Understanding Narcotic Analgesics and Opiates: History, Mechanisms, and Uses
Delve into the world of narcotic analgesics and opiates, exploring the history of opium poppy, morphine derivatives, opioid compounds, and the pharmacology mechanisms of action. Discover the uses of opiates in analgesia, preanesthetic medication, and more, alongside the endogenous ligands involved.
8 views • 55 slides
Advancements in Chemical Mechanisms for Air Quality Management
Daniel Jacob and team have been enhancing chemical mechanisms in the GEOS-Chem model to support US air quality management. Ongoing work includes developing new mechanisms for aromatic VOCs, tropospheric halogens, mercury redox, adaptive mechanism reduction, machine learning applications, and unifica
0 views • 19 slides
Understanding Isolation and Virtualization in Operating Systems
This text delves into the concepts of isolation and virtualization in operating systems. It covers topics such as virtual memory, virtual machines, containers, and kernel isolation mechanisms like chroot and cgroups. The discussion explores how these techniques provide isolation between processes, c
5 views • 20 slides
Understanding AARCH64 Linux Kernel Memory Management
Explore the confidential and proprietary details of AARCH64 Linux kernel memory mapping, virtual memory layout, variable configurations, DDR memory layout, and memory allocation techniques. Get insights into the allocation of physically contiguous memory using Continuous Memory Allocator (CMA) integ
0 views • 18 slides
Kinematics of Machines: Instantaneous Center Method for Velocity and Acceleration Analysis
Explore the method of locating instantaneous centers in mechanisms to analyze velocity and acceleration. The content covers examples of pin-jointed four-bar mechanisms and slider-crank mechanisms, providing dimensions and angular velocities calculations. Prof. Divyesh B. Patel from L.E. College, Mor
0 views • 13 slides
Understanding Plasmid Partitioning Mechanisms in Bacteria
The stable maintenance of low-copy-number plasmids in bacteria relies on partition mechanisms that ensure proper positioning during cell division. Different from high-copy-number plasmids, which rely on random diffusion, low-copy-number plasmids require regulated partitioning mechanisms to prevent d
0 views • 14 slides
Understanding Metabolic Control Mechanisms in Cellular Regulation
Metabolic control mechanisms play a crucial role in maintaining homeostasis within cells by regulating metabolic pathways. This involves finely adjusting the output of pathways in response to external signals, ensuring the proper flux of metabolites to meet cellular needs. Pacemaker enzymes, such as
1 views • 17 slides
Overview of Organic Reactions and Mechanisms
Organic reactions can be categorized into addition, elimination, and substitution reactions, occurring through either polar or free radical mechanisms. Polar reactions may be electrophilic or nucleophilic, while free radical reactions involve radicals reacting to complete electron octets. Different
2 views • 26 slides
Understanding Prezygotic Reproductive Isolating Mechanisms
Prezygotic reproductive isolating mechanisms prevent mating or fertilization between different species before it can occur. Examples include habitat isolation, behavioral isolation, and temporal isolation. These mechanisms play a significant role in maintaining species integrity and preventing the f
0 views • 4 slides
Understanding Generalized Discriminant Analysis (GDA) in Pattern Recognition
Generalized Discriminant Analysis (GDA) is a nonlinear form of Linear Discriminant Analysis (LDA) that utilizes kernel methods to find discriminatory features for optimal class separability. LDA aims to maximize the between-class covariance matrix while minimizing the within-class covariance matrix.
2 views • 17 slides
Fuel Pricing Mechanisms and Regulatory Framework Presentation
This presentation to the Portfolio Committee on Mineral Resources and Energy delves into the Basic Fuel Price (BFP) for liquid fuels, covering global fuel pricing forms, policy positions, key pricing mechanisms, regulatory mandates, and the intricate structure behind fuel prices. It explains how the
2 views • 28 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
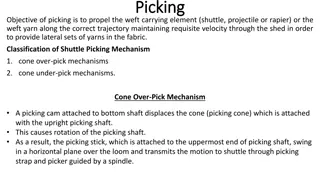
Understanding Shuttle Picking Mechanisms in Weaving
Shuttle picking mechanisms play a crucial role in propelling the weft carrying element to maintain the required trajectory and velocity in fabric weaving. Two common mechanisms are cone over-pick and cone under-pick, each offering unique adjustments for strength and timing. The cone over-pick involv
0 views • 14 slides
Exploring Defense Mechanisms in Personality Structure
In "Understanding Personality Structure in the Clinical Process" by Nancy McWilliams, various defense mechanisms are illustrated through real-life examples. These mechanisms include primitive withdrawal, denial, omnipotent control, idealization and devaluation, and projection with projective identif
1 views • 29 slides
Understanding Kernel Tricks in Machine Learning
Kernel tricks in machine learning involve transforming inputs into higher-dimensional spaces to make linear models work for nonlinear data. Kernels can be applied to various algorithms like SVM, ridge regression, and more, allowing for better model performance with complex datasets.
0 views • 15 slides
Fundamentals of Operating Systems Explained
Explore the core concepts of operating systems, including kernel-userspace interactions, system calls, context switching, and virtual memory management. Delve into x86 assembly for system calls, hardware interrupts, and the flow of control during system call invocations. Gain insights into key compo
7 views • 19 slides
Understanding the Inversion of Mechanisms in Kinematics
Inversion of Mechanisms in Kinematics involves measuring absolute and relative motions in stationary and moving frames, respectively. By fixing different links in a kinematic chain, we can obtain various mechanisms. This process does not alter relative motions but may significantly change absolute m
0 views • 78 slides
Improving the Reliability of Commodity Operating Systems
This research paper discusses the challenges and solutions in enhancing the reliability of commodity operating systems by addressing system failures caused by kernel extensions. The Nooks approach isolates extensions within protection domains, allowing them to reside in the kernel address space with
0 views • 40 slides
Raspberry Pi 2 Boot Process Overview
Raspberry Pi 2's boot process involves a series of stages initiated by the GPU, loading essential firmware and enabling hardware components gradually, leading to the activation of the CPU and the kernel's entry point. The system transitions through various low-level processes before reaching a stabl
0 views • 9 slides
Safeguarding Focal Point Training: Enhancing Reporting and Response Mechanisms
This training module focuses on empowering Safeguarding Focal Points (SFPs) to understand and implement community-based feedback and response mechanisms, effectively handle safeguarding complaints, document barriers to reporting, address data protection issues, and ensure inclusive and confidential
0 views • 18 slides
Understanding Authentication Mechanisms and Security Vulnerabilities
Authentication lies at the core of application security, serving as the primary defense against malicious attacks. This article explores various authentication technologies, including HTML forms-based authentication, multi-factor mechanisms, client SSL certificates, and more. It delves into common d
0 views • 70 slides
Overview of UNIX System Protection
UNIX System Protection focuses on ensuring security and access control mechanisms within the UNIX operating system. Developed in 1969 by Dennis Ritchie and Ken Thompson at AT&T Bell Labs, UNIX features design elements like a portable API, protection rings, kernel processes, and a trusted computing b
0 views • 12 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Understanding User Mode, Kernel Mode, Interrupts, and System Calls in Computer Architecture
In modern computers following Von Newman Architecture, programs and data are stored in RAM. The CPU, RAM, ROM, and devices communicate via address and data buses. The system operates in both kernel and user modes, where kernel mode allows full system control, while user mode restricts access for sec
0 views • 29 slides
Tracing Network Packets in Linux Kernel with eBPF
This presentation discusses the challenges of troubleshooting modern networking systems and proposes a solution using eBPF technology to trace the path of network packets in the Linux kernel. The goal is to develop a tool that provides detailed information about how network packets are processed in
0 views • 16 slides
Understanding Exceptional Control Flow in Computer Systems
Control flow mechanisms in computer systems have evolved to handle exceptional events triggered by external system states. This includes exceptions, interrupts, and context switches that enable the CPU to respond to events like data arrival, user inputs, and system timeouts. Exception handling invol
0 views • 66 slides
Overview of Human Rights Monitoring Mechanisms
Human rights conventions under the United Nations and regional systems have established monitoring mechanisms to ensure compliance. These mechanisms include treaty-based and non-treaty-based approaches, with treaty bodies overseeing the implementation of legally binding instruments. Reporting proced
0 views • 23 slides
Improved Truthful Mechanisms for Subadditive Combinatorial Auctions
This research paper discusses strategies to maximize welfare in combinatorial auctions. It explores mechanisms for handling strategic bidders with private valuations, aiming to design truthful and optimal welfare mechanisms while considering polytime constraints. The study presents advancements in a
0 views • 19 slides
Analyzing Multimodality in Density Distributions Using JMP Scripting
Explore variability sources hidden in density distributions through JMP scripting. The analysis focuses on identifying and filtering distribution modes in semiconductor fab electrical measurements using kernel estimation and empirical rules. Antonio D'Angelo and Felice Russo from Lfoundry S.r.l. Ita
0 views • 6 slides
Understanding Remote Procedure Call (RPC) in Different Kernel Environments
Communication through Remote Procedure Call (RPC) plays a crucial role in facilitating seamless interaction between server and client processes, whether on the same machine or across different kernels. This technology streamlines local and cross-domain communication, optimizing performance while ens
0 views • 9 slides
Overview of the Pintos Instructional Operating System Kernel Project
Description of the Pintos Operating System Kernel project, including its use in educational settings at institutions such as Stanford University and Virginia Tech. The project aims to provide students with a hands-on experience in OS design, focusing on the internal workings of the kernel. Pintos fe
0 views • 33 slides
Understanding Pipes in Process Communication
Pipes in process communication allow for high-throughput data transfer between parent and child processes. The kernel creates a communication stream through file descriptors, enabling one process to send data to another. Processes can use pipes for efficient inter-process communication, with the ker
1 views • 15 slides
Understanding Biomarkers and Toxicity Mechanisms: Overview of Mechanisms in Targeting Biological Macromolecules
This overview delves into different categorizations of mechanisms of action (MoA) based on target molecules, interaction types, and steric specificity. It explores non-specific and specific mechanisms, along with possible categorizations involving membrane toxicity, reactive toxicity, and species-sp
0 views • 8 slides
Understanding User and Kernel Modes in Operating Systems
The content provided discusses various aspects of user and kernel modes in operating systems through a set of true/false questions related to user programs, CPU interrupts, heap management, and process behavior in different modes. It touches on the role of the kernel in managing virtual memory, hand
0 views • 10 slides
Understanding Coping Skills and Defense Mechanisms
Coping mechanisms and defense mechanisms are strategies individuals use to manage stress and emotions. Coping mechanisms help people adjust to difficult events while maintaining emotional well-being, whereas defense mechanisms operate at an unconscious level and can change internal psychological sta
0 views • 18 slides
Defense Mechanisms in Psychology: Understanding Repression, Displacement, Intellectualization, Rationalization
Defense mechanisms play a crucial role in how individuals cope with stress and anxiety. This text delves into key defense mechanisms such as repression, displacement, intellectualization, and rationalization. These mechanisms help individuals manage unacceptable thoughts, feelings, and impulses by r
0 views • 11 slides
Hyper-Parameter Tuning for Graph Kernels via Multiple Kernel Learning
This research focuses on hyper-parameter tuning for graph kernels using Multiple Kernel Learning, emphasizing the importance of kernel methods in learning on structured data like graphs. It explores techniques applicable to various domains and discusses different graph kernels and their sub-structur
0 views • 20 slides
Overview of UNIX and Linux Operating Systems
The UNIX brand encompasses a range of powerful multitasking, multiuser operating systems used by various organizations to develop IT technologies. UNIX internals consist of kernel space and user space, with programs accessing system services rather than hardware directly. The Unix filesystem is a ke
0 views • 36 slides
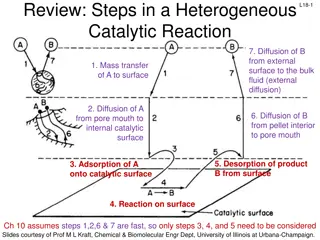
Understanding Steps in Heterogeneous Catalytic Reactions and Adsorption Mechanisms
This review discusses the steps involved in a heterogeneous catalytic reaction, focusing on diffusion, mass transfer, adsorption, and desorption processes. It details the site balance, surface reaction mechanisms, and desorption steps, providing insights into the complexities of catalytic processes.
0 views • 17 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides