Enhancing Wi-Fi Relay Networks for Improved Coverage and Reliability
This document discusses the need to enhance relay frameworks in Wi-Fi networks to improve coverage, reliability, and performance of stations in different ranges. It highlights the challenges of S1G-based relays, proposes enhancements to the relay framework, and introduces new types of relay framewor
1 views • 12 slides
Proposed Approach for MAC Address Assignment in IEEE 802.11
IEEE 802.1CQ is working on a mechanism to assign local MAC address blocks to end nodes specifically related to IEEE 802.11 standards. The current draft lacks a pre-association mechanism for IEEE 802.11 stations to obtain a local MAC address before association. The proposed remedy suggests specifying
6 views • 7 slides
Understanding Relay, Optoisolator, and Stepper Motor Interfacing with 8051 Microcontroller
Explore the fundamentals of relays, optoisolators, and stepper motors along with their interfacing with the 8051 microcontroller. Learn about relay characteristics, operation, optoisolator linking, and stepper motor control through programming examples in Assembly and C.
21 views • 28 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
Understanding the 5V Relay Module and Its Applications
A 5V relay module is an electrically activated switch commonly used in switching circuits for home automation projects, controlling heavy loads, safety circuits, and automotive electronics. This small relay board works with a 5V signal and can handle up to 10A of current for both AC and DC loads. It
1 views • 7 slides
Comprehensive Guide to Transformer Buchholz Relay by Prof. V. G. Patel
Understanding the significance of Buchholz relay in protecting transformers from incipient faults that can develop into serious issues. Developed by Max Buchholz in 1921, this gas-operated device detects faults such as core insulation failure, short-circuited core laminations, and loss of oil due to
3 views • 14 slides
Considerations for Relay Operation in Next Generation Wi-Fi Networks
In this document, considerations and use cases for relay operation in next generation Wi-Fi networks are discussed. The authors provide insights into the improvements in reliability and throughput, focusing on the benefits of relay features in various scenarios such as smart home devices and automot
0 views • 11 slides
Fun Team Relay Games for Physical Education
Engage in exciting and interactive team relay games like Locomotor Relay, Long Jump Relay, Crab Walk Relay, Over/Under Relay, and V-Sit Relay. These activities promote teamwork, coordination, and physical fitness in a fun and engaging way. Set up cones, form teams, and enjoy these dynamic relay chal
0 views • 6 slides
Enhancing Communication: The Role of Relay Services for Individuals with Hearing or Speech Disabilities
Explore the importance of telephone communication for individuals with hearing or speech disabilities, and how relay services facilitate communication through text transcription. Learn about the speed of transcription, VCO services, and the basic method of communication that is often taken for grant
0 views • 18 slides
Evolution of Relay Services for Deaf and Hard of Hearing Individuals
The history of relay services for the deaf and hard of hearing dates back to the 1960s in the USA. Three pioneering deaf men played a significant role in establishing the first successful deaf telephone network, leading to the development of relay services as we know them today. This evolution enabl
0 views • 29 slides
Relay Communications for Ultra High Reliability in IEEE 802.11-22/1908r1
Investigating relay communications to enhance Rate-vs-Range (RvR) performance for Ultra High Reliability (UHR) in IEEE 802.11-22/1908r1. The content explores relay design objectives, goodput analysis, existing relay solutions like WiFi extenders, and the challenges in implementing relay technology t
3 views • 16 slides
Understanding Electrical Relays and Contactors
An electrical relay is a magnetic switch that utilizes electromagnetism to control contacts. Relays consist of a coil and contacts insulated from each other, with different types like normally open (NO) and normally closed (NC) contacts. Contactors, a specialized type of relay, handle heavy power lo
2 views • 43 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
Understanding Wide Area Networking Using Frame Relay Cloud
The field of networking is advancing rapidly, with technologies like cloud computing relying on robust wide area networking. This presentation explores the use of Frame Relay Cloud in improving the security and configuration complexities faced in interconnecting wide area networks. It discusses the
0 views • 16 slides
Enhancing Internet Telephony Quality Through Predictive Relay Selection
Examining the quality of Internet telephony in relation to network performance, this research explores the use of Managed Overlay to improve call quality for services like Skype. Analysis of 430 million Skype calls reveals that a significant portion experience poor network performance, emphasizing t
1 views • 26 slides
Privacy Issues in IEEE 802.11 Networks: Tracking and MAC Randomization
This presentation delves into the privacy concerns surrounding 802.11 networks, focusing on tracking vulnerabilities and the limitations of MAC randomization in preventing tracking. It discusses the ease of tracking devices, the risk of passive tracking due to MAC addresses being visible in frames,
0 views • 27 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
IEEE 802.11-23/1899r0 Relay Operation for 11bn - Presentation Summary
In this presentation, the IEEE 802.11-23/1899r0 document discusses relay operations to improve Rate-vs-Range (RvR) performance for UHR. Various potential solutions for implementing a relay protocol in UHR are explored, focusing on enhancing multi-hop channel access delay, end-to-end QoS, and simplif
0 views • 10 slides
Considerations for Relay Operation in Next-Gen Wi-Fi Networks
This presentation discusses the considerations and features for relay development in next-generation Wi-Fi networks, focusing on improving coverage in dead zones, enhancing throughput, and reducing energy consumption. It explores concepts like multi-traffic multiplexing in relay transmission and pow
0 views • 9 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
Implications of IEEE 802.11 State Machine and MAC Randomization
The document discusses the state machine transitions in IEEE 802.11, focusing on MAC address handling and implications for STA connectivity within an ESS. It explains the scenarios where a STA can use different MAC addresses, emphasizing the binding of state to specific address configurations and th
0 views • 11 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
Understanding Relay Logic and Circuits
Explore the world of relay logic and circuits with detailed explanations, images, and practical examples. Learn about basic relays, labeling, simple relay logic circuits, sump pump relay circuit, NAND burglar alarm, and various relay logic gates (AND, OR, NAND, NOR). Dive into the functioning of rel
0 views • 17 slides
How to Record Your Voice: A Comprehensive Guide for Windows, Mac, and Smartphones
Learn how to record your voice for ePoster, MP3, or podcasts using Windows 10, Mac, Android, or iPhone/iPad devices. Find step-by-step instructions for recording on different platforms, including using Windows Voice Recorder on a Windows 10 computer and QuickTime Player on a Mac. Discover tips for a
1 views • 10 slides
IEEE 802.11-24/0386r0 Lower MAC Relay Protocol Details
Detailed discussion on supporting the relay protocol in IEEE 802.11bn, covering relay addressing, end-to-end BA, relay TXOP protection, beacon forwarding, security processing, non-UHR STA support, sounding procedure, A-MPDU aggregation, de-aggregation, and more. The relay operation involves relay de
0 views • 16 slides
Exploring Mac OS & VoiceOver: A Comprehensive Guide with Belinda Rudinger
Dive into the world of Mac OS and VoiceOver with expert Belinda Rudinger in this detailed tutorial. Learn about screen readers, VoiceOver commands, built-in features, interaction tools, customization options, and useful utilities. Discover how to navigate the Mac ecosystem seamlessly using VoiceOver
0 views • 20 slides
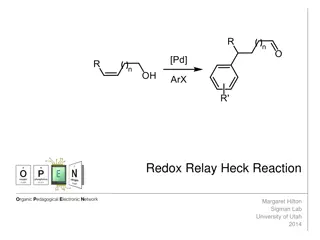
Understanding the Redox-Relay Heck Reaction in Organic Synthesis
The Redox-Relay Heck Reaction is a powerful tool in organic synthesis that allows for the functionalization of olefins with aryl groups. Developed by Sigman and colleagues, this reaction involves a palladium-catalyzed relay controlled by a thermodynamic sink, leading to the formation of aldehydes or
0 views • 6 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
0 views • 25 slides
The Migration Advisory Committee Review and Findings
The Migration Advisory Committee (MAC) is an independent advisory body formed in 2007 to provide recommendations to the government on migration issues. The MAC does not create or implement policy but advises through research and analysis in various areas like economics, education, and stakeholder en
0 views • 13 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
Energy Efficient Relay Antenna Selection for AF MIMO Two-Way Relay Channels
The study explores energy-efficient relay antenna selection for AF MIMO two-way relay channels, aiming to optimize energy efficiency while maintaining performance. It discusses the advantages and disadvantages of two-way MIMO relay systems, emphasizing higher spectral efficiency, improved reliabilit
0 views • 17 slides
Caseous Mitral Valve Calcification (C-MAC) and Stroke: Overview and Management
Caseous Mitral Valve Calcification (C-MAC) is a rare condition characterized by spectrum liquefaction necrosis of the mitral annular calcification (MAC), potentially leading to cardiovascular complications like strokes and emboli. This article discusses the features, diagnostic aspects, and treatmen
0 views • 7 slides
Enhancing MAC Header Protection in IEEE 802.11 Networks
This document discusses the need for improved protection of MAC headers in IEEE 802.11 networks to address security concerns related to certain fields that are currently not adequately protected. It emphasizes the importance of safeguarding vital information in MAC headers to prevent potential attac
0 views • 12 slides
IEEE 802.11-22/0424r1 - MAAD MAC Protocol Overview
The document discusses the MAAD MAC protocol, where the AP assigns a MAAD MAC address to the STA during association. Key differences from other schemes are highlighted, emphasizing the use of MAAD MAC addresses as identification. Details on support indication, address allocation, and recognition mec
0 views • 7 slides
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
IEEE 802.11-23/0421r1: Understanding the IRM Scheme for MAC Address Privacy
The document discusses the use of the Same MAC Address (SMA) scheme in IEEE 802.11-23/0421r1 and introduces the Improved Randomized MAC (IRM) scheme as a privacy-enhancing solution. It explores the implementation and benefits of IRM over SMA, addressing issues like privacy requirements, device ident
0 views • 7 slides
Enhancement of Rule-based Random and Changing MAC Proposal in IEEE 802.11-22/1802r0
This document details the enhancements proposed for the Rule-based Random and Changing MAC (RRCM) in IEEE 802.11-22/1802r0. The RRCM concept involves generating Random MAC (RMA) addresses locally to increase security and prevent trackability in wireless networks. Key aspects include RMA generation,
0 views • 12 slides
MAC Address Randomization in IEEE 802.11: Privacy Concerns and Solutions
The document discusses the rise of MAC randomization in IEEE 802.11 networks, addressing motivations, benefits, concerns over privacy implications, and real-life scenarios highlighting the risks associated with passive observation of MAC addresses. It emphasizes the importance of safeguarding privac
0 views • 14 slides