • 14 slides
Understanding Message Passing Models in Computer Science
Message passing models in computer science involve concepts like producer-consumer problems, semaphores, and buffer management. This content explores various scenarios such as void producers and consumers, as well as the use of multiple semaphores. The functions of message passing are detailed, high
0 views • 50 slides
Academic Integrity Board Game Overview
Academic Integrity Board Game offers a fun and educational approach to understanding academic integrity. The game revolves around values like honesty, trust, fairness, respect, responsibility, and courage, as defined by the International Center for Academic Integrity. Players set up the board, place
0 views • 4 slides
Understanding Durability and Integrity in Data Storage Systems
Durability and integrity are crucial aspects of data storage systems. Durability ensures data survives faults like crashes and power loss, while integrity ensures data correctness in the face of faults. Disk data is durable due to surviving power loss, and has integrity through explicit and complex
0 views • 24 slides
Impact of Message Execution on Advertising Effectiveness
The impact of a message in advertising is not just about what is said, but also how it is said. Different cultures and ads have varying approaches, with some focusing on rational positioning while others appeal to emotions. The choice of headlines and copy can significantly influence the effectivene
0 views • 11 slides
Exploring the Concept of Integrity through Art and Quotes
Delve into the multifaceted theme of integrity through thought-provoking quotes, artistic interpretations, and personal reflections. Witness how individuals from diverse backgrounds define and exemplify integrity in their own lives. Join the journey to understand the significance of integrity and it
0 views • 8 slides
Enhancing Data Integrity in IEEE 802.11 Networks
This document discusses proposals for improving data integrity in IEEE 802.11 networks, specifically focusing on header protection for individually addressed data and management frames. It explores the challenges and alternatives related to verifying Message Integrity Check (MIC) before sending ackn
0 views • 20 slides
Early Church Message and Format in Acts of the Apostles: Kerygmata by C. H. Dodd
The early church's message and format in Acts of the Apostles, particularly focusing on the kerygmata as elucidated by C. H. Dodd, with references to Acts 2:14-39 and 3:12-26. Explore the challenges to the kerygmata and the adaptation of the Christian message to various audiences. Additionally, insi
0 views • 17 slides
Supervisor's Role in Guiding Students in Citizen Science and Business Projects
This module focuses on the critical role supervisors play in guiding students engaged in citizen science and business projects. It covers topics such as ethical challenges, academic integrity, and educational materials to support students and supervisors in their collaboration. The training plan inc
0 views • 6 slides
Practical Aspects of Modern Cryptography: November 2016
Exploring session-based protocols, SSL/TLS, certificates, and public key infrastructure, this presentation delves into the motivation behind secure online interactions, discussing the importance of verifying identities, ensuring data confidentiality, maintaining message integrity, and authenticating
0 views • 137 slides
IPC Lab 2 MessageQ Client/Server Example
This MessageQ example demonstrates the client/server pattern using SYS/BIOS heap for message pool, anonymous message queue, and return address implementation. The example involves two processors - HOST and DSP, where the DSP processor acts as the server creating a named message queue, and the HOST p
0 views • 12 slides
Understanding Message Passing Interface (MPI) Standardization
Message Passing Interface (MPI) standard is a specification guiding the development and use of message passing libraries for parallel programming. It focuses on practicality, portability, efficiency, and flexibility. MPI supports distributed memory, shared memory, and hybrid architectures, offering
0 views • 29 slides
Medicaid Integrity Institute 2012 Training Conference Overview
The Medicaid Integrity Institute (MII) provides training and technical assistance to state Medicaid program integrity employees at no cost. The institute, established in 2007 by CMS and the US Dept. of Justice, aims to enhance national program integrity standards. Located at the National Advocacy Ce
0 views • 8 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
Network Security: A Top-Down Approach Overview
This content delves into the fundamental principles of network security, covering topics such as cryptography, authentication, message integrity, and security measures at different network layers. It explores the concepts of confidentiality, authentication, message integrity, access, and availabilit
0 views • 66 slides
CC5212-1 Procesamiento Masivo de Datos Otoño 2016 Lab 2: Aidan Hogan's Message
In this lab project, Aidan Hogan provides instructions for accessing a code repository and implementing an instant messaging system. The steps include logging in, connecting to a directory, implementing message servers and apps, and setting up the command line to message peers. Detailed visuals acco
0 views • 24 slides
Practice Test for Developing Integrity in 4th Grade
This practice test by Renee Cook from Brownsburg, IN, focuses on developing integrity in 4th-grade students. The test includes scenarios where students have to choose the best action reflecting integrity. The test is designed like a dartboard, aiming to find the "bull's-eye" answer that aligns most
0 views • 18 slides





























![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245322/bulk-sms-providers-in-australia-august-2024-price-comparison.jpg)
![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245325/bulk-sms-providers-in-australia-august-2024-price-comparison-245325.jpg)


