Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
adonai software
Adonai college Management System is a cloud-based ERP System that delivers various College and School Management Systems, College and School Management Software, College and School Management System ERP, College and School Management Software System, Online College and School Management Software Sys
3 views • 1 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Petrol Pump Software for Petrol Bunks
Do you want to promote your petrol pump business with an advanced software? Then Petrosoft is the best software solution to develop Petrol pump software to your business. We made this software by studying all kind of issues that petrol bunk owners face all over the world.\n PetroSoft, the best petro
1 views • 2 slides
Why Your Bureau Needs Payroll Software Now More Than Ever
Payroll software has become an integral part of modern businesses. The software\nautomates payroll processing and simplifies compliance with the HM Revenue and\nCustoms (HMRC) regulations in the United Kingdom (UK). The software reduces the\ntime and effort required for payroll processing, increases
6 views • 7 slides
Understanding Software: Types and Classifications
Software is a crucial component in computing, enabling users to execute tasks efficiently through programs. It is categorized into System Software and Application Software, with System Software managing hardware operations including Operating Systems, Device Drivers, and Firmware. Learn more about t
0 views • 12 slides
Enhance Productivity with HR and Payroll Software in UAE
Discover the best HR software in UAE tailored to streamline your HR and payroll processes. From HR attendance software to HR software for startups, explore top HR software companies offering comprehensive solutions for your business needs. Find free HR software for UAE and enhance your workforce man
2 views • 1 slides
Understanding Software Engineering: Concepts and Characteristics
Software engineering involves the application of scientific principles and methods to develop efficient, reliable software products. The need for software engineering arises due to factors like large software size, scalability, cost concerns, dynamic nature, and quality management. Good software exh
1 views • 25 slides
Aircraft Software Management and Control
Software management and control in aircraft systems are crucial for ensuring safe operations. This involves the classification of software based on criticality levels, certification requirements, and examples of software applications. Understanding the importance of following correct procedures for
0 views • 24 slides
Understanding Software Processes and Models
Software processes are structured activities essential for software system development, involving specification, design, validation, and evolution. Various process models and approaches like the Rational Unified Process and agile methods are discussed, highlighting the importance of adaptability in
1 views • 105 slides
Understanding Software Requirements and Design Principles
Software requirements play a crucial role in defining what a system should do, while the design describes how it achieves those goals. This lecture series covers the concepts of user and system requirements, techniques for describing system requirements, organizing software requirements in a documen
1 views • 30 slides
Understanding Software Processes and Models
This lecture discusses software processes, models, and activities involved in requirements engineering, software development, testing, and evolution. It covers topics such as process models, computer-aided software engineering (CASE) technology, software specification, design, validation, and evolut
1 views • 25 slides
Software Testing Training Course in Noida
Software testing is a crucial aspect of the software development lifecycle. It ensures the quality, reliability, and performance of software applications. With the increasing demand for high-quality software, the need for skilled software testers is
1 views • 9 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Understanding Requirements Analysis in Software Engineering
Requirements analysis is a crucial task in software engineering that bridges the gap between system engineering and software design. It involves specifying software's operational characteristics, interface with other system elements, and constraints it must meet. Through elicitation processes like m
9 views • 30 slides
Understanding Software Measurement and Metrics in Software Engineering
Software measurement plays a crucial role in assessing the size, quantity, and quality of software products and processes. It involves direct and indirect measurement methods to monitor and improve software quality, predict future outcomes, and manage project budgets and schedules. Software metrics
0 views • 8 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Software Cost Estimation in Software Engineering
Software cost estimation in software engineering involves predicting the resources required for a software development process. It includes fundamental estimation questions, software cost components, costing and pricing considerations, software pricing factors, and programmer productivity assessment
0 views • 30 slides
Understanding Computer Software and Operating Systems
Computer software, comprising system software and application software, plays a crucial role in managing computer resources and facilitating user instructions. System software consists of control programs, support programs, and development programs, while application software assists in specific tas
1 views • 26 slides
ATST Safety Review High-Level Software Overview
This document provides an overview of the high-level software components involved in the ATST Safety Review conducted on 26th January 2011. It includes details on the Telescope Software Control Systems, Observatory Software Control Systems, and Instrument Software Control Systems, along with respons
13 views • 15 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Understanding Software Engineering: An Overview by Lecturer Sebastian Coope
Explore the world of software engineering with Lecturer Sebastian Coope in this informative module introduction. Discover the importance of structured and disciplined approaches in making software, the challenges in software development, and the necessity of software engineering in handling complex
5 views • 37 slides
Software Construction and Evolution in CSSE 375: Overview
This course introduction in Software Construction and Evolution (CSSE 375) covers topics such as the nature of software, challenges in software evolution, software degradation, and the art of avoiding information loss due to relentless changes. The course aims to equip students with skills in softwa
0 views • 20 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Insights from NATO Software Engineering Conferences and The Software Crisis of the Seventies
Exploring the challenges faced in software engineering during the 1970s, including issues such as project delays, inefficiencies, and the critical need for reliable, high-quality software. Insights from the NATO Software Engineering Conferences shed light on the struggle to meet increasing modern so
0 views • 46 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
Software Bingo_ A Game-Changing Addition to Your Online Casino
Discover how software bingo, bingo game software, professional bingo software, software for bingo, pc bingo games software can enhance your online casino and boost player engagement.\n\nSource>>\/\/ \/bingo-software\n\n
0 views • 4 slides
Understanding the Essence of Software Development Process
Software is a vital component in today's technology-driven world. It consists of instructions, data structures, and descriptive information that enable the functioning of computer programs. Unlike hardware manufacturing, software development is an engineering process that undergoes changes and deter
0 views • 74 slides
Overview of Static Bug Detection in Software Quality Assurance
Static bug detection is a less popular but effective approach for software quality assurance compared to traditional testing methods. It involves tools like Findbugs that help identify potential issues in code before deployment, such as bad coding styles, null pointer dereferences, and malicious cod
0 views • 36 slides
Understanding Software Engineering Fundamentals
Explore the significance of software in modern economies, the attributes of good software, software engineering principles, software processes, and process models. Learn how software engineers ensure functionality, maintainability, dependability, efficiency, and usability in software development.
0 views • 25 slides
Understanding Software Engineering and Development Processes
Explore the key concepts of software engineering, including misconceptions, legacy software, and development phases. Learn about professional responsibilities, the need for software processes, the ETVX model, and different properties of software processes. Discover the components of software process
0 views • 57 slides
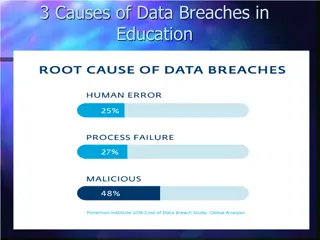
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides