How to Identify and Mitigate Cyber Threats
Learn how to identify and mitigate cyber threats, including malware and viruses. Understand the different types of malware and their impact on devices. Enhance your digital citizenship skills to protect yourself online.
2 views • 13 slides
Top Malware Protection Services in Dallas - Keep Your Business Safe
If you are searching for the best Malware Protection in Dallas, then you are in the right place. For all your Cyber Security needs look no further than Black Swan Cyber Security. As cyber threats continue to evolve, it is important to prevent the introduction of malicious code that can compromise th
2 views • 3 slides
How Does Antivirus Software Detect and Remove Malware?
In this PDF, We learn how antivirus software detects and removes malware through signature-based detection, heuristic analysis, behavioural monitoring, and sandboxing. VRS Technologies LLC offers the most strategic services of Antivirus installation Dubai. For More info Contact us: 056-7029840.
1 views • 2 slides
Understanding Entity-Relationship Model in Database Systems
This article explores the Entity-Relationship (ER) model in database systems, covering topics like database design, ER model components, entities, attributes, key attributes, composite attributes, and multivalued attributes. The ER model provides a high-level data model to define data elements and r
0 views • 25 slides
Understanding Malware: Types, Risks, and Prevention
Dive into the world of malware to explore major types such as viruses, worms, ransomware, and more. Learn about social engineering tactics, insider threats, and best practices to safeguard against malware attacks. Discover the malicious intent behind grayware and how to prevent malware infections ef
0 views • 23 slides
Corporate Account Takeover & Information Security Awareness Presentation
Discover the threat of Corporate Account Takeover, a growing electronic crime, where cybercriminals utilize malware to fraudulently access and transfer funds from corporate online banking accounts. Learn about malware, types of transactions targeted, and how criminals exploit victims through various
1 views • 25 slides
Information Security Tabletop Exercise: Malware & DDOS Attack
Conduct a tabletop exercise focused on a malware and DDOS attack scenario at your company. Explore incident response, decision-making, communication, and coordination among your crisis team. Enhance preparedness and identify gaps in your cybersecurity strategy to effectively mitigate threats. The ex
0 views • 21 slides
Understanding Malware Analysis with OllyDbg: A Practical Approach
Explore the fundamentals of malware analysis using OllyDbg, a user-mode debugger, for dynamic analysis. Learn how to dissect malicious code, analyze its behavior, and uncover hidden secrets within malware samples. Discover the powerful features of OllyDbg and its role in incident response and cybers
0 views • 17 slides
Understanding Entity-Relationship Modeling in Database Systems
Entity-Relationship (ER) modeling is a crucial aspect of designing database systems. It helps in defining data elements and relationships, presenting a conceptual view of the database structure. Entities, attributes, key attributes, composite attributes, and multivalued attributes play distinct role
1 views • 33 slides
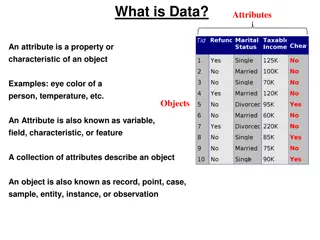
Understanding Data Attributes and Types for Analysis
Exploring the concept of data attributes, this information covers attributes as properties of objects, the distinction between experimental and observational data, types of attributes like qualitative and quantitative, and the properties of attribute values. It also delves into examples and categori
2 views • 32 slides
Understanding Malware: Types, Usage, and Protection
Malware, short for malicious software, encompasses various forms of hostile software designed to disrupt computer operation, steal sensitive information, or gain unauthorized access. It includes viruses, trojan horses, worms, spyware, phishing, ransomware, and more. Malware is often used to steal pe
1 views • 49 slides
Effective Antivirus Approaches and Malware Defense Strategies
Antivirus approaches play a crucial role in combating malware threats. Prevention is key, followed by detection, identification, and removal of viruses. Generic Decryption technology aids in detecting complex polymorphic viruses without causing any harm to the computer. CPU emulator, virus signature
1 views • 22 slides
Understanding Malware: Definitions and Types
Explore the diverse world of malware with definitions, categories, and examples such as self-replicating malware, population growth, parasitic malware, logic bombs, trojans, backdoors, viruses, and more. Gain insights into the characteristics and behaviors of different types of malware to enhance yo
0 views • 21 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Understanding DNS Firewall Architecture at Virginia Tech
Virginia Tech implements Response Policy Zone (RPZ) as a mechanism in the DNS system to protect clients from malicious domains. The RPZ allows recursive resolvers to customize responses for specific zones, enhancing security against malware callbacks. Working with campus partners, the RPZ database a
0 views • 11 slides
Comprehensive Malware Analysis Techniques
This detailed guide covers basic static techniques, malware analysis in virtual machines, and basic dynamic analysis. It includes information on static analysis, such as examining payloads without execution, file signatures, and signatures generated via analysis. Additionally, it delves into counter
0 views • 17 slides
Understanding Malware and Computer Security
Exploring the world of malware and computer security, this content delves into different types of malware such as Trojan horses, viruses, worms, and rootkits. It discusses how malware can violate site security policies and the covert actions they can carry out without detection. Examples like the Ge
0 views • 127 slides
Update of Medium- and Heavy-Duty Vehicle Attributes for Energy Commission Transportation Forecasting
This project aims to support the Energy Commission's transportation energy demand forecasting efforts by updating historic and forecast attributes of medium- and heavy-duty vehicles. Tasks include administration, review of past forecast attributes, updating historical vehicle attributes, forecasting
0 views • 12 slides
Mapping Project Overview and Attributes
This content provides detailed information about a mapping project involving the transition from S.S-53 to S-124, including complex and simple attributes, spatial references, and metadata. It covers aspects such as domain models, NAVWARN preamble, complex vs. simple attributes, and more. The content
0 views • 23 slides
Malware Dynamic Analysis Part 6 Overview
This content provides insights into Malware Dynamic Analysis Part 6 by Veronica Kovah. It covers actionable outputs like Yara and Snort, utilizing the open-source tool Yara to identify and classify malicious files based on patterns. The Yara signatures discussed include rules, identifiers, and condi
0 views • 25 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Understanding Theory and Association of Attributes
Attributes are studied under Theory of Attributes and Association of Attributes. Theory of Attributes covers basic concepts like statistics of variables, while Statistics of Attributes deals with qualitative data that can't be measured quantitatively. Conditions and classifications with reference to
0 views • 27 slides
Understanding Malware Execution and DLLs in IDA
Exploring how malware executes in IDA Pro, the significance of control flow graphs, DLL review, methods of utilizing DLLs for malicious activities, analyzing DLLs for code execution, and the management of processes in a secure environment. Gain insights into malware behaviors involving DLLs and proc
0 views • 27 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malware: Types, Risks, and Removal Methods
Explore the world of malware, including its various types and how it infiltrates systems. Discover the dangers it poses, such as data theft and system hijacking, and learn about manual removal techniques using tools like MBAM. Dive into hands-on labs to analyze, detect, and eliminate malware for a s
0 views • 15 slides
Understanding Malware Analysis Using Cuckoo Sandbox
Dive into the world of malware analysis with a focus on using Cuckoo Sandbox, an open-source automated system for analyzing various types of malicious files. Explore the process of setting up, customizing, and running analyses on different malware samples to generate actionable outputs. Learn how to
0 views • 22 slides
Context-Aware Malware Detection Using GANs in Signal Systems
This project focuses on detecting malware within signal/sensor systems using a Generative Adversarial Network (GAN) approach. By training on normal system behavior and generating fake malware-like samples, the system can effectively identify anomalies without relying on signature-based methods. The
0 views • 10 slides
Analyzing Android Applications for Malware Detection
Android applications have become a prime target for cybercriminals, leading to an increase in Android malware. The authors introduce a mobile sandbox for automated analysis of Android apps, combining both static and dynamic methods. Static analysis inspects downloaded apps and their source code, whi
1 views • 20 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
MapReduce Method for Malware Detection in Parallel Systems
This paper presents a system call analysis method using MapReduce for malware detection at the IEEE 17th International Conference on Parallel and Distributed Systems. It discusses detecting malware behavior, evaluation techniques, categories of malware, and approaches like signature-based and behavi
0 views • 22 slides
Evaluating Android Anti-malware Against Transformation Attacks
This study evaluates the effectiveness of Android anti-malware solutions against transformation attacks, focusing on the resistance to various types of malware obfuscations. It explores different transformations such as repacking, trivial changes, and sophisticated obfuscation techniques. Ten popula
0 views • 23 slides
Understanding Computer System Security Threats and Malware Types at Eshan College of Engineering
Explore the world of computer system security threats and malware at Eshan College of Engineering through insightful presentations prepared by Associate Professor H.K. Sharma from the CS Department. Learn about security threats like intrusion, phishing, spyware, spam, and malware categories such as
0 views • 13 slides
Exploring SMT Solvers for Malware Unpacking
In this informative content, we delve into the world of malware analysis, binary packers, and the challenges posed by obfuscation techniques. The article discusses tools like UPX and Themida, as well as the complexities of virtualization and handler obfuscation in unpacking malware. Understanding th
0 views • 24 slides
Analysis of Mixed-Mode Malware and Malware Analysis Tools
This analysis delves into mixed-mode malware, detailing its two phases and potential impact on malware analysis tools like TEMU. It explores scenarios where malware attacks analysis tools, emphasizing the challenges faced in observing and preventing malicious behavior. The study also highlights vari
0 views • 14 slides
Introduction to Malware Reverse Engineering
Explore the fundamentals of reverse engineering malware in this comprehensive guide for beginners. Covering topics like x86/64 ASM basics, setting up an environment, using debuggers, malware analysis techniques, and essential tools needed for the trade. Learn about the importance of software breakpo
0 views • 35 slides
Emerging Malware Threats in the COVID-19 Era
Malware researcher Ankit Anubhav discusses the challenges and evolving tactics in combatting malware threats during the COVID-19 era. Insights include remote work vulnerabilities, social engineering tactics, and recent malware techniques to stay vigilant against. The discussion covers specific attac
0 views • 11 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
Rise of Mobile Malware: A Historical Perspective
Explore the evolution of mobile malware from early instances like LibertyCrack in 2000 to more recent threats like DroidDream in 2011. Learn how malicious software has targeted mobile devices, such as Palm OS and Symbian phones, and understand the tactics used to infect and control these devices. Di
0 views • 38 slides
Understanding Entities and Relationships in Database Design
Explore the concepts of entities, entity sets, attributes, key attributes, single-valued and multi-valued attributes, derived attributes, as well as relationships and relationship sets in the context of database design. Gain insights into distinguishing between regular entities, weak entities, and e
0 views • 24 slides
Understanding DeepLocker Malware and AI-Embedded Attacks
Security researchers at Sevastopol State University have developed DeepLocker, a sophisticated malware that leverages artificial neural networks to conceal its activation conditions and evade detection. The malware utilizes deep neural networks to function, making it difficult to detect and analyze.
0 views • 13 slides