Understanding IDS/IPS: Enhancing Security with SecurityGen's Advanced Solutions
In the realm of cybersecurity, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play pivotal roles in safeguarding networks against evolving threats. SecurityGen's IDS IPS solutions are designed to monitor network traffic, detect suspicious activities, and prevent potential i
4 views • 1 slides
Function Based Thinking
Function-based thinking in Missouri Schoolwide Positive Behavior Support, emphasizing data-based decision-making, mission clarity, and effective teaching practices. Understand how behavior is related to the environment and how environmental interventions play a key role in shaping expected behaviors
6 views • 27 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Addressing Predatory Behavior in the Fellowship
Predatory behavior, especially towards vulnerable members, is a concerning issue in the fellowship. This behavior includes unwelcome advances, exploitation of power dynamics, and institutional sexism. The discussion on predatory behavior necessitates honest dialogue and a united approach for a safer
3 views • 13 slides
Cyber Threat Detection and Network Security Strategies
Threat detection is crucial in analyzing security ecosystems to identify and neutralize malicious activities. Methods like leveraging threat intelligence, behavior analytics, setting intruder traps, and conducting threat hunts are essential for proactive security. Implementing security through obscu
1 views • 51 slides
Understanding Consumer Behavior in Marketing
The design of a marketing program starts with understanding consumer behavior. Consumers, as the end users, play a crucial role in shaping market trends. Producers seek insights into consumer personas, market behaviors, and influencing factors. Management focuses on the consequences of consumer beha
2 views • 26 slides
Understanding Psychology: The Science of Behavior and Mental Processes
Psychology is the scientific study of behavior and mental processes. Psychologists study both observable behavior and private mental processes. The primary goals of psychology are to describe, understand, predict, and control behavior. Different branches of psychology, such as applied psychology, cl
2 views • 29 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Understanding Inmate Behavior Management in Correctional Settings
Inmate Behavior Management in correctional facilities involves supervising inmates, implementing corrective discipline, and fostering a fair and consistent environment. It emphasizes the importance of behavior management plans, identifying undesirable traits in supervision, and passing educational a
0 views • 19 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Human Behavior: Foundations and Factors
Human behavior is a multifaceted subject influenced by genetic makeup, culture, and individual values. It encompasses both overt actions and covert thoughts, a product of the individual and environmental factors. Psychologists study behavior from visible (overt) actions like playing football to inne
0 views • 20 slides
Understanding Malware Analysis with OllyDbg: A Practical Approach
Explore the fundamentals of malware analysis using OllyDbg, a user-mode debugger, for dynamic analysis. Learn how to dissect malicious code, analyze its behavior, and uncover hidden secrets within malware samples. Discover the powerful features of OllyDbg and its role in incident response and cybers
0 views • 17 slides
Understanding Normal and Abnormal Behavior: Perspectives and Definitions
Normal behavior varies from person to person and society, influenced by individual preferences and societal norms. Abnormal behavior is characterized by an inability to function effectively or personal discomfort. The concept of normality and abnormality in psychology raises complex questions about
2 views • 8 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Understanding Human Behavior: Insights for Social Workers
This material delves into the intricacies of human behavior, exploring factors influencing behavior such as heredity, environment, intelligence, needs, and motives. It covers the concept of human behavior, stages in life from conception to old age, and theories of human development by eminent psycho
2 views • 71 slides
Understanding Animal Behavior and Ecology
Animal behavior encompasses a range of activities such as feeding, breeding, and social interactions. Ethology focuses on studying behavior in natural environments, while behavioral ecology examines ecological aspects like predator-prey interactions. Sociobiology delves into the evolution of social
3 views • 5 slides
Understanding Behavior Management in Classroom Settings
Explore the essential topics of behavior management, classroom strategies, and discipline in educational settings. Delve into the functions of behavior, impact of trauma on learning, and effective management techniques. Learn how to identify underlying reasons for student behaviors, discuss behavior
0 views • 76 slides
Secure and Trustworthy Cyberspace (SaTC) Program Overview
The Secure and Trustworthy Cyberspace (SaTC) Program, led by Program Director Sam Weber, aims to protect cyber systems from malicious behavior while upholding privacy and usability. It focuses on multidisciplinary approaches involving various disciplines like computer science, engineering, economics
0 views • 9 slides
DNS Forensics & Protection: Analyzing and Securing Network Traffic
DNS Forensics involves using DNS traffic to analyze network health, detect anomalous behavior, and combat malicious activities. By understanding DNS activity on systems and implementing defense strategies, users and network providers can enhance security and privacy.
0 views • 16 slides
Targeting Emotions to Facilitate Behavior Change in Older Adults
Efforts in changing health behavior have traditionally focused on social and cognitive factors, but recent evidence highlights the importance of affective states in decision-making and behavior change. Janey Peterson discusses the role of emotions in achieving and sustaining behavior change to benef
0 views • 11 slides
Securing Wi-Fi Access Points for Smartphone Applications
Explore the vulnerabilities of smartphone applications to attacks through dangerous Wi-Fi access points. Consider methods for accessing the internet on smartphones and the potential for malicious behavior. Recommendations are made for enhancing security to prevent backdoors and protect users from fr
0 views • 5 slides
Grading Criteria for Effort and Behavior in Educational Reporting
Effort and behavior in educational settings are evaluated based on criteria ranging from Excellent to Causing Concern. Pupils demonstrating excellent behavior show respect, responsibility, and positive engagement in learning. Those with good behavior exhibit cooperation and respect for others, albei
0 views • 9 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Understanding Applied Behavior Analysis (ABA) for Youth Interventions
Applied Behavior Analysis (ABA) is a science focusing on improving human behavior by increasing desired behaviors, teaching new skills, and generalizing behaviors. ABA emphasizes observable behaviors, measurement of behavior change, and the use of interventions in various settings like classrooms an
0 views • 25 slides
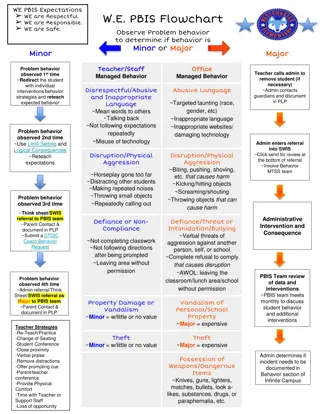
PBIS Expectations and Behavior Flowchart
The PBIS flowchart outlines behavior expectations and interventions for minor and major incidents in a school setting. It covers disrespectful behavior, disruption, defiance, property damage, theft, possession of weapons, and more. The flowchart guides teachers and staff on managing and addressing s
0 views • 6 slides
Managing Acting-Out Behavior: A Staff Development Program Review
This review discusses a staff development program created by Geoffrey Colvin, Ph.D., from the University of Oregon, focusing on preventing and managing acting-out behavior in students with emotional disturbance or behavior disorders. The program includes video presentations, strategies for behavior
0 views • 22 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Understanding Organizational Behavior and Individual Behavior
Organizational Behavior (OB) is a multidisciplinary field that combines knowledge from various disciplines to study and manage organizations effectively. It emphasizes the application of this knowledge to enhance organizational effectiveness and the well-being of participants. OB is a useful concept
0 views • 38 slides
Function-Based Behavior Support Plans: A Comprehensive Guide
Explore the process of developing Function-Based Behavior Support Plans (BSP) using Functional Behavioral Assessment (FBA). Understand the concepts of function and functional behavior assessment, learn how FBA/BSP fits within a multi-tiered support system, and practice developing BSP for students. D
0 views • 74 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
MapReduce Method for Malware Detection in Parallel Systems
This paper presents a system call analysis method using MapReduce for malware detection at the IEEE 17th International Conference on Parallel and Distributed Systems. It discusses detecting malware behavior, evaluation techniques, categories of malware, and approaches like signature-based and behavi
0 views • 22 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
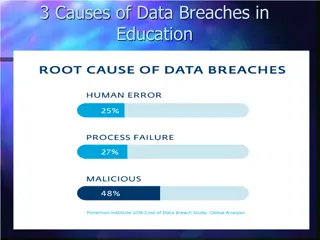
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides