Inspectorate of Government Bi-Annual Performance Reports and Anti-Corruption Function Summary
The Inspectorate of Government in Uganda, led by the Inspector General Beti Kamya Turwomwe, presented bi-annual performance reports to Parliament for the periods January-June 2022, July-December 2022, and January-June 2023. The reports highlight the IG's mandate derived from the Constitution, focusi
1 views • 16 slides
Understanding Memory Allocation in Operating Systems
Memory allocation in operating systems involves fair distribution of physical memory among running processes. The memory management subsystem ensures each process gets its fair share. Shared virtual memory and the efficient use of resources like dynamic libraries contribute to better memory utilizat
1 views • 233 slides
Understanding Memory Organization in Computers
The memory unit is crucial in any digital computer for storing programs and data. It comprises main memory, auxiliary memory, and cache memory, each serving different roles in data storage and retrieval. Main memory directly communicates with the CPU, while cache memory enhances processing speed by
1 views • 37 slides
Understanding Memory Organization in Computers
Delve into the intricate world of memory organization within computer systems, exploring the vital role of memory units, cache memory, main memory, auxiliary memory, and the memory hierarchy. Learn about the different types of memory, such as sequential access memory and random access memory, and ho
0 views • 45 slides
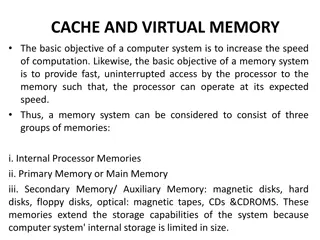
Understanding Cache and Virtual Memory in Computer Systems
A computer's memory system is crucial for ensuring fast and uninterrupted access to data by the processor. This system comprises internal processor memories, primary memory, and secondary memory such as hard drives. The utilization of cache memory helps bridge the speed gap between the CPU and main
1 views • 47 slides
Dynamic Memory Allocation in Computer Systems: An Overview
Dynamic memory allocation in computer systems involves the acquisition of virtual memory at runtime for data structures whose size is only known at runtime. This process is managed by dynamic memory allocators, such as malloc, to handle memory invisible to user code, application kernels, and virtual
0 views • 70 slides
Enhancing Anti-Corruption Activities in Extractive Sector Work Plans
Reflecting on anti-corruption activities in MSG work plans is crucial for good governance of oil, gas, and mineral resources. The EITI provides guidance on addressing corruption risks, with a recommended three-step approach: assess risks, develop an activity plan, and monitor results. Step 1 involve
0 views • 11 slides
Corruption and Anti-Corruption Measures in Latin America and the Caribbean
This research delves into the issue of corruption at the sub-national level in Latin America and the Caribbean, particularly focusing on the forest sector and the REDD+ program. It examines the vulnerable areas, corrupt practices, and lessons learned from case studies in Brazil and Bolivia. The stud
0 views • 28 slides
Understanding Memory Management in Operating Systems
Dive into the world of memory management in operating systems, covering topics such as virtual memory, page replacement algorithms, memory allocation, and more. Explore concepts like memory partitions, fixed partitions, memory allocation mechanisms, base and limit registers, and the trade-offs betwe
1 views • 110 slides
Role of EITI in Addressing Corruption in Extractive Sectors
The Extractive Industries Transparency Initiative (EITI) plays a crucial role in combating corruption in the oil, gas, and mineral sectors globally. By exposing vulnerable practices, providing contextual information, supporting citizen engagement, and advancing anti-corruption norms, EITI helps dete
0 views • 9 slides
Perceptions of Patron-Client Politics on Corruption in Papua New Guinea: A Research Proposal
Investigate the impact of patron-client politics on corruption in PNG to understand its effects on civil service and governance. Analyze traditional and modern systems to identify prevailing patronage types and their influence on corruption. The study aims to redefine corruption in the PNG context f
0 views • 24 slides
Global Incidents of Corruption: A New Index by Davide Furceri
Davide Furceri from the International Monetary Fund discusses the need for a new index of corruption, construction methodology, impact on the economy, and progress in measuring corruption. The presentation emphasizes the IMF's active role in combating corruption worldwide.
3 views • 32 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs accessing a common memory, leading to challenges like the cache coherence problem. This article delves into different types of shared memory architectures, such as UMA and NUMA, and explores the cache coherence issue and protocols. It also highlights
2 views • 27 slides
Strategies for Combating Academic Corruption in Higher Education
Corruption in higher education is a multifaceted issue that requires unbundling to effectively combat. Strategies include creating awareness, sharing resources, focusing on prevention over punishment, and implementing internal quality assurance systems. Actions within and outside higher education in
0 views • 6 slides
Understanding Memory Management and Swapping Techniques
Memory management involves techniques like swapping, memory allocation changes, memory compaction, and memory management with bitmaps. Swapping refers to bringing each process into memory entirely, running it for a while, then putting it back on the disk. Memory allocation can change as processes en
0 views • 17 slides
Understanding Corruption in India: Causes, Effects, and Solutions
Corruption in India is a significant issue affecting the economy and society at large. This article explores the definition of corruption, its prevalence in India, key causes, major players involved, comparison with global standings, and methods employed. Lack of effective management, inadequate ove
1 views • 18 slides
Understanding Memory Encoding and Retention Processes
Memory is the persistence of learning over time, involving encoding, storage, and retrieval of information. Measures of memory retention include recall, recognition, and relearning. Ebbinghaus' retention curve illustrates the relationship between practice and relearning. Psychologists use memory mod
0 views • 22 slides
Unpacking Self-Reinforcing Corruption Patterns
Delve into the complex dynamics of self-reinforcing corruption cycles and their implications for reform strategies. Explore how widespread corruption weakens deterrence, strengthens individual incentives for corruption, and impacts social norms against corrupt practices.
0 views • 45 slides
The Fight Against Corruption and African Myths in Review at TUEFA Conference
Prof. PLO Lumumba delivered a compelling speech addressing corruption and African myths at the TUEFA Conference in Nairobi. The presentation highlighted the cultural and colloquial definitions of corruption, emphasizing its widespread impact in Africa. The origins and causes of corruption in Africa
0 views • 23 slides
Corruption and Accountability in Food Aid Management
Corruption in humanitarian aid, particularly in the management of food aid commodities, deprives the most vulnerable of essential resources, hindering the noble goal of saving lives during crises. Examples from the Liberia-Sierra Leone refugee crisis shed light on the rampant corruption, where benef
0 views • 16 slides
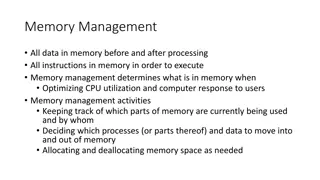
Understanding Memory Management in Computer Systems
Memory management in computer systems involves optimizing CPU utilization, managing data in memory before and after processing, allocating memory space efficiently, and keeping track of memory usage. It determines what is in memory, moves data in and out as needed, and involves caching at various le
1 views • 21 slides
Dynamic Memory Management Overview
Understanding dynamic memory management is crucial in programming to efficiently allocate and deallocate memory during runtime. The memory is divided into the stack and the heap, each serving specific purposes in storing local and dynamic data. Dynamic memory allocators organize the heap for efficie
0 views • 31 slides
Countering Violent Extremism Through Anti-Corruption in Eastern Africa
The project aims to pilot the impact of countering police corruption on radicalization and acts of violent extremism in Eastern Africa. By increasing internal anti-corruption oversight, empowering communities to report corruption effectively, and promoting collaboration between community, police, an
0 views • 17 slides
Understanding Memory Basics in Digital Systems
Dive into the world of digital memory systems with a focus on Random Access Memory (RAM), memory capacities, SI prefixes, logical models of memory, and example memory symbols. Learn about word sizes, addresses, data transfer, and capacity calculations to gain a comprehensive understanding of memory
1 views • 12 slides
Uncovering Corruption: Bridging the Pre/Modern Gap
Exploring the history of corruption across different eras, a research project delves into premodern and modern societies to understand the factors influencing corruption and strategies to combat it. Through workshops, presentations, and publications, the project aims to redefine success in governanc
0 views • 6 slides
Understanding Corruption, Governance, and Societal Norms
Alina Mungiu-Pippidi delves into the complexities of corruption, governance regimes, and societal norms, emphasizing the need to transform governance systems rather than just combat illegal corruption. She explores the concepts of corruption at the individual and societal levels, governance regimes,
0 views • 30 slides
Understanding Different Types of Memory Technologies in Computer Systems
Explore the realm of memory technologies with an overview of ROM, RAM, non-volatile memories, and programmable memory options. Delve into the intricacies of read-only memory, volatile vs. non-volatile memory, and the various types of memory dimensions. Gain insights into the workings of ROM, includi
0 views • 45 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
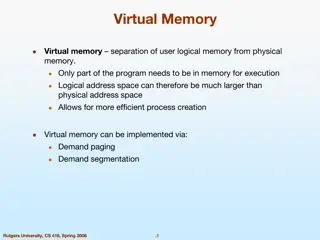
Understanding Virtual Memory Concepts and Benefits
Virtual Memory, instructed by Shmuel Wimer, separates logical memory from physical memory, enabling efficient utilization of memory resources. By using virtual memory, programs can run partially in memory, reducing constraints imposed by physical memory limitations. This also enhances CPU utilizatio
0 views • 41 slides
Understanding Virtual Memory and its Implementation
Virtual memory allows for the separation of user logical memory from physical memory, enabling efficient process creation and effective memory management. It helps overcome memory shortage issues by utilizing demand paging and segmentation techniques. Virtual memory mapping ensures only required par
0 views • 20 slides
Understanding Memory: Challenges and Improvement
Delve into the intricacies of memory with discussions on earliest and favorite memories, a memory challenge, how memory works, stages of memory, and tips to enhance memory recall. Explore the significance of memory and practical exercises for memory improvement.
0 views • 16 slides
Leveraging Big Data for Monitoring Corruption Risks in Development Aid Contracts
Explore insights on utilizing big data to enhance oversight and control corruption risks in development aid contracts, focusing on innovations in corruption measurement, data mobilization for development, and widening access to combat corruption. Understand corruption proxies, underlying data, and c
0 views • 47 slides
Understanding Memory Management in Programming
Memory management is a critical aspect of programming to prevent issues like memory leaks, use-after-free bugs, and memory corruption. Proper memory allocation and deallocation techniques can improve performance and avoid security vulnerabilities. Learn about heap storage, garbage collection, smart
0 views • 27 slides
Memory Management Principles in Operating Systems
Memory management in operating systems involves the allocation of memory resources among competing processes to optimize performance with minimal overhead. Techniques such as partitioning, paging, and segmentation are utilized, along with page table management and virtual memory tricks. The concept
0 views • 29 slides
Understanding the Prevention and Combating of Corrupt Activities Act (PRECCA)
The Prevention and Combating of Corrupt Activities Act (PRECCA) aims to prevent and combat corruption in both government and the private sector. It establishes measures to prevent corruption, defines various corrupt activities, and imposes obligations on individuals and entities to report corruption
0 views • 15 slides
Understanding Corruption and Competition in Botswana: Insights from Barney Rustle Masupe
Directorate on Corruption and Economic Crime (DCEC) in Botswana tackles corruption through investigation, prevention, and education. Corruption is defined as the misuse of public office for personal gain. Corrupt activities include soliciting, offering, or receiving valuable consideration. Barney Ru
0 views • 19 slides
International Anti-Corruption Frameworks and State Compliance
Scholarship on state compliance with international law and the impact of anti-corruption standards on domestic policies is growing, yet there is a lack of systematic studies on how states comply with and implement these standards. Various organizations and conventions focus on combating corruption a
0 views • 10 slides
Understanding Corruption and Its Implications on Institutions and Society
Corruption, as discussed by Jonathan Hopkin from the London School of Economics, is viewed through various lenses - from a reflection of traditional hierarchical ties in modernization theory to the inadequacy of political institutions. Economists highlight how corruption distorts market allocation.
0 views • 8 slides
Enhancing Memory Bandwidth with Transparent Memory Compression
This research focuses on enabling transparent memory compression for commodity memory systems to address the growing demand for memory bandwidth. By implementing hardware compression without relying on operating system support, the goal is to optimize memory capacity and bandwidth efficiently. The a
0 views • 34 slides
Locality-Aware Caching Policies for Hybrid Memories
Different memory technologies present unique strengths, and a hybrid memory system combining DRAM and PCM aims to leverage the best of both worlds. This research explores the challenge of data placement between these diverse memory devices, highlighting the use of row buffer locality as a key criter
0 views • 34 slides