Driving Effectiveness with Direct Mail: Key Insights
Direct mail continues to be a powerful marketing tool, offering personalized, targeted, and impactful campaigns in today's digital world. WARC's research highlights the effectiveness of including direct mail in marketing strategies, driving revenue growth, brand building, and overall campaign succes
1 views • 15 slides
HPE 878643-001 96W Smart Storage Battery for DL/ML/SL G10 Servers
New | HPE 878643-001 | 96W Smart Storage Battery for DL\/ML\/SL G10 Servers | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed
0 views • 1 slides
Advanced Cooling Solutions for Immersion Servers by Asperitas
Asperitas offers an innovative immersion cooling solution for servers, featuring the AIC24-15/19/21 technology with advanced power and compute densities. The integration solution includes power delivery, management, cooling, monitoring, and containment features for optimal performance. Their Shell I
1 views • 19 slides
Enhance Security and Compliance with ADAudit Plus
ADAudit Plus by ManageEngine is a real-time change auditing and reporting software that helps you monitor and secure your Active Directory, Azure AD, Windows servers, file servers, and workstations. It transforms event log data into actionable reports, identifies anomalous activity, and assists in d
0 views • 31 slides
Understanding Email Communication Protocol
Explore the workings of email communication through SMTP, user agents, mail servers, and message queues. Discover the process of sending and receiving emails between users like Alice and Bob, highlighting the role of servers in handling message delivery and retrieval.
0 views • 18 slides
Issues and Algorithms in Server Software Design
The content discusses fundamental issues in server software design such as connectionless vs. connection-oriented access, stateless vs. stateful applications, and iterative vs. concurrent server implementations. Various server algorithms like iterative and concurrent servers are explained with their
3 views • 44 slides
Understanding Internet Tools and Terminology
The Internet is a global network of interconnected computers utilizing the TCP/IP communication method. It includes the World Wide Web, browsers for accessing content, servers for data transfer, websites with webpages displayed via web servers, URLs for addressing resources, and protocols like SMTP,
2 views • 6 slides
Understanding Computer Networks and Servers
Computer networks are groups of connected computers that allow communication and resource sharing. They utilize network media, adapters, operating systems, and protocols. Servers are specialized network computers that provide centralized access to resources like applications, files, and email servic
1 views • 53 slides
Understanding Mail Server Basics from a Linux Operating System Perspective
Dive into the essentials of mail servers, exploring the key components of an email system, such as email clients and servers. Learn how email clients work, the functions they offer, and the role of email servers in managing and routing messages to ensure delivery over the Internet.
0 views • 25 slides
Efficient Mail Distribution and Dispatching Procedures in an Office Setting
Enhance your mail handling skills with this office practice lesson focusing on distributing and dispatching mail internally and externally. Learn to address envelopes, attach enclosures securely, and dispatch mail within deadlines. Discover how to minimize delays, handle missing items, and follow es
0 views • 5 slides
Efficient Mail Distribution and Dispatching Practices in Office Environments
Learn the essential skills required for distributing and dispatching mail efficiently in an office setting. This lesson covers internal and external mail handling procedures, reasons for delays, dispatching mail externally, and using courier services. Understand the importance of timely mail distrib
0 views • 5 slides
Post-COVID-19 Operational Guide for PCR Inc.
The operational guide outlines safety protocols for PCR Inc. post-COVID-19, emphasizing a 50% capacity limit, presence of a certified food manager on-site, adherence to social distancing guidelines, frequent sanitation of high-touch surfaces, and mandatory mask-wearing. Employees are required to wea
2 views • 7 slides
Understanding Concurrent Processing in Client-Server Software
Concurrency in client-server software allows for simultaneous computing, involving multi-user systems, time-sharing, and multiprocessing. This concept is vital in distributed computing, occurring among clients and servers, as well as within networks. Developers design client programs without conside
3 views • 26 slides
Understanding Scanning in Thin Clients, RDP, and Citrix Environments
Learn about the difference between Fat Clients and Thin Clients, various types of Thin Clients, reasons for using Thin Clients, how programs are accessed on servers, and issues with scanning in RDP connections in this informative guide. Discover why Thin Clients are preferred for centralized softwar
1 views • 16 slides
Understanding Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Revolutionizing Data Delivery with Python ADDE Project
Python ADDE Project aims to modernize data delivery infrastructure by developing Python libraries for ADDE server development, enabling easy creation of servers without the need for McIDAS-X knowledge. The initiative seeks to ensure a sustainable future for ADDE in serving new satellite and image da
3 views • 9 slides
Why the Best Dedicated Servers Run on Linux
In the realm of web hosting, dedicated servers stand as the pinnacle of performance, control, and reliability. When it comes to choosing an operating system for these servers, Linux consistently emerges as the top choice for businesses, developers, a
1 views • 11 slides
Understanding Web Hosting and Server Types
Web hosting is a service that enables individuals and organizations to make their websites accessible via the World Wide Web. It provides necessary infrastructure, storage, and connectivity to ensure websites are available to users 24/7. The web hosting process involves domain names, DNS translation
0 views • 9 slides
Fast Crash Recovery in RAMCloud - Overview and Architecture
RAMCloud offers fast crash recovery, low-latency access, and large-scale storage in RAM, addressing the challenge of durability in RAM with a pervasive log structure and disk-based replication. The architecture includes Application Servers, Coordinators, Masters, Backups, and Storage Servers to ensu
0 views • 36 slides
Raft Consensus Algorithm Overview for Replicated State Machines
Raft is a consensus algorithm designed for replicated state machines to ensure fault tolerance and reliable service in distributed systems. It provides leader election, log replication, safety mechanisms, and client interactions for maintaining consistency among servers. The approach simplifies oper
0 views • 32 slides
Server Design Alternatives - A Comprehensive Overview
Exploring various server design alternatives such as preforked servers, threaded servers, prethreaded servers, sequential servers, and multiplexed servers. Discussing their implementations, efficiency, limitations, and potential combinations for optimal performance.
1 views • 12 slides
Understanding DNS Replication with BIND9
Explore the intricacies of DNS replication using BIND9, including the role of authoritative name servers, the importance of serial numbers, and the process of data transfer between master and slave servers. Discover insights on maintaining consistency in zone data to ensure smooth DNS operations.
2 views • 39 slides
Effective Method to Protect Web Servers Against Breach Attacks
Abdusamatov Somon presents an effective method called HTB to protect web servers against breach attacks, focusing on secure computation and mitigation. The research addresses side-channel attacks based on compression and the CRIME BREACH issue, providing insights into implementing the breach attack
1 views • 13 slides
Discussion on Provisioning Servers Addressing Information in 3GPP TS 23.501
Background CT4 LS in S2-2200200 issue 2 discussed the interpretation and intention of the addressing information for Provisioning Servers (PVS) as stated in 3GPP TS 23.501. The focus was on whether the provided PVS IP addresses and/or FQDNs are for a single PVS server or multiple servers and how the
0 views • 4 slides
Fault-tolerant and Load-balanced VuFind Project Overview
Project Background: Part of the National Digital Library initiative, the VuFind project aims to provide a discovery interface for Finnish archives, libraries, and museums. It started development in 2012 due to the insufficiency of existing commercial products. The focus is on enhancing fault toleran
1 views • 19 slides
Understanding SMTP - Simple Mail Transfer Protocol
SMTP (Simple Mail Transfer Protocol) is a fundamental component of the application layer in computer networks. It is used for sending electronic mail messages between servers and user agents. The process involves user agents composing messages, connecting to mail servers, and transferring messages o
0 views • 29 slides
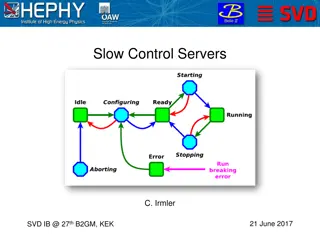
Slow Control Servers and Network Configuration for SVD Management
The documentation discusses the setup and requirements for slow control servers, network configuration, FADC server status, ENV server status, and general SC server status for SVD management. It outlines the need for backup servers, minimum server requirements, server specifications, procurement det
0 views • 11 slides
The Power of Direct Mail in Influencing Influencers
Direct mail has a significant impact on influencers, with up to 80% believing that it can change their opinion of a company or brand. While most people are receivers of influencer content, influencers themselves are influenced by mail more than the average. Mail helps in creating cut-through and hel
0 views • 6 slides
Unlock 20% Postage Credits with First-Time User Incentive for Advertising Mail
Discover the exclusive First-Time User Incentive for Advertising Mail by Royal Mail, offering 20% postage credits on up to 1m items posted in a 12-month period. This opportunity is ideal for businesses looking to leverage mail for advertising, providing a substantial reward for first-time users or t
0 views • 10 slides
Guidelines for Using Mail Ballots and Returning Them
In this guide, you will find instructions on using mail-in ballots and envelopes to cast your vote. Remember to verify with the Secretary of State's office. Ensure you have received all necessary items in the mail, and if anything is missing, contact the provided office number. After voting, mail yo
0 views • 6 slides
Understanding Client-Server Paradigm in Distributed Systems
Client-server paradigm in distributed systems involves structuring systems as collaborating processes where clients request services from servers. The model follows a request/reply protocol, with servers providing centralized control of shared resources. Advantages include security and simplicity, w
1 views • 30 slides
Understanding Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
0 views • 7 slides
Understanding Client-Server Computing in Distributed Systems
Client-server interaction forms the foundation of distributed computing, where clients rely on servers to perform operations. Clients can be various applications like browsers, email clients, and office software, while servers manage network resources and serve specific functions such as file storag
0 views • 17 slides
Minimum Direct Connections to Achieve Simultaneous Access
In a computer science laboratory with 15 workstations and 10 servers, the minimum number of direct connections needed to ensure that any set of 10 or fewer workstations can simultaneously access different servers is determined using the Generalized Pigeonhole Principle. By strategically connecting w
0 views • 5 slides
Understanding Email Technologies and Infrastructure
Explore the intricacies of email technologies, infrastructure, and architecture, including the format of HTTP messages, the role of proxy servers, creating web servers, and key components of email systems like user agents, mail servers, and SMTP protocol. Delve into email protocols like SMTP, POP3,
0 views • 38 slides
Minnesota County Election Administration Training Conference Overview
The 2022 County Election Administration Training Conference focuses on mail ballot precincts and mail elections. The agenda covers changes in processing mail ballots, polling place operations on Election Day, history of mail elections, and resources for mail voting. Details include authorizing mail
0 views • 62 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Understanding the Architecture of the World Wide Web
The World Wide Web (WWW) is a vast repository of information accessible through a distributed client-server system. Users interact with web pages hosted on servers through browsers, utilizing URLs to navigate between different sites. This system consists of clients (browsers) and servers, where clie
0 views • 44 slides
Analyzing Break-In Attempts Across Multiple Servers using Apache Spark
Exploring cyber attacks on West Chester University's servers by analyzing security logs from five online servers using Apache Spark for large-scale data analysis. Uncovering attack types, frequency patterns, and sources to enhance security measures. Discover insights on break-in attempts and potenti
0 views • 19 slides
Mail Specification and Processing Changes Effective September 2024
This document outlines changes in the processing of out-of-specification mail, starting from September 2nd, 2024. Mail pieces that do not meet specified requirements will undergo manual sortation or less efficient processing, potentially incurring additional charges. Reasons for introducing these ch
0 views • 16 slides