WhatsApp Direct Message
With the greatest \"WhatsApp Direct Message\" app that we've brought to you, which allows users to message random numbers without needing to save them. While this feature may offer convenience for users who frequently communicate with unknown contacts.
8 views • 22 slides
Budget Execution Challenges in Somalia's Social Sectors
Addressing malnutrition in Somalia is hindered by low budget execution rates in the health and education sectors. Only a small portion of Official Development Assistance (ODA) is channeled through government systems, impacting service delivery and development financing. Donor-supported budgets for h
1 views • 32 slides
The Truth of Righteousness by Faith Message in Laodicean Context
Understanding the significance of righteousness by faith message is crucial for Christians, especially in today's Laodicean condition. The message emphasizes justification through faith in Christ, leading to obedience to God's commandments and holy living. Encouraging believers to seek righteousness
1 views • 35 slides
Craft the Best WhatsApp Business Greeting Message Guide.
Read about the WhatsApp Business greeting message: tips and best examples to craft the perfect WhatsApp Business greeting message.\n
0 views • 7 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
An Easy Way to Craft a 2024 Quick Message
\"Creating a quick message that stands out in 2024 requires brevity, relevance, and personalization. Ensure the subject line is concise and grabs the reader's attention. Be sure to keep the message short, focusing on the recipient's needs or interests. Engagement can be enhanced with emojis and visu
1 views • 5 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
1 views • 26 slides
Accessing Electronic Case Documents via mySocialSecurity Message Center
Learn how to access your electronic case documents through the mySocialSecurity Message Center. Follow these steps: sign in to mySocialSecurity, verify your cell phone number, enter the security code, agree to the terms, select messages, open the message, and click to view the PDF document. Retrieve
0 views • 8 slides
Advertising Campaign Planning and Execution
Dive into the world of advertising campaigns through insightful information on creative briefs, elements, DAGMAR approach, and budget factors. Learn about the critical role of the creative brief in guiding the message execution process, the objectives and steps of DAGMAR for setting advertising goal
1 views • 23 slides
Guide to Using the EPR Message Centre for Electronic Patient Records
Learn how to efficiently navigate and utilize the Message Centre in the Electronic Patient Record (EPR) system for managing workflow, signing off letters, reviewing results, and handling notifications. Accessible through Cerner Millennium, the Message Centre allows healthcare providers to electronic
1 views • 45 slides
Comprehensive Guide to Message Evaluation, Testing, and Provisioning System (MVPS)
Explore the Message Evaluation, Testing, and Provisioning System (MVPS) used by the Center for Surveillance, Epidemiology, and Laboratory Services. MVPS streamlines data collection, collaboration, and provision of timely and accurate data, enhancing public health goals. Learn about the Components of
2 views • 13 slides
The Neglected Provisions of Order XXI CPC, 1908
Explore the overlooked aspects of Order XXI CPC, 1908, focusing on the definitions, types of decrees, modes of execution, procedures for executing decrees, reasons for neglect, impact, recommendations, and conclusion. Learn about neglected provisions like summary execution, execution against legal r
0 views • 14 slides
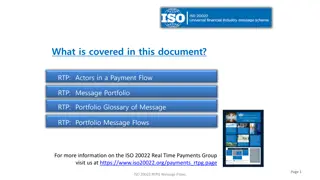
Real-Time Payments: Actors and Message Flows Overview
This document provides an overview of the actors involved in a payment flow and the message portfolio in Real-Time Payments (RTP). It includes details on various actors like Instructing agent, Forwarding agent, Ultimate Debtor, Reimbursement agents, and more. The provided message flows illustrate th
1 views • 12 slides
Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
Sender, Message, Receiver Correspondence in Communication Process
Communication process involves sender, message, and receiver elements. The sender initiates communication, generates a message, and conveys it to the receiver. The message is encoded, transmitted through a channel, and decoded by the receiver. Noise can hinder the communication process by interferin
1 views • 13 slides
HL7 Messaging in Healthcare Industry
Health Level 7 (HL7) is a standard for health-related messages used in systems like WebIZ. The training covers HL7 messaging overview, message formats, user settings, facility setup, and execution monitoring. Learn about data maintenance, incoming and outgoing messaging uses, and message formatting
1 views • 50 slides
Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
The Impact of Message Creation on Communication Processes
The process of communication begins with creating a message, which can significantly influence how it is received. Messages, conveyed through words, signs, or sounds, are interpreted by receivers based on the sender's delivery. Littlejohn (2018) emphasizes the importance of how senders initiate comm
1 views • 9 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Modes of Execution of Decree in Civil Law
The lecture discusses the various modes of execution of decree in civil law, such as execution against a person through arrest and detention, and execution against property. It explains the procedures involved in arrest and detention, including the conditions for release, restrictions on arrest, and
0 views • 9 slides
Java Memory Management
Explore how memory is managed in Java programs, including memory allocation for code, objects, and execution stack. Learn about memory areas like the execution stack and heap, and understand the concept of activation records in method execution.
0 views • 27 slides
Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Evolution of Execution Methods in Modern Society
Explore the historical and modern methods of execution, from hanging to lethal injection, and the transition towards more civilized approaches. Learn about the contributions of prominent figures like Elbridge Gerry in advocating for humane execution methods. Delve into the commercial rivalry between
0 views • 13 slides
Secure and Efficient Multi-Variant Execution in Distributed Settings
This paper discusses dMVX, a system for secure multi-variant execution in distributed settings to mitigate memory errors and protect against attacks. Using leader and follower variants, diversified program variants run in lockstep to ensure security. The system monitors and replicates I/O results, e
0 views • 35 slides
Introduction to Message Passing Interface (MPI) in IT Center
Message Passing Interface (MPI) is a crucial aspect of Information Technology Center training, focusing on communication and data movement among processes. This training covers MPI features, types of communication, basic MPI calls, and more. With an emphasis on MPI's role in synchronization, data mo
0 views • 29 slides
Hardware-Assisted Task Scheduler for OS Intensive Applications
A hardware-assisted task scheduler called SchedTask is proposed to address the issue of instruction cache pollution in OS intensive applications. By utilizing SuperFunction characterization and a specialized scheduler, the system aims to optimize task execution on different cores for improved perfor
0 views • 28 slides
Impact of Message Execution on Advertising Effectiveness
The impact of a message in advertising is not just about what is said, but also how it is said. Different cultures and ads have varying approaches, with some focusing on rational positioning while others appeal to emotions. The choice of headlines and copy can significantly influence the effectivene
0 views • 11 slides
Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
IPC Lab 2 MessageQ Client/Server Example
This MessageQ example demonstrates the client/server pattern using SYS/BIOS heap for message pool, anonymous message queue, and return address implementation. The example involves two processors - HOST and DSP, where the DSP processor acts as the server creating a named message queue, and the HOST p
0 views • 12 slides
Processes in Operating Systems - ECE344 Lecture 3 Summary
This lecture delves into the essential concepts of processes, threads, and synchronization in operating systems. Key topics covered include units of execution, representation of units of execution in the OS, process execution states, and state transitions. Users, programs, and the role of processes
0 views • 45 slides
InvisiSpec: Making Speculative Execution Invisible
InvisiSpec presents a novel defense mechanism to address speculative execution attacks in the cache hierarchy. By making speculative execution invisible to potential attackers, this holistic approach aims to mitigate the risks associated with exploiting side effects on incorrect paths, such as Spect
0 views • 18 slides
Multicycle Datapath and Execution Steps Overview
This content provides a detailed explanation of a multicycle datapath and the execution steps involved in processing instructions. It covers key elements such as instruction fetching, decoding, memory referencing, ALU operations, branch and jump instructions, as well as memory access for read and wr
0 views • 11 slides
Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Rethinking Processes with Threads in Operating Systems
Processes in operating systems traditionally include various resources and execution states, leading to inefficiencies in communication and parallel program execution. By separating the concept of a process from its execution state, modern OSes like Mac, Windows, and Unix introduce threads as lightw
0 views • 29 slides
Python Programming Essentials: Basics, Operators, Expressions, and Control Flow
This segment delves into the fundamentals of Python programming with a focus on essential concepts such as comments, numbers, strings, variables, arithmetic operators, logical operators, order of execution, expressions, and control flow statements like conditional execution and looping. Learn about
0 views • 12 slides
Operating System Concepts: Multiprogramming, Multiprocessing, Multitasking, and Multithreading
In the realm of operating systems, terms like multiprogramming, multiprocessing, multitasking, and multithreading can often be confusing due to their similar appearance but distinct meanings. These concepts play a crucial role in efficiently managing resources in a computing system, particularly in
0 views • 6 slides
Memory Allocation and Program Execution Overview
Understanding memory allocation is crucial for efficient program execution. This content delves into the importance of memory allocation, considerations for storing data during program execution, and the requirements for allocating memory efficiently. It also explores solutions for managing memory s
1 views • 35 slides
CPU Virtualization and Execution Control in Operating Systems
Explore the concepts of CPU virtualization, direct execution, and control mechanisms in operating systems illustrated through a series of descriptive images. Learn about efficient CPU virtualization techniques, managing restricted operations, system calls, and a limited direct execution protocol for
0 views • 18 slides